In recent weeks, cybersecurity researchers have identified a sophisticated malware delivery method that exploits the Internet Archive’s trusted infrastructure to host and disseminate malicious payloads. […]
Month: August 2025
Warlock Ransomware Exploits SharePoint Vulnerabilities to Infiltrate Networks and Exfiltrate Data
In recent weeks, the cybersecurity landscape has been disrupted by the emergence of Warlock, a sophisticated ransomware strain that leverages unpatched Microsoft SharePoint servers to […]
Russian State-Sponsored Hackers Exploit Legacy Cisco Vulnerability to Infiltrate Critical Infrastructure
In a recent advisory, the Federal Bureau of Investigation (FBI) and Cisco have raised alarms over a Russian state-sponsored cyber espionage group, identified as Static […]
Password Managers at Risk: Clickjacking Vulnerabilities Expose Sensitive Data
In a recent study presented at the DEF CON conference, security researcher Marek Tóth unveiled that numerous popular password managers are susceptible to clickjacking attacks, […]
Florida Man Sentenced to 10 Years for Role in Scattered Spider Cybercrime Group
In a significant development in the fight against cybercrime, 20-year-old Noah Michael Urban from Palm Coast, Florida, has been sentenced to a decade in federal […]
Apple Releases Emergency Patch for CVE-2025-43300 Zero-Day Vulnerability Exploited in Targeted Attacks
Apple has recently issued critical security updates to address a zero-day vulnerability, identified as CVE-2025-43300, which has been actively exploited in highly sophisticated attacks targeting […]
Scattered Spider Hacker Sentenced to 10 Years and Ordered to Pay $13 Million in Restitution for SIM Swapping Crypto Theft
In a significant development in the fight against cybercrime, 20-year-old Noah Michael Urban, a member of the notorious cybercriminal group Scattered Spider, has been sentenced […]
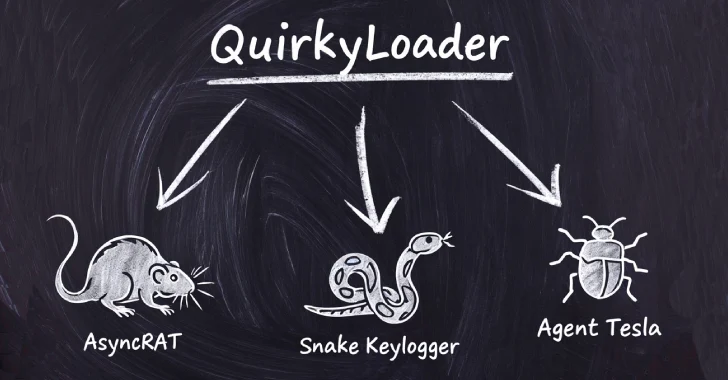
Cybercriminals Deploy QuirkyLoader to Distribute Agent Tesla, AsyncRAT, and Snake Keylogger
Cybersecurity experts have identified a new malware loader, QuirkyLoader, actively used since November 2024 to disseminate various malicious payloads through email spam campaigns. This loader […]
The Persistent Threat of Weak Passwords and Compromised Accounts: Insights from the Blue Report 2025
In the ever-evolving landscape of cybersecurity, organizations often focus on countering sophisticated adversary techniques. However, the most damaging breaches frequently stem from fundamental vulnerabilities: weak […]
India’s Ban on Real-Money Gaming: A $23 Billion Industry at Risk
On August 20, 2025, India’s lower house of parliament passed the Promotion and Regulation of Online Gaming Bill, 2025, introducing a comprehensive ban on real-money […]