Critical Use-After-Free Vulnerability in Linux Kernel’s POSIX CPU Timers Exposed A significant security flaw, identified as CVE-2025-38352, has been discovered in the Linux kernel’s implementation […]
Month: December 2025
BlindEagle Executes Complex Cyberattack on Colombian Commerce Ministry, Advances Fileless Malware Tactics
BlindEagle’s Advanced Cyber Assaults on Colombian Government Agencies In September 2025, the South American cyber threat group known as BlindEagle launched a sophisticated attack targeting […]
Malicious NPM Package ‘Lotusbail’ Steals WhatsApp Data from 56,000 Developers Worldwide
Malicious NPM Package ‘lotusbail’ Compromises WhatsApp Data of 56,000 Developers A recently discovered malicious npm package named lotusbail has been found to steal WhatsApp messages […]
Hacktivist Group Scrapes 86 Million Tracks in Massive Spotify Data Breach
Hacktivist Group Scrapes 86 Million Spotify Tracks in Unprecedented Data Breach In a bold and controversial move, the shadow library known as Anna’s Archive has […]
Cybercriminals Use ClickFix and Steganography to Hide Malware in Images, Evading Detection
Cybercriminals Exploit ClickFix and Steganography to Conceal Malware in Images In a concerning development, cybercriminals have combined the deceptive ClickFix social engineering technique with advanced […]
Critical Vulnerability in Digiever NVRs Actively Exploited, CISA Urges Immediate Patching
Critical Vulnerability in Digiever DS-2105 Pro Network Video Recorders Actively Exploited On December 22, 2025, the Cybersecurity and Infrastructure Security Agency (CISA) added a critical […]
Hackers Hijack Nezha Monitoring Tool for Undetectable Remote System Access, Experts Warn
Article Title: Cybercriminals Exploit Nezha Monitoring Tool for Stealthy Remote Access In a concerning development, cybersecurity experts at Ontinue’s Cyber Defense Center have identified that […]
Malicious Chrome VPN Extensions Phantom Shuttle Steal User Credentials; Users Urged to Uninstall Immediately
Beware: Malicious Chrome VPN Extensions Stealing User Credentials In a concerning development, two deceptive Chrome extensions named Phantom Shuttle have been masquerading as legitimate VPN […]
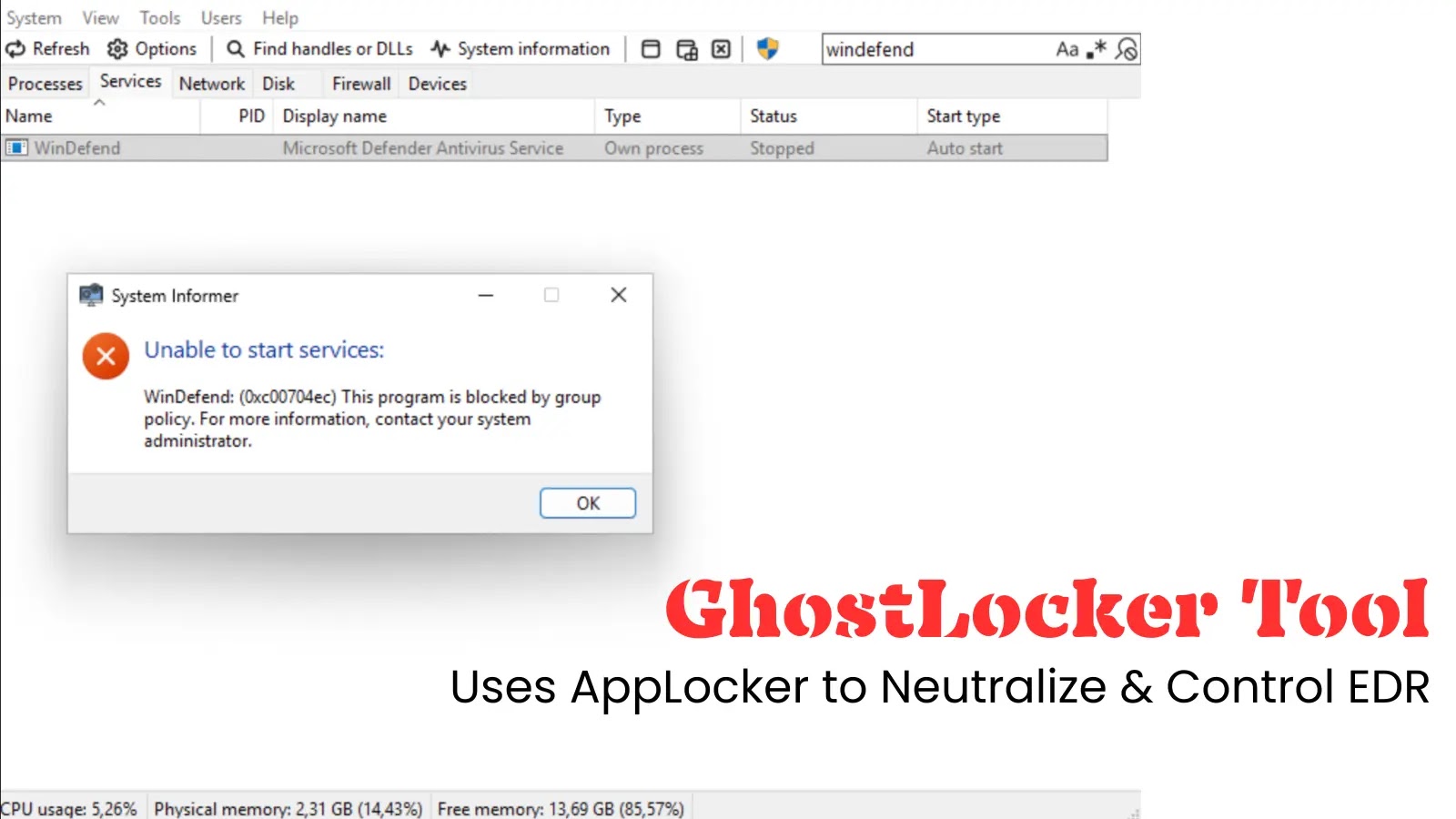
GhostLocker Exploits Windows AppLocker to Neutralize EDR Systems, Highlights Critical Flaw
GhostLocker: Exploiting Windows AppLocker to Disable EDR Systems A groundbreaking tool named GhostLocker has emerged, showcasing a novel method to disable Endpoint Detection and Response […]
Critical Flaw in HPE OneView Allows Remote Code Execution; Patch Urgently Recommended
Critical HPE OneView Vulnerability Exposes Enterprises to Remote Code Execution A critical security flaw has been identified in Hewlett Packard Enterprise’s (HPE) OneView platform, a […]