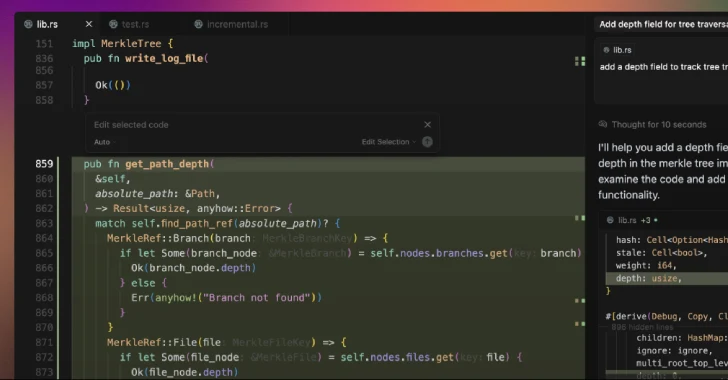
A significant security vulnerability has been identified in Cursor, an AI-powered code editor, which could enable the execution of arbitrary code when a developer opens […]
Day: September 12, 2025
Cloud-Native Security in 2025: The Imperative of Runtime Visibility
The evolution of cloud-native applications has significantly transformed the security landscape. Technologies such as containers, Kubernetes, and serverless computing have become standard in modern enterprises, […]
Critical Vulnerability in DELMIA Apriso Exploited: CISA Issues Urgent Advisory
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently added a critical security vulnerability, identified as CVE-2025-5086, to its Known Exploited Vulnerabilities (KEV) catalog. […]
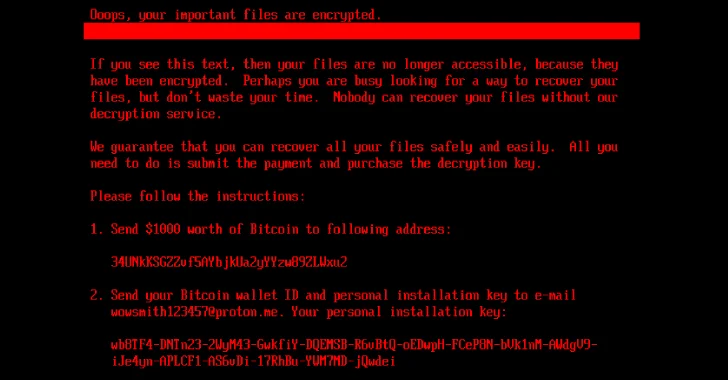
HybridPetya Ransomware Exploits UEFI Vulnerability to Evade Secure Boot
Cybersecurity experts have identified a new ransomware variant named HybridPetya, which mirrors the infamous Petya and NotPetya malware strains. This sophisticated ransomware can circumvent the […]
Apple Alerts Users to New Spyware Threats: French Cybersecurity Agency Confirms Notifications
In a recent development, Apple has issued notifications to several users, informing them that their devices may have been compromised by spyware. This action has […]
Gmail Enhances Package Tracking with New ‘Purchases’ Tab
Google has introduced a significant update to Gmail, unveiling a Purchases tab designed to streamline the management of package deliveries. This new feature consolidates all […]
FTC Initiates Investigation into AI Chatbot Companions from Leading Tech Firms
The Federal Trade Commission (FTC) has launched an inquiry into seven prominent technology companies—Alphabet, Character Technologies, Instagram, Meta Platforms, OpenAI, Snap, and xAI—regarding their development […]
Apple Issues Multiple Spyware Threat Notifications to French Users in 2025
In early September 2025, Apple initiated a new series of threat notifications to French users, alerting them to potential targeting by commercial spyware. This marks […]
Critical Vulnerability in DELMIA Apriso Factory Software Exploited in Active Attacks
A critical security vulnerability has been identified and actively exploited in DELMIA Apriso, a manufacturing operations management (MOM) and manufacturing execution system (MES) software developed […]
Threat Actors Exploit Open-Source AdaptixC2 Framework in Sophisticated Cyber Attacks
In May 2025, cybersecurity experts observed a significant uptick in cyber attacks utilizing AdaptixC2, an open-source command-and-control (C2) framework originally designed for penetration testing. This […]