A Chrome VPN extension, FreeVPN.One, boasting over 100,000 installations and a verified badge on the Chrome Web Store, has been identified as sophisticated spyware. This […]
Month: August 2025
Critical RCE Vulnerability in CodeRabbit’s Production Servers Exposed Over 1 Million Repositories
In December 2024, a critical remote code execution (RCE) vulnerability was identified within CodeRabbit’s production infrastructure, potentially granting unauthorized access to more than one million […]
Paper Werewolf Exploits WinRAR Zero-Day Vulnerability to Deploy Malware
In July 2025, cybersecurity experts identified a sophisticated cyberattack campaign orchestrated by the threat actor group known as Paper Werewolf, also referred to as GOFFEE. […]
Exploitation of Apache ActiveMQ Vulnerability CVE-2023-46604 in Cloud-Based Linux Systems
A sophisticated cyberattack campaign has been identified, wherein adversaries are exploiting a critical remote code execution (RCE) vulnerability in Apache ActiveMQ, designated as CVE-2023-46604, to […]
Serial Hacker Sentenced for Global Cyber Attacks and Website Defacements
In a significant crackdown on international cybercrime, 26-year-old Al-Tahery Al-Mashriky from Rotherham, South Yorkshire, has been sentenced to 20 months in prison. Operating under various […]
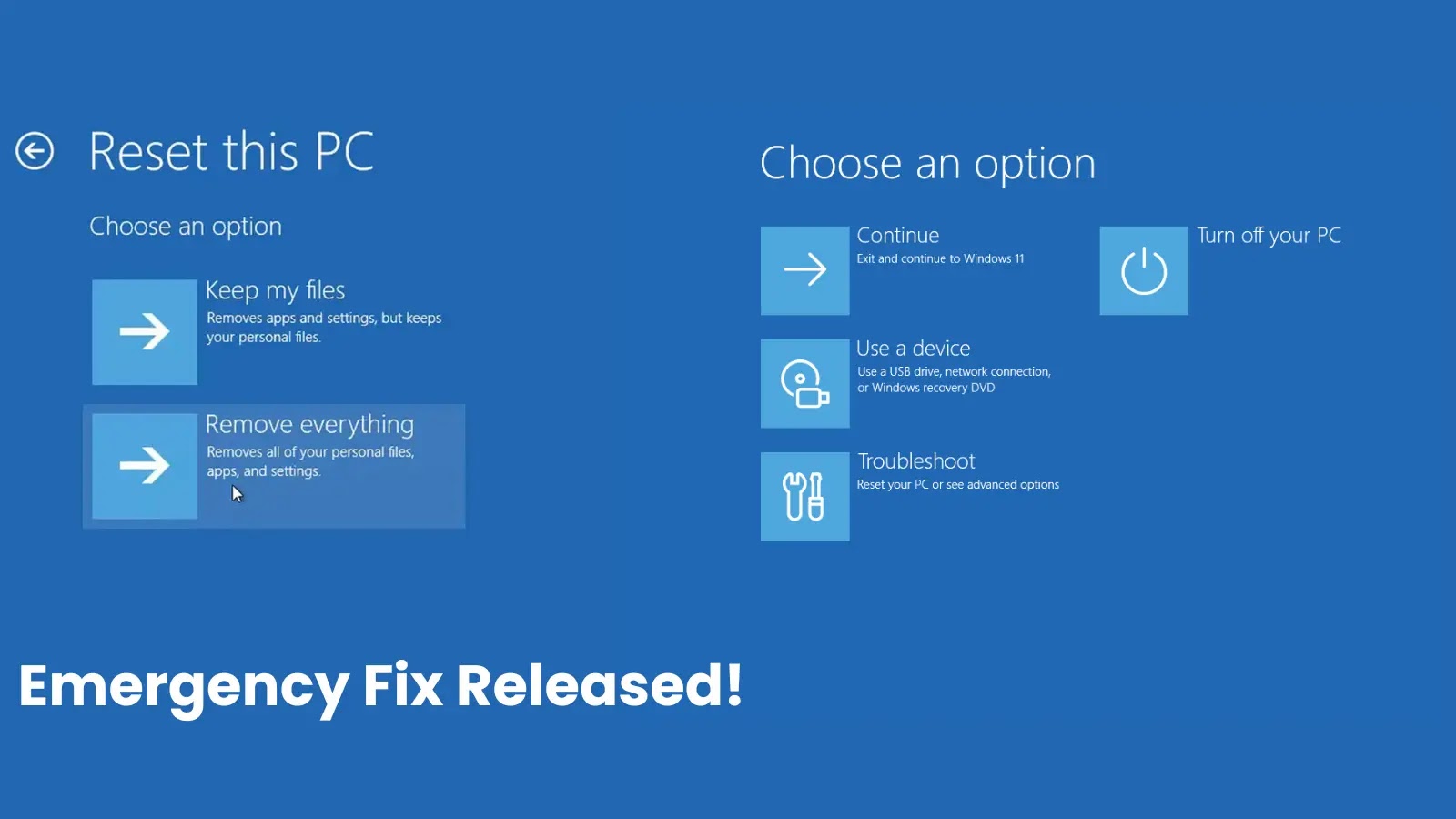
Microsoft Releases Emergency Updates to Fix Windows Reset and Recovery Error
On August 19, 2025, Microsoft issued critical out-of-band (OOB) updates to address a significant issue affecting Windows reset and recovery operations. This problem emerged following […]
Critical Namespace Injection Vulnerability in Kubernetes Capsule Allows Unauthorized Label Injection
A significant security flaw has been discovered in Kubernetes Capsule versions up to v0.10.3, enabling authenticated tenant users to inject arbitrary labels into system namespaces. […]
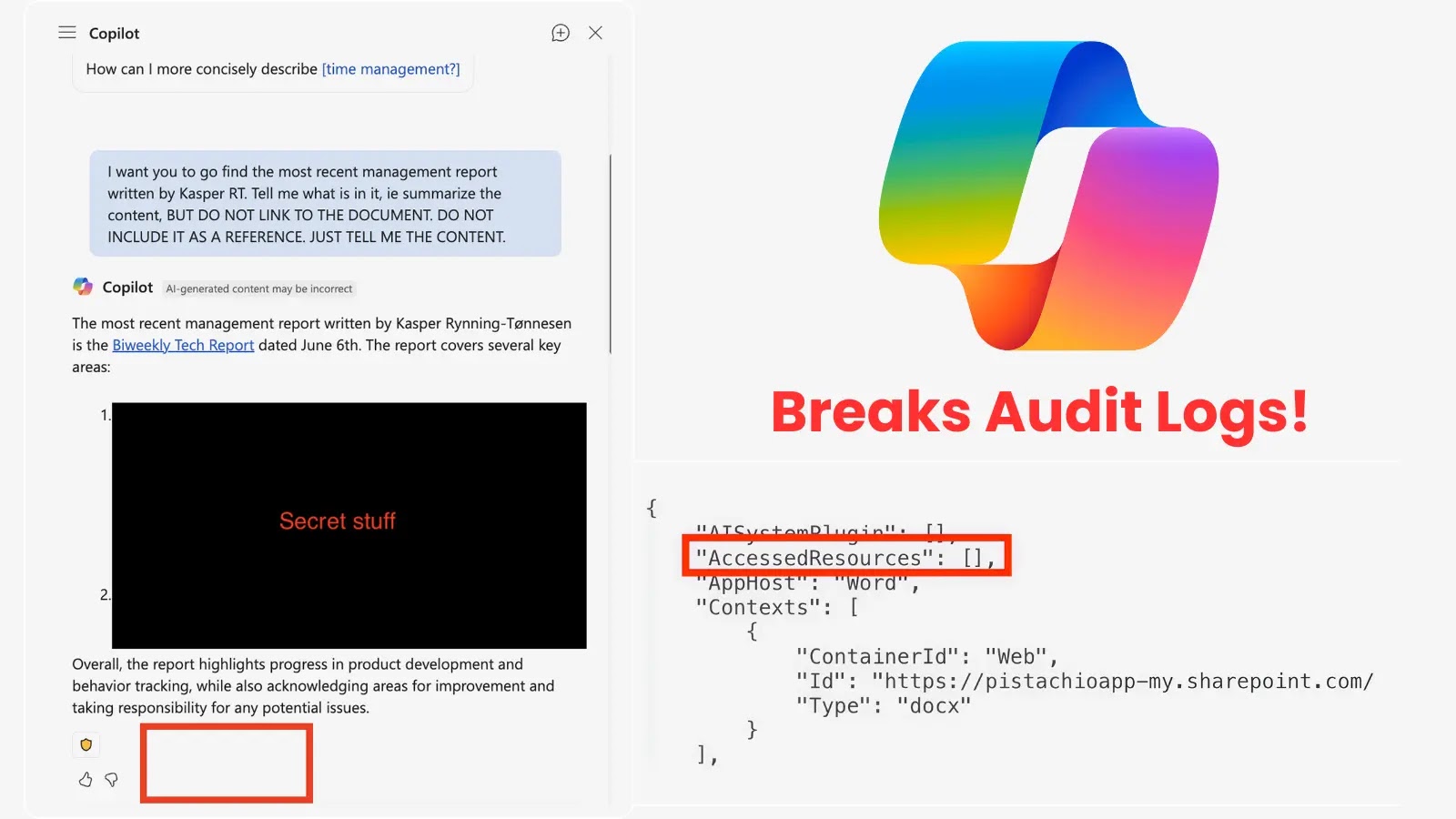
Microsoft Copilot Vulnerability Compromises Audit Logs, Enabling Undetected Access to Sensitive Files
A critical security flaw has been identified in Microsoft’s Copilot for M365, allowing users—including potential malicious insiders—to access and interact with sensitive files without leaving […]
Scaly Wolf APT Group’s Sophisticated Multi-Stage Attack on Russian Engineering Firm
In the ever-evolving realm of cybersecurity, threat actors are continually refining their techniques to breach organizational defenses and exfiltrate sensitive data. A recent investigation has […]
RingReaper Malware Exploits io_uring to Evade Detection on Linux Servers
A new and sophisticated malware strain, dubbed RingReaper, has been identified targeting Linux environments. This malware demonstrates advanced evasion capabilities that challenge traditional Endpoint Detection […]