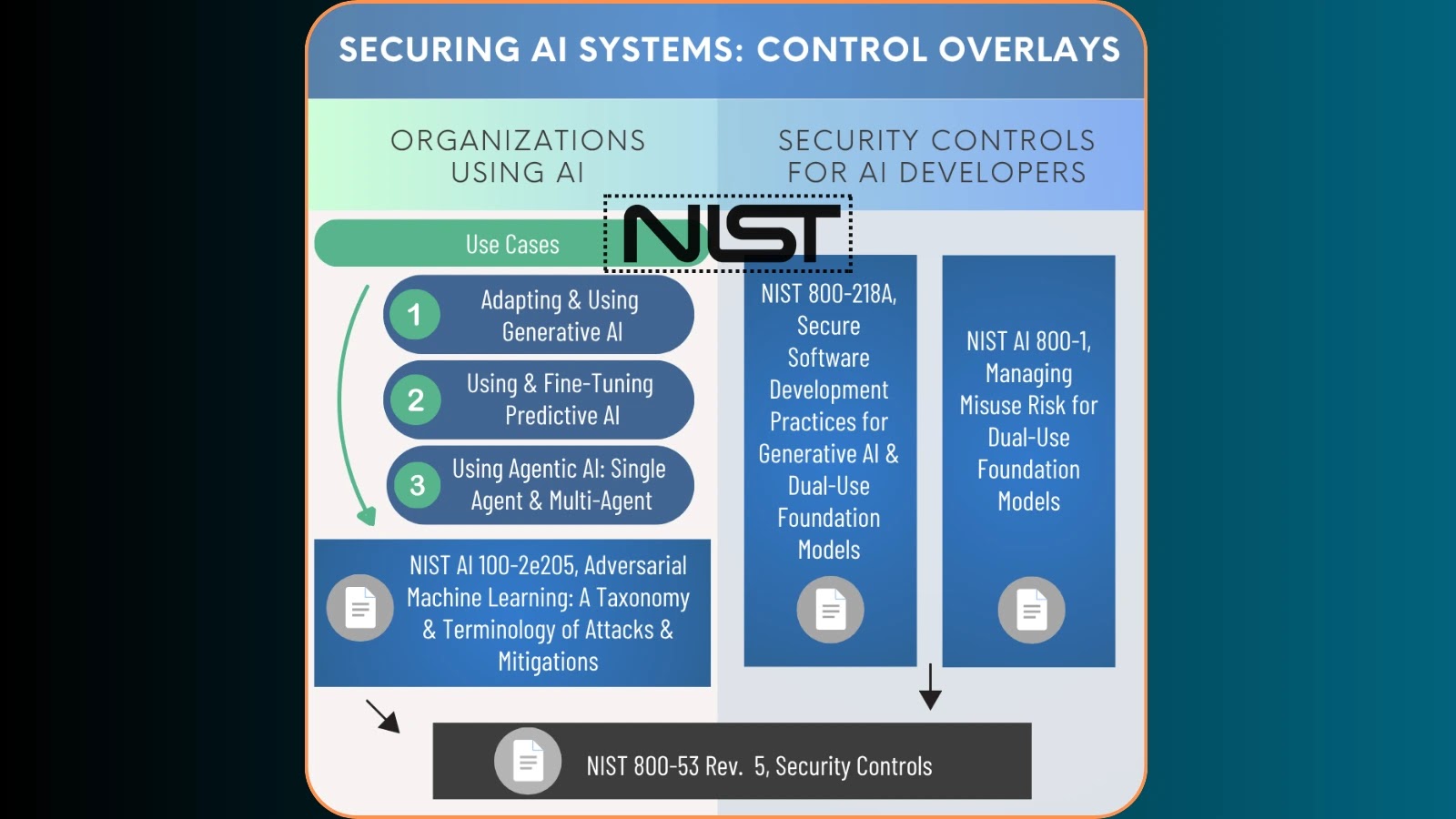
On August 14, 2025, the National Institute of Standards and Technology (NIST) unveiled a comprehensive concept paper detailing proposed NIST Special Publication (SP) 800-53 Control […]
Month: August 2025
Critical Vulnerability in Docker Desktop for Windows Enables Full Host System Compromise
A recently identified security flaw in Docker Desktop for Windows, designated as CVE-2025-9074, has exposed a critical vulnerability that allows malicious containers to gain unauthorized […]
South Asian APT Group Employs Advanced Tactics to Infiltrate Military Personnel’s Mobile Devices
A sophisticated South Asian Advanced Persistent Threat (APT) group has been orchestrating an extensive espionage campaign targeting military personnel and defense organizations across Sri Lanka, […]
Malicious Go Module Disguised as SSH Brute-Forcing Tool Steals Credentials via Telegram
A sophisticated supply chain attack has emerged, targeting developers through a malicious Go module package that masquerades as a legitimate SSH brute-forcing tool while covertly […]
BQTLOCK Ransomware: A New RaaS Threat with Advanced Evasion Techniques
In mid-July 2025, a sophisticated ransomware strain named BQTLOCK emerged, operating under a comprehensive Ransomware-as-a-Service (RaaS) model. This model democratizes access to advanced encryption capabilities, […]
Lumma Affiliates Employ Advanced Evasion Techniques to Maintain Stealth and Operational Continuity
Since its emergence in 2022, the Lumma information stealer has evolved into a formidable malware-as-a-service (MaaS) platform, dominating the cybercriminal landscape. By late 2024, Lumma […]
Ex-Developer Sentenced to Four Years for Sabotaging Ohio Employer with Kill-Switch Malware
In a significant case highlighting the dangers of insider threats, 55-year-old Davis Lu, a Chinese national residing in Houston, Texas, has been sentenced to four […]
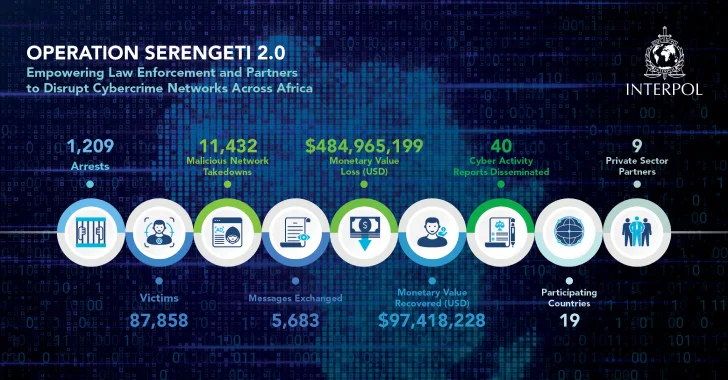
INTERPOL’s Operation Serengeti 2.0: A Major Blow to Cybercrime in Africa
In a significant move against cybercrime, INTERPOL has announced the arrest of 1,209 individuals across 18 African nations. This operation, part of the ongoing Operation […]
Revolutionizing Penetration Testing: The Impact of Automation on Delivery and Efficiency
Penetration testing (pentesting) has long been a cornerstone in identifying and mitigating security vulnerabilities before malicious actors can exploit them. However, as cyber threats have […]
Chinese Cyber Espionage Groups Intensify Attacks on Cloud and Telecom Sectors
Recent analyses by cybersecurity experts have unveiled a surge in malicious activities orchestrated by Chinese cyber espionage groups, notably Murky Panda, Genesis Panda, and Glacial […]