Recent investigations have uncovered that numerous mobile applications are inadvertently exposing sensitive user data due to misconfigured Google Firebase services. These misconfigurations allow unauthorized access […]
Month: September 2025
Critical Vulnerability in NVIDIA Merlin Transformers4Rec Library Enables Remote Code Execution with Root Privileges
A significant security flaw has been identified in NVIDIA’s Merlin Transformers4Rec library, designated as CVE-2025-23298. This vulnerability allows unauthenticated attackers to execute arbitrary code remotely […]
Volvo Group North America Addresses Data Breach Stemming from Third-Party Ransomware Attack
Volvo Group North America has recently informed its employees and associates about a data breach that resulted in the exposure of personal information, including names […]
Critical Cisco IOS and IOS XE Vulnerability Allows Remote Authentication Bypass and Data Exposure
A significant security flaw has been identified in Cisco’s IOS and IOS XE software, potentially enabling unauthenticated remote attackers to circumvent authentication mechanisms and access […]
ColdRiver APT Group Exploits ClickFix Technique to Deploy Malware
In recent developments, cybersecurity experts have identified a sophisticated campaign orchestrated by the ColdRiver Advanced Persistent Threat (APT) group. This campaign leverages the deceptive ClickFix […]
BRICKSTORM: A Stealthy Backdoor Targeting Technology and Legal Sectors
In mid-2025, cybersecurity experts identified a sophisticated backdoor malware named BRICKSTORM, which has been targeting organizations within the technology and legal industries. This malware exploits […]
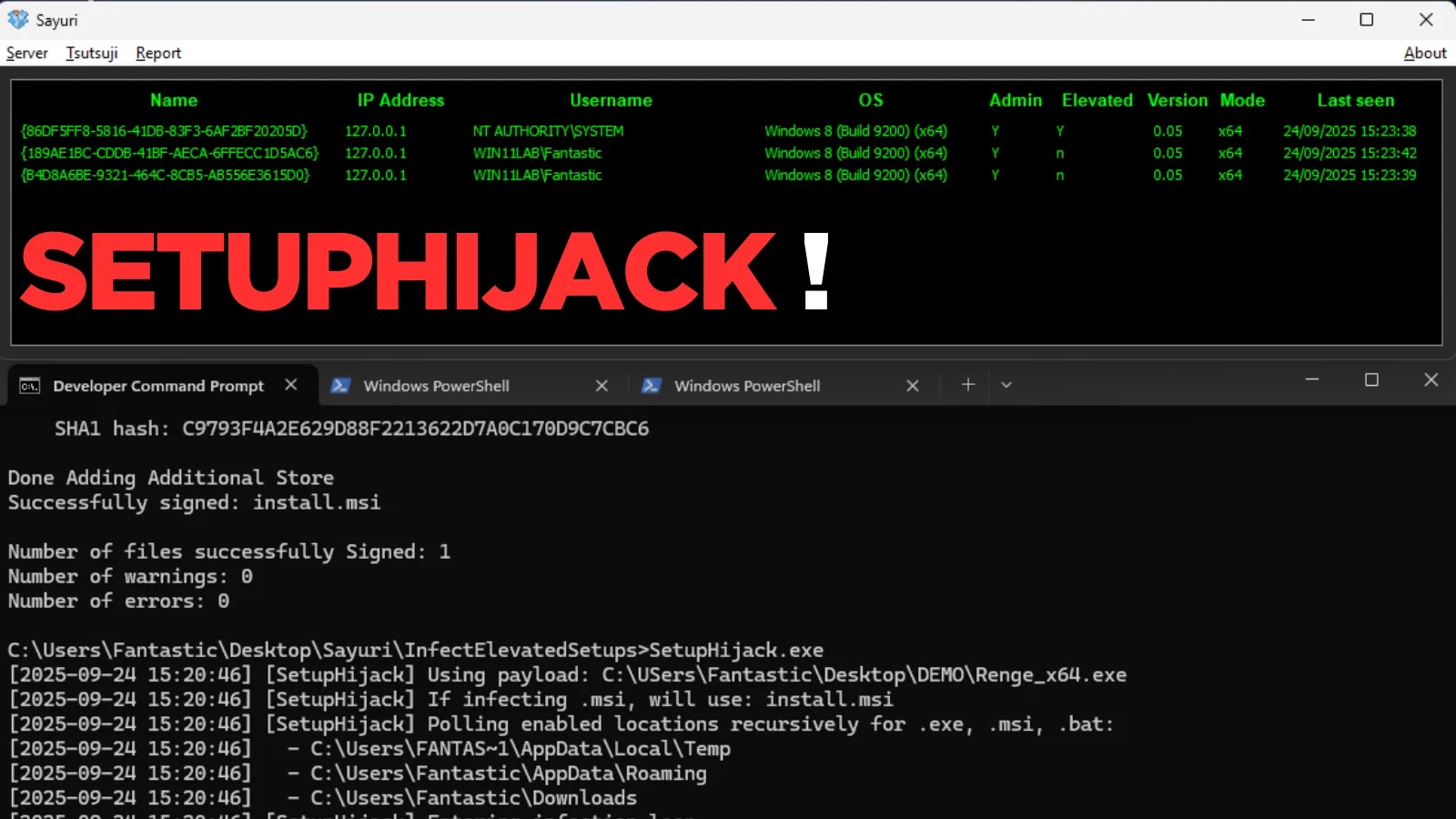
SetupHijack Tool Exploits Race Conditions and Insecure File Handling in Windows Installer Processes
SetupHijack is an open-source research utility designed to exploit vulnerabilities in Windows installer and update mechanisms, specifically targeting race conditions and insecure file handling. This […]
Critical Path Traversal Vulnerability in ZendTo Exposes Sensitive Data
A significant security flaw has been identified in ZendTo, a widely used web-based file transfer application. This vulnerability, designated as CVE-2025-34508, allows authenticated users to […]
LockBit 5.0 Ransomware: A New Cross-Platform Threat Targeting Windows, Linux, and ESXi Systems
In September 2025, the notorious LockBit ransomware group unveiled its latest iteration, LockBit 5.0, marking a significant evolution in its cyberattack capabilities. This release underscores […]
Apple’s Response to iPhone 17 Pro ‘Scratchgate’ Sparks Debate Over Device Durability
The recent release of Apple’s iPhone 17 Pro has been overshadowed by a growing controversy dubbed Scratchgate, with users reporting that the device’s aluminum frame […]