On September 19, 2025, Collins Aerospace, a subsidiary of RTX Corporation, experienced a ransomware attack targeting its Multi-User System Environment (MUSE) passenger processing software. This […]
Month: September 2025
Cisco’s SNMP Vulnerability: A Critical Threat to Network Security
Cisco has recently disclosed a critical zero-day vulnerability, designated as CVE-2025-20352, within its widely utilized IOS and IOS XE software platforms. This flaw resides in […]
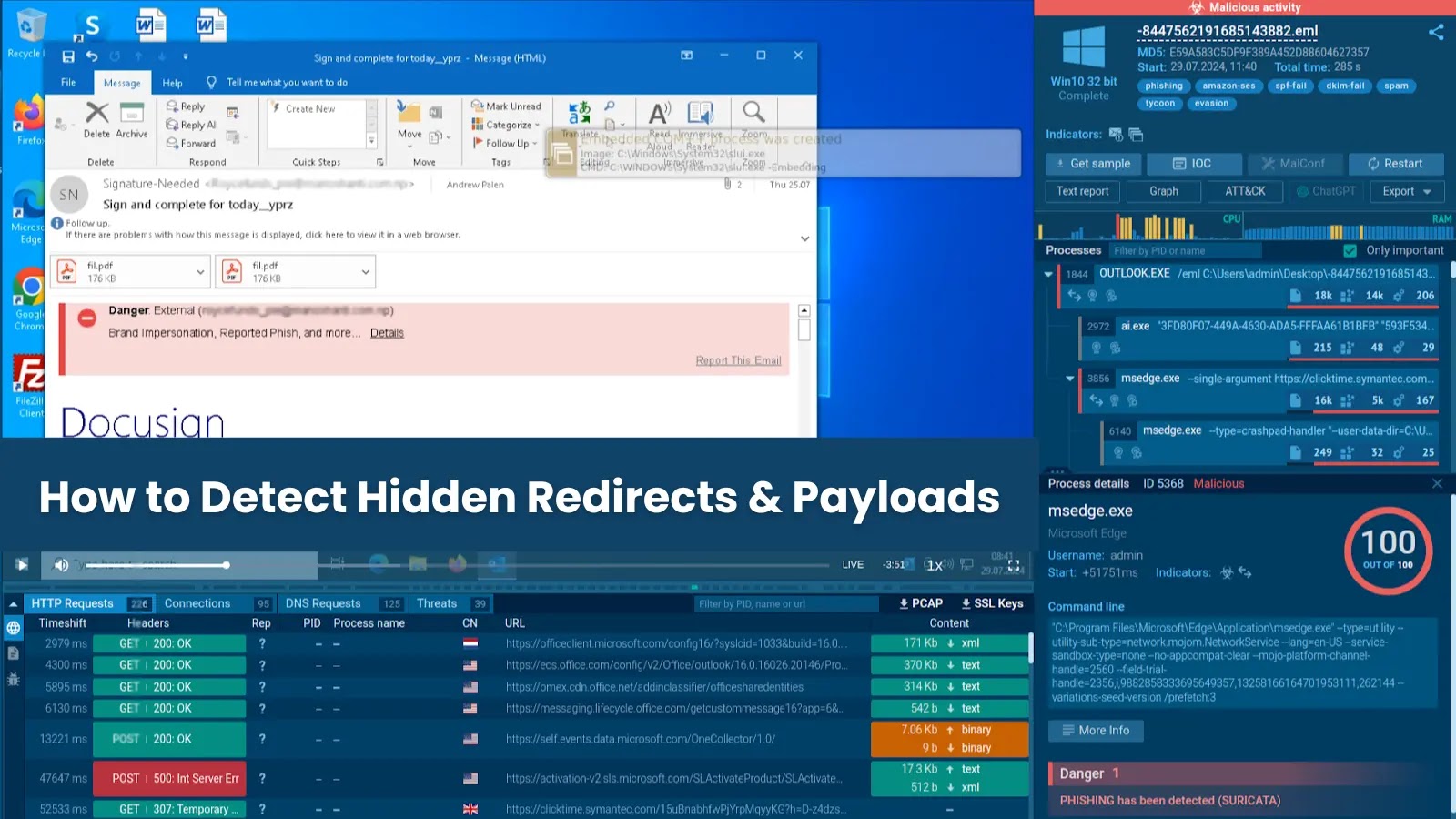
Unmasking Malicious SVGs in Phishing Campaigns: Detecting Hidden Redirects and Payloads
Phishing attacks have evolved, employing increasingly sophisticated methods to deceive users and bypass security measures. A recent tactic involves the use of Scalable Vector Graphics […]
Critical Vulnerability in DNN Platform’s Prompt Module Enables Malicious Script Execution
A significant security flaw has been identified in the DotNetNuke (DNN) Platform, a widely utilized content management system (CMS). This vulnerability, designated as CVE-2025-59545, carries […]
Banking Trojans Masquerade as Government and Payment Apps to Target Android Users
A sophisticated cybercriminal campaign has been identified, targeting Android users in Indonesia and Vietnam. This operation involves banking trojans disguised as legitimate government identity applications […]
Critical Vulnerability in Linux Kernel’s KSMBD Service Enables Remote Code Execution
A significant security flaw has been identified in the Linux kernel’s KSMBD (Kernel SMB Daemon) service, potentially allowing authenticated remote attackers to execute arbitrary code […]
Critical Vulnerabilities in Supermicro BMC Firmware Enable Attackers to Bypass Signature Verification
Recent investigations have uncovered significant vulnerabilities in Supermicro’s Baseboard Management Controller (BMC) firmware, revealing that previous security patches were insufficient. These flaws allow attackers to […]
Hackers Exploit Hikvision Camera Vulnerability to Access Sensitive Information
A critical security flaw in Hikvision surveillance cameras, initially identified in 2017, is currently being actively exploited by cybercriminals to gain unauthorized access to sensitive […]
Russian-Backed Disinformation Campaign Targets Moldova’s Upcoming Elections
As Moldova approaches its parliamentary elections on September 28, 2025, cybersecurity experts have identified a sophisticated disinformation campaign orchestrated by Russian entities. This operation aims […]
Exploiting Trust: How Attackers Use Domain Fronting with Google Services to Conceal Malicious Traffic
In today’s digital landscape, organizations heavily rely on services like Google Meet, YouTube, Chrome update servers, and Google Cloud Platform (GCP) to maintain seamless operations. […]