India Mandates Active SIM Card Requirement for Messaging Apps to Combat Cyber Fraud In a decisive move to bolster cybersecurity and curb digital fraud, India’s […]
Year: 2025
India Mandates ‘Sanchar Saathi’ Cybersecurity App on All Smartphones, Raises Privacy Concerns
India Enforces Mandatory ‘Sanchar Saathi’ Cybersecurity App on All Smartphones In a decisive move to bolster national cybersecurity, India’s Department of Telecommunications (DoT) has mandated […]
Critical Vulnerabilities Patched in OpenVPN; Users Urged to Update for Enhanced Security
Critical OpenVPN Vulnerabilities Expose Systems to Attacks OpenVPN, a widely utilized open-source VPN solution, has recently addressed several critical vulnerabilities that could have allowed attackers […]
ShadyPanda Cyber-Espionage Compromises 4.3M Chrome, Edge Users Over Seven Years
ShadyPanda’s Seven-Year Stealth: How 4.3 Million Chrome and Edge Users Were Compromised In a meticulously orchestrated cyber-espionage campaign spanning seven years, the threat group known […]
Google Urges Immediate Action: Critical Updates Released for Android Zero-Day Exploits Affecting Millions
Google Releases Urgent Security Updates to Address Actively Exploited Android Zero-Day Vulnerabilities Google has issued critical security updates to rectify multiple zero-day vulnerabilities affecting Android […]
Critical Apache Struts Flaw CVE-2025-64775 Allows Disk Exhaustion Attacks; Urgent Updates Needed
Critical Apache Struts Vulnerability Exposes Systems to Disk Exhaustion Attacks A significant security vulnerability has been identified in Apache Struts, a widely used open-source framework […]
New USB Cable Hack Tool: Evil Crow Cable Wind Enables Stealth Attacks and Remote Control
Evil Crow Cable Wind: The Charging Cable That Can Hack Your Device In the ever-evolving landscape of cybersecurity threats, a new device has emerged that […]
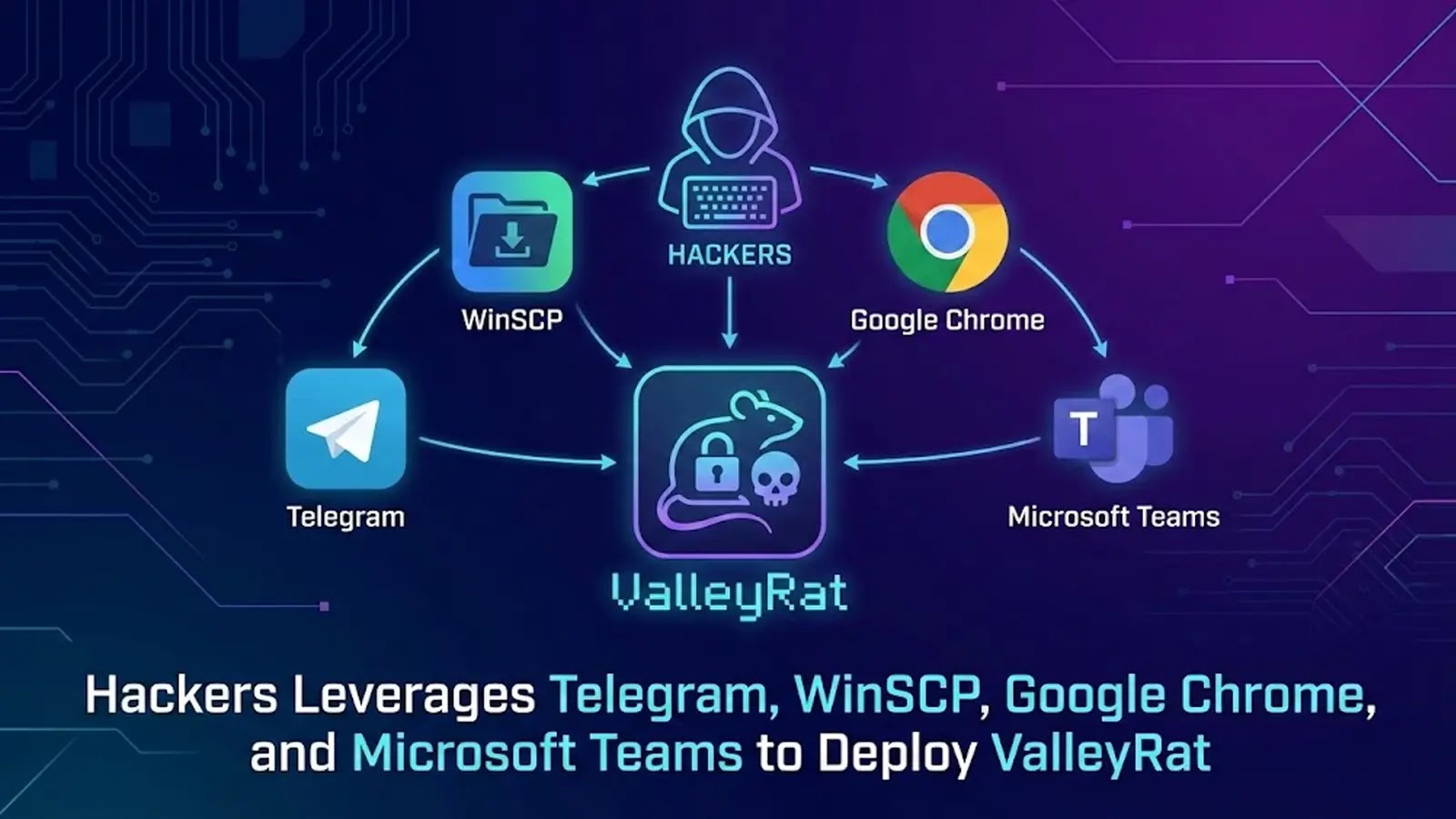
Silver Fox APT Targets Popular Apps to Spread ValleyRAT Malware through Spear-Phishing and Malicious Ads
Cybercriminals Exploit Popular Apps to Deploy ValleyRAT Malware A recent cybersecurity investigation has uncovered a sophisticated malware campaign that leverages trusted applications to distribute ValleyRAT, […]
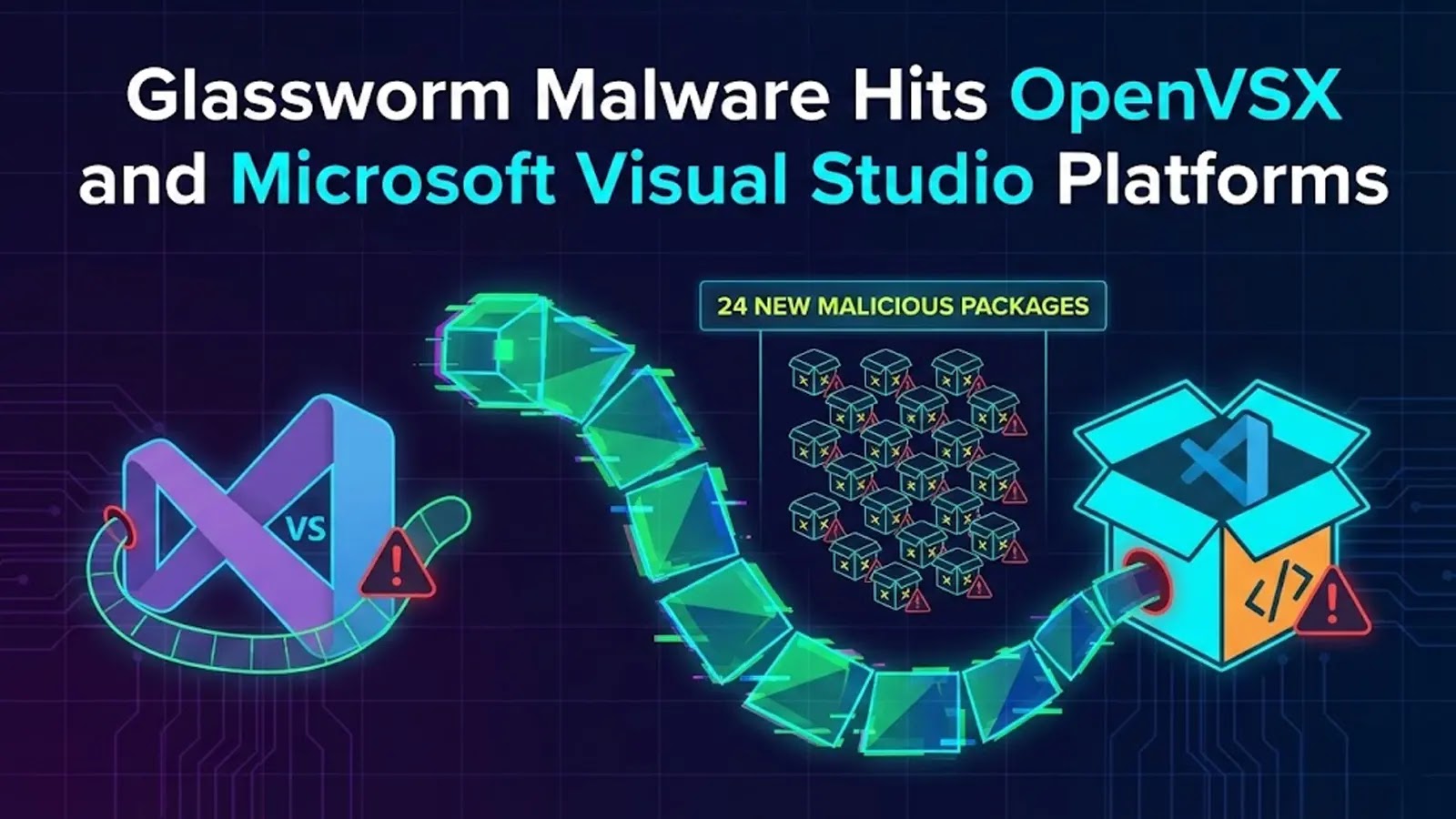
GlassWorm Malware Returns: 24 Malicious Extensions Target Visual Studio and OpenVSX Platforms
GlassWorm Malware Resurfaces: 24 Malicious Extensions Target OpenVSX and Microsoft Visual Studio The GlassWorm malware campaign has re-emerged with alarming intensity, deploying 24 malicious extensions […]
Raspberry Pi 5 Launches at $45, Offering Affordable High-Performance Computing
Raspberry Pi 5: Affordable High-Performance Computing Now More Accessible The Raspberry Pi Foundation has unveiled the Raspberry Pi 5 with 1GB RAM, priced at an […]