On August 19, 2025, the Cybersecurity and Infrastructure Security Agency (CISA) released four detailed advisories concerning Industrial Control Systems (ICS). These advisories bring to light […]
Month: August 2025
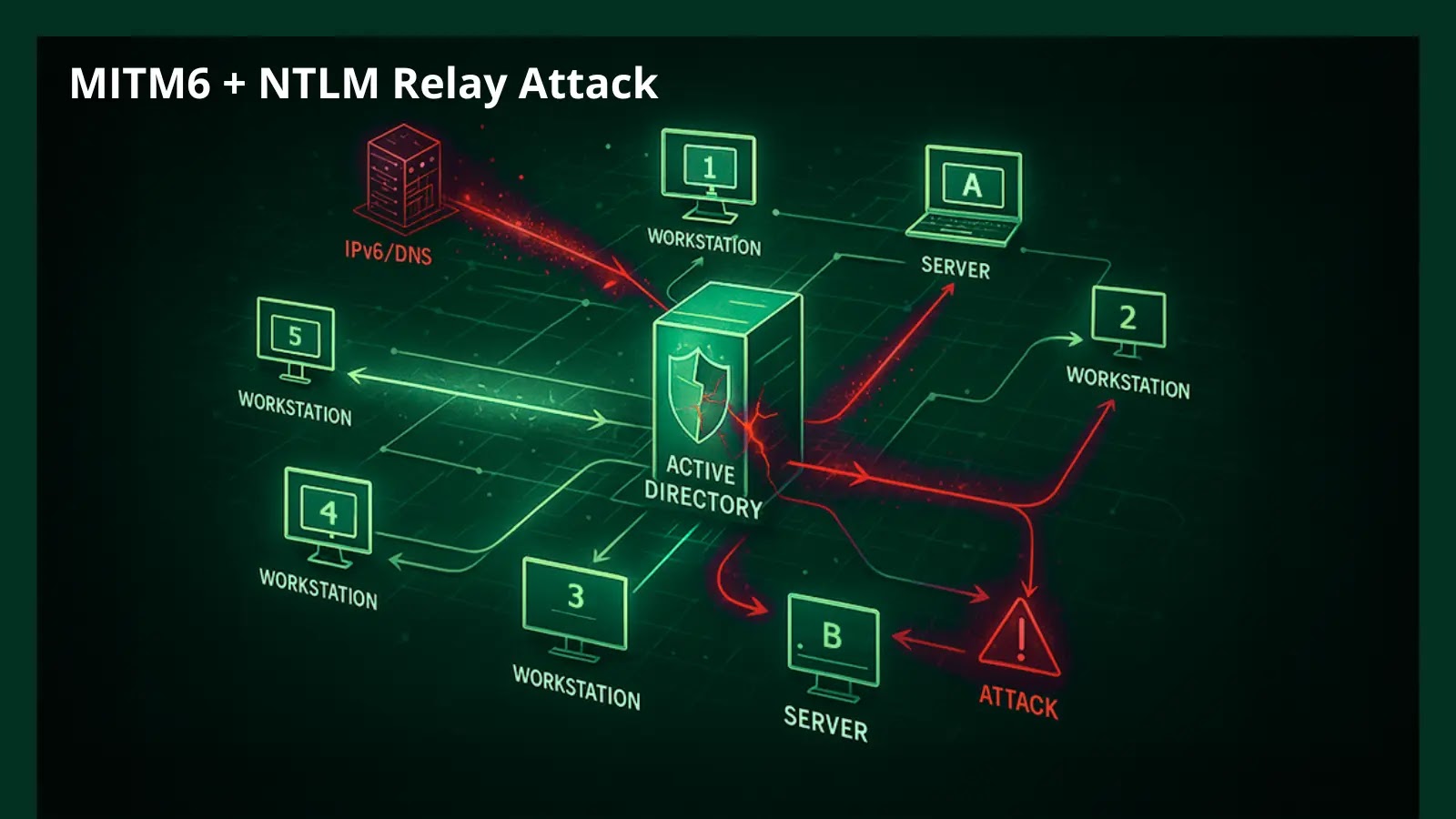
Exploiting Windows IPv6 Auto-Configuration: The MITM6 and NTLM Relay Attack
A sophisticated cyberattack technique has emerged, combining MITM6 and NTLM relay methods to achieve full compromise of Active Directory domains. This attack exploits Windows’ default […]
UNC5518 Exploits Legitimate Websites with Fake CAPTCHAs to Deploy Malware
A sophisticated cybercrime operation has emerged, targeting unsuspecting internet users through a deceptive social engineering technique that exploits one of the web’s most trusted security […]
DragonForce Ransomware: A Comprehensive Analysis of Tactics, Techniques, and Impact
Introduction Since its emergence in late 2023, DragonForce has rapidly evolved into a formidable ransomware operation, posing significant threats across various sectors. Operating under a […]
Florida Man Sentenced to 10 Years for Role in Scattered Spider Cybercrime Group
In a landmark case highlighting the escalating threat of cybercrime, 20-year-old Noah Michael Urban from Palm Coast, Florida, has been sentenced to a decade in […]
FBI Issues Critical Alert on Russian State-Sponsored Cyber Attacks Targeting U.S. Critical Infrastructure
The Federal Bureau of Investigation (FBI) has recently issued a critical security alert concerning sophisticated cyber operations orchestrated by the Russian Federal Security Service (FSB) […]
Kali Linux Enhances Vagrant Image Creation with DebOS Integration
The Kali Linux development team has recently overhauled their Vagrant image build process, transitioning from HashiCorp’s Packer to DebOS. This strategic move aims to unify […]
Cybercriminals Exploit PDF Editor to Convert Devices into Residential Proxies
Cybersecurity researchers have identified a sophisticated cyber threat where attackers distribute a seemingly legitimate PDF editor application to transform infected devices into residential proxies. This […]
Critical QUIC-LEAK Vulnerability Exposes Servers to Memory Exhaustion and Denial-of-Service Attacks
A significant security flaw, identified as CVE-2025-54939 and termed QUIC-LEAK, has been discovered in the LSQUIC QUIC implementation. This vulnerability enables remote attackers to exhaust […]
Mozilla Releases Firefox 142 to Address Critical Security Vulnerabilities Enabling Remote Code Execution
On August 19, 2025, Mozilla unveiled Firefox 142, a pivotal update designed to rectify multiple high-severity security vulnerabilities that could permit attackers to execute arbitrary […]