Microsoft Defender Portal Access Restored After Traffic Surge Disruption On December 2, 2025, Microsoft faced a significant service disruption affecting the Microsoft Defender portal, a […]
Year: 2025
DevilsTongue Spyware Targets Global Windows Users: A Cybersecurity Challenge
Candiru’s DevilsTongue Spyware: A Global Threat to Windows Users In the ever-evolving landscape of cyber threats, a new and formidable adversary has emerged: DevilsTongue, a […]
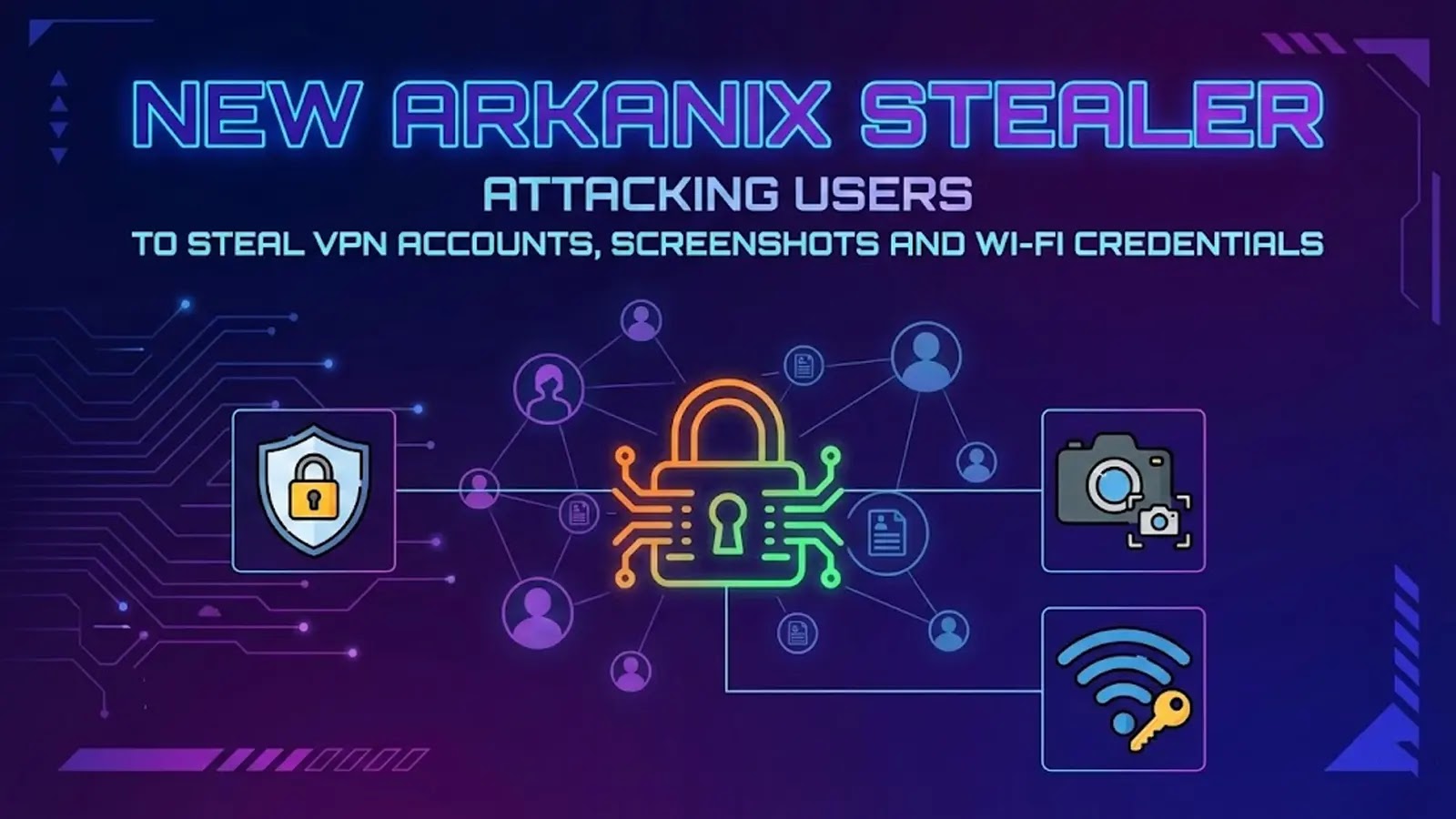
Arkanix Stealer Malware Targets VPNs and Wi-Fi Credentials in New Cybersecurity Threat
Arkanix Stealer: The New Cyber Threat Targeting VPNs, Wi-Fi Credentials, and More A new malware strain, known as Arkanix Stealer, has emerged as a significant […]
Investigation Exposes Lazarus Group’s Sophisticated Recruitment Tactics and Attack Methods
Unveiling Lazarus Group’s Recruitment Tactics: A Live Investigation In a groundbreaking investigation, cybersecurity experts from BCA LTD, ANYRUN, and NorthScan have provided an unprecedented look […]
Security Breach in SmartTube App for Android TV: Users Advised to Uninstall and Monitor Devices
Security Breach in SmartTube App for Android TV: Users at Risk The Android TV community is currently grappling with a significant security breach involving SmartTube, […]
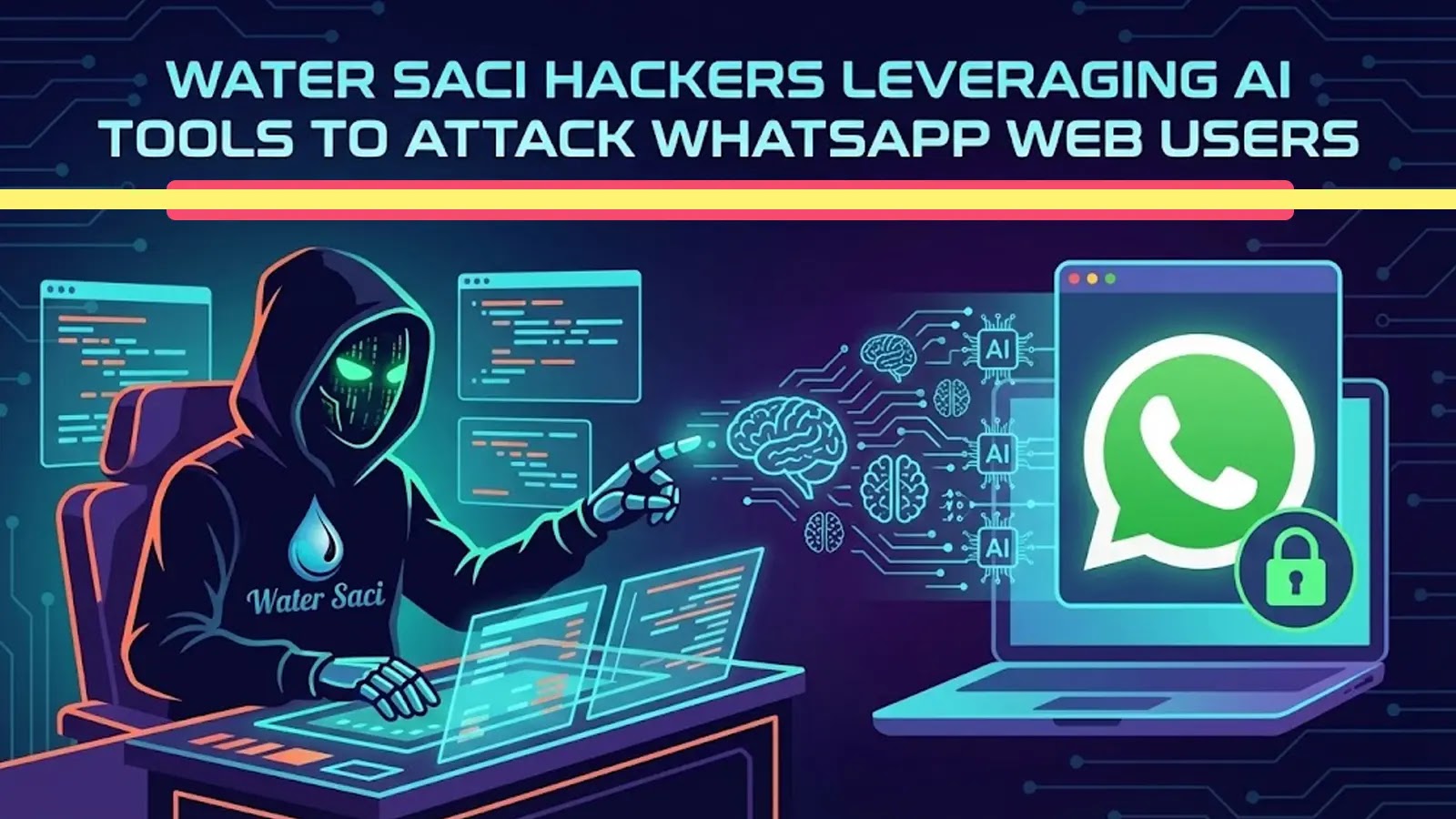
AI-Driven WhatsApp Web Attacks Target Brazilian Users with Sophisticated Malware Campaign Water Saci
Water Saci Hackers Exploit AI to Launch Sophisticated Attacks on WhatsApp Web Users In a concerning development, cybercriminals have intensified their efforts by launching a […]
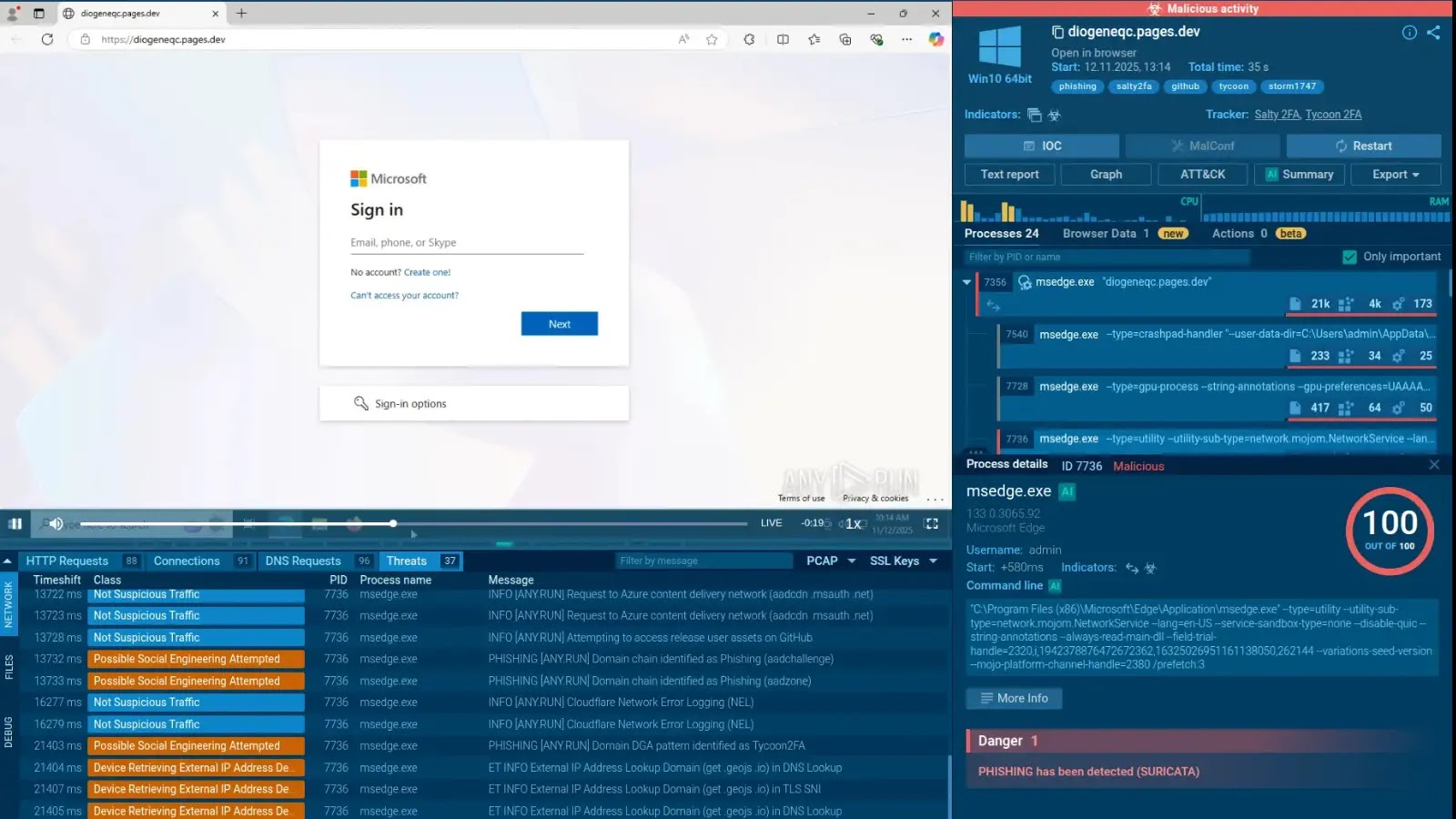
Hybrid Phishing Kits Salty2FA and Tycoon2FA Target Enterprises, Evade Multi-Factor Authentication
Emerging Threat: Salty2FA and Tycoon2FA Phishing Kits Target Enterprise Credentials In the ever-evolving landscape of cyber threats, a new and sophisticated phishing attack has emerged, […]
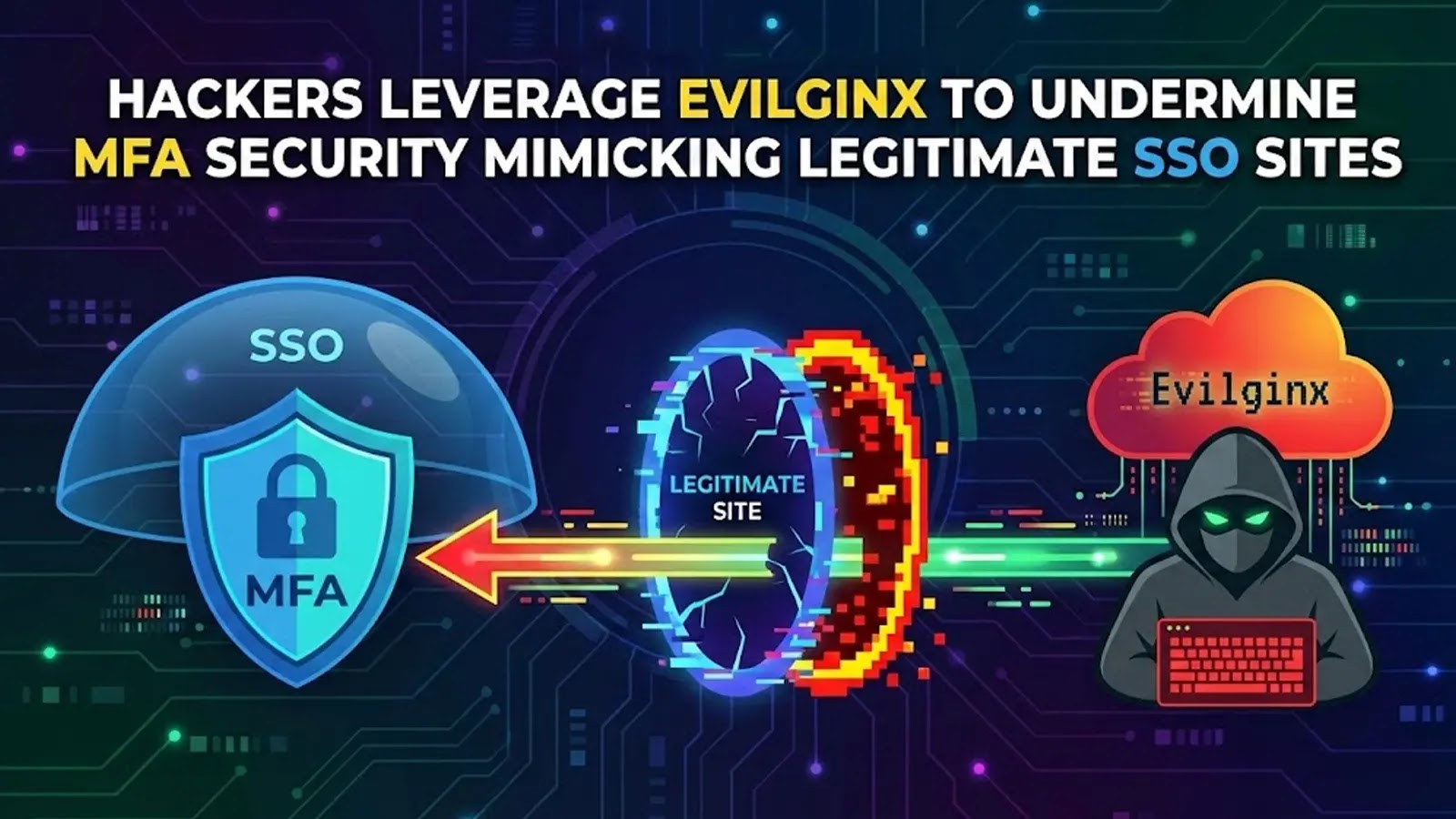
Hackers Exploit Evilginx to Bypass MFA, Hijack Cloud Accounts in Sophisticated Phishing Attacks
Hackers Exploit Evilginx to Bypass Multi-Factor Authentication and Hijack Cloud Accounts In a concerning development, cybercriminals are increasingly utilizing Evilginx, an advanced adversary-in-the-middle (AitM) tool, […]
Ukrainian Hackers Launch Cyber Attacks on Russian Aerospace and Defense Sectors
Ukrainian Cyber Offensive Targets Russian Aerospace and Defense Sectors In a significant escalation of cyber warfare, Ukrainian-affiliated hackers have intensified their attacks on Russian aerospace […]
Early Detection of Insider Threats: Detecting Anomalies in Authentication and Access Patterns
Unveiling Insider Threats: Early Detection Through Authentication and Access Anomalies In today’s digital landscape, insider threats pose a significant challenge to organizational security. Unlike external […]