In recent years, cybercriminals have increasingly exploited Remote Monitoring and Management (RMM) tools to gain unauthorized access to corporate systems. These tools, originally designed to […]
Month: August 2025
Scattered Spider: Evolution of a Cyber Threat – New Tactics and Techniques in 2025
Scattered Spider, also known by aliases such as UNC3944, Octo Tempest, 0ktapus, Muddled Libra, and Scatter Swine, has rapidly evolved into one of the most […]
Critical Zero-Day Vulnerabilities in Adobe AEM Forms: Immediate Action Required
Adobe has recently issued an urgent security update for its Adobe Experience Manager (AEM) Forms on Java Enterprise Edition (JEE) to address two critical zero-day […]
Microsoft’s Project Ire: Pioneering Autonomous Malware Detection with AI
In a significant advancement for cybersecurity, Microsoft has introduced Project Ire, an autonomous artificial intelligence (AI) agent designed to detect and classify malware without human […]
Chinese State-Sponsored Hackers Exploit SharePoint Vulnerabilities to Deploy Advanced Malware Toolset
In a recent cybersecurity development, Chinese state-sponsored hacking groups have been actively exploiting critical vulnerabilities in Microsoft SharePoint servers to deploy a sophisticated malware suite […]
Chinese Cybercriminals Exploit Digital Wallets in Massive U.S. Payment Card Fraud
Between July 2023 and October 2024, a sophisticated Chinese cybercriminal syndicate orchestrated one of the most extensive payment card fraud operations in history, potentially compromising […]
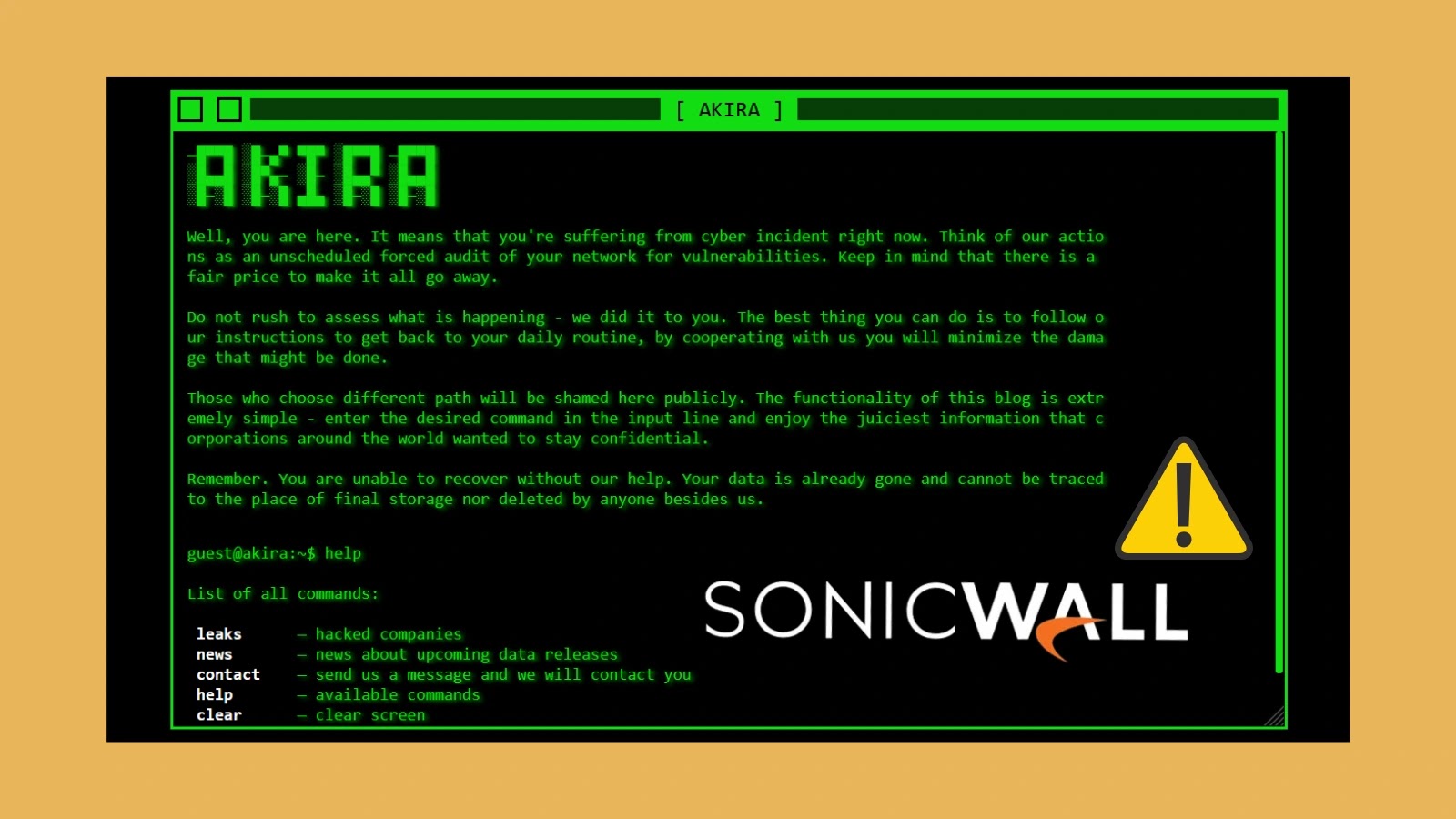
Akira Ransomware Exploits Windows Drivers to Evade Detection in SonicWall VPN Attacks
In recent cybersecurity developments, the Akira ransomware group has demonstrated advanced evasion techniques by exploiting legitimate Windows drivers to bypass antivirus (AV) and endpoint detection […]
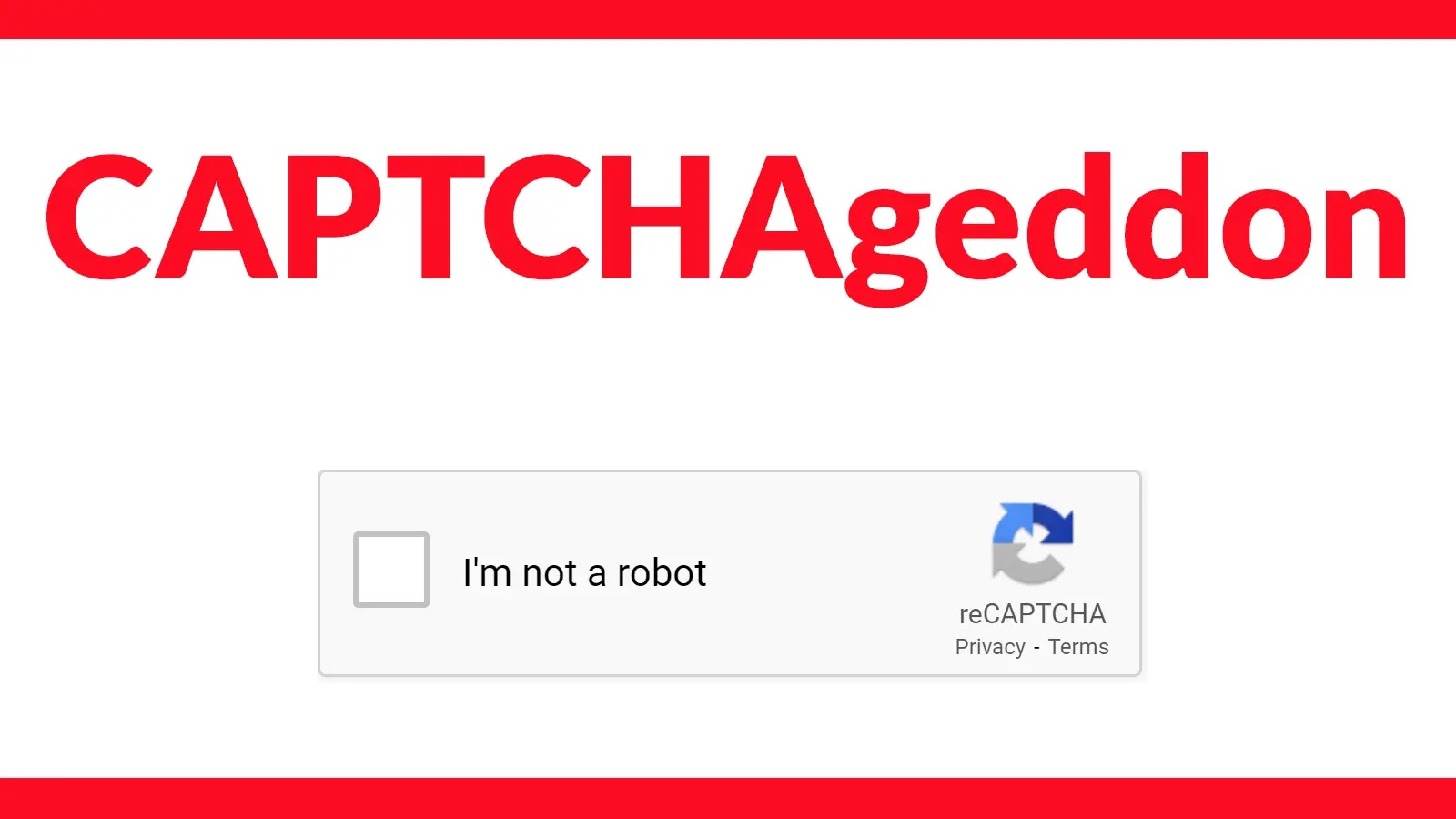
CAPTCHAgeddon: The Rise of ClickFix Attacks Exploiting Fake CAPTCHAs to Deploy Malware
In the ever-evolving landscape of cyber threats, a new and sophisticated malware campaign has emerged, leveraging fake CAPTCHA verification pages to deceive users into executing […]
Unveiling DevilsTongue: The Sophisticated Windows Spyware Targeting Users Globally
In recent years, the cybersecurity landscape has been significantly impacted by the emergence of advanced spyware tools designed to infiltrate and monitor high-profile targets worldwide. […]
Critical Vulnerabilities in Rockwell Arena Simulation Software Enable Remote Code Execution
Rockwell Automation has recently disclosed three critical vulnerabilities in its Arena® Simulation software, identified as CVE-2025-7025, CVE-2025-7032, and CVE-2025-7033. These flaws, affecting versions 16.20.09 and […]