In a recent cybersecurity development, threat actors affiliated with the Democratic People’s Republic of Korea (DPRK) have been identified utilizing the ClickFix social engineering technique […]
Day: September 22, 2025
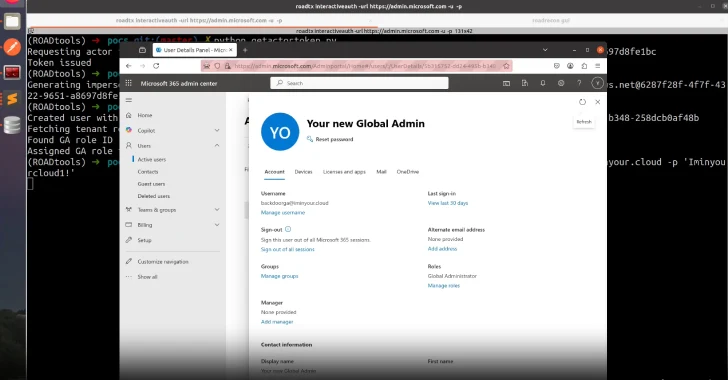
Microsoft Addresses Critical Entra ID Vulnerability Allowing Global Admin Impersonation Across Tenants
Microsoft has recently patched a critical vulnerability in its Entra ID (formerly Azure Active Directory) that could have permitted attackers to impersonate any user, including […]
Securing AI Agents and Non-Human Identities: A Comprehensive Guide
In today’s digital landscape, enterprises are increasingly reliant on non-human identities (NHIs) such as service accounts, API tokens, and AI agents. These entities operate autonomously, […]
Tech Giants Advise H-1B Visa Holders to Remain in the U.S. Amid New Policy Changes
In response to recent policy shifts affecting the H-1B visa program, leading technology companies such as Amazon, Google, and Microsoft have issued advisories to their […]
Cyberattack Disrupts Major European Airports, Causing Widespread Flight Delays
Over the weekend of September 20-21, 2025, a significant cyberattack targeted Collins Aerospace’s MUSE (Multi-User System Environment) software, a critical component in airline check-in and […]
Silicon Valley’s Strategic Investment in AI Training Environments
In recent years, the tech industry has been captivated by the potential of artificial intelligence (AI) agents—autonomous systems capable of performing tasks traditionally handled by […]
Cybersecurity Weekly Recap: Major Breaches, Emerging Threats, and Critical Vulnerabilities
In the past week, the cybersecurity landscape has been marked by significant incidents, including major data breaches, the emergence of sophisticated threats, and the discovery […]
Sophisticated Cyber-Attack Targets macOS Users via GitHub Pages to Deploy Atomic Stealer Malware
A recent cyber-attack campaign has been identified, exploiting GitHub Pages to distribute the Atomic Stealer (AMOS) malware to macOS users. This operation employs advanced Search […]
Cybercriminals Exploit Malicious Scripts and Phishing Tactics to Compromise Industrial Control Systems
In the first half of 2025, industrial automation systems have increasingly become prime targets for sophisticated cybercriminals. These adversaries are deploying malicious scripts and phishing […]
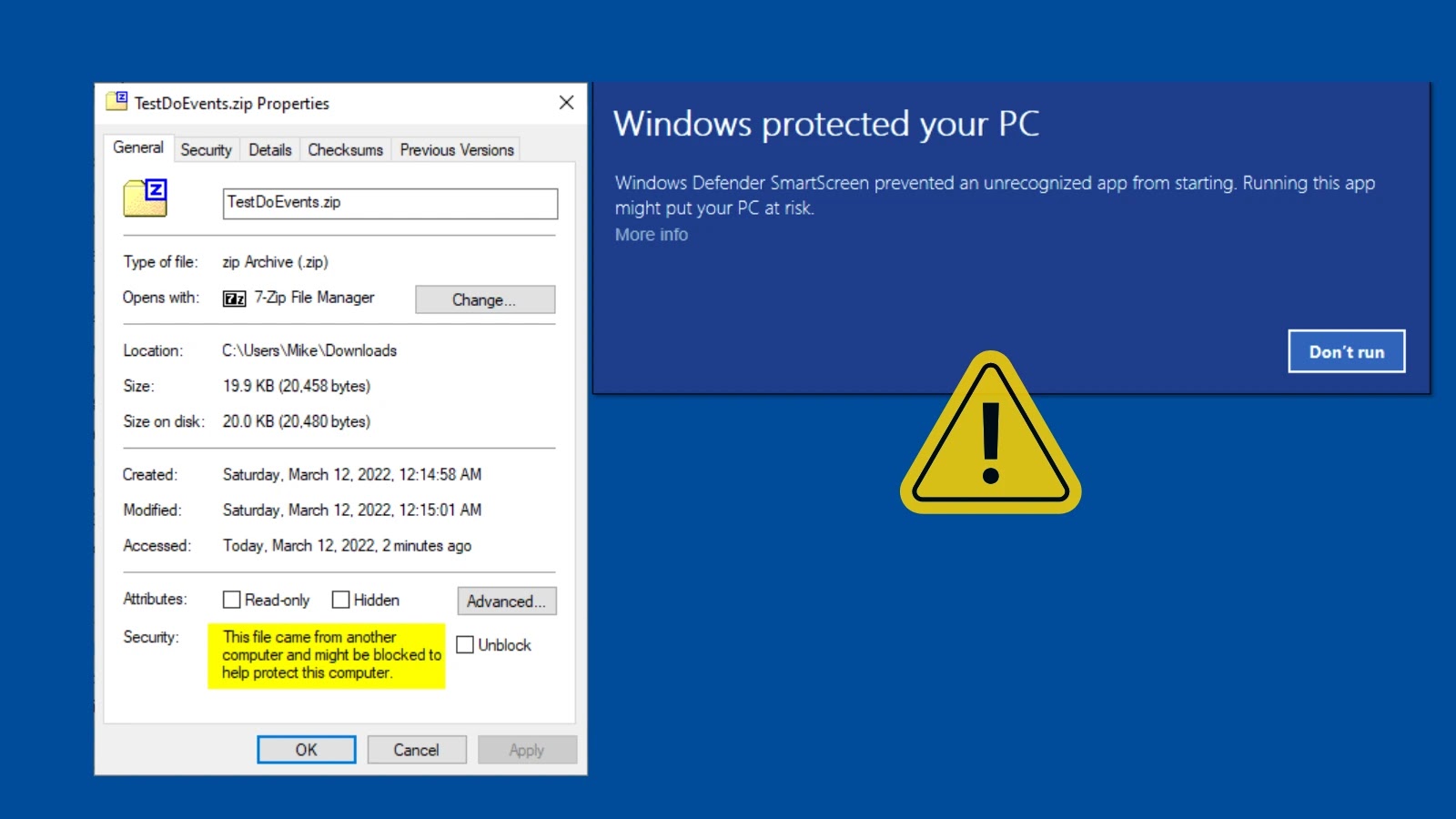
Hackers Exploit Windows LNK Stomping to Bypass Security Measures
A sophisticated cyberattack technique known as LNK Stomping has emerged as a significant threat to Windows security. This method exploits inherent flaws in how the […]