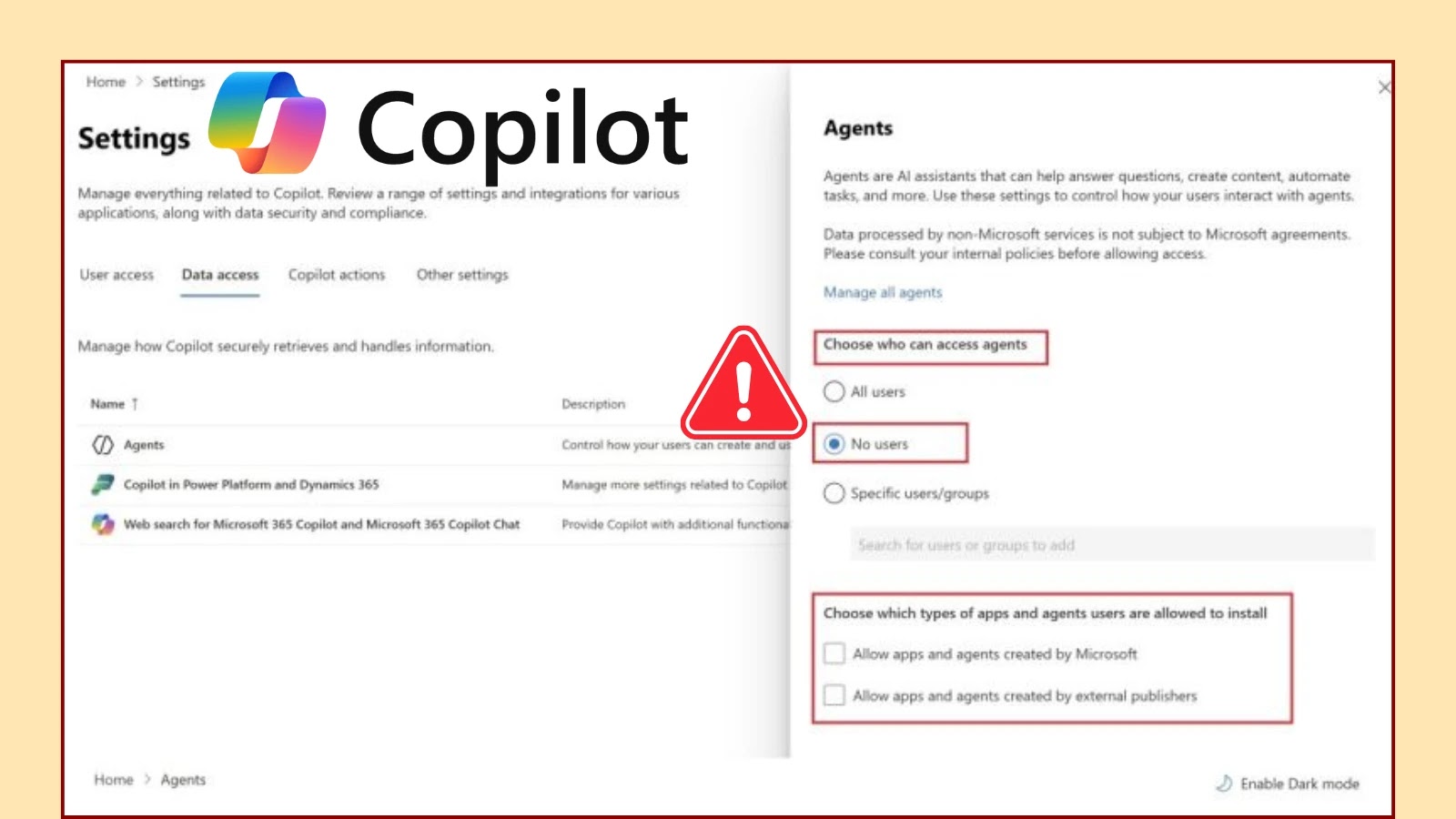
In May 2025, Microsoft introduced 107 Copilot Agents across Microsoft 365 tenants, aiming to enhance productivity through AI-driven assistance. However, security experts have identified a […]
Month: August 2025
Critical Vulnerabilities in Tableau Server Allow Malicious File Uploads and Remote Code Execution
A series of critical security vulnerabilities have been identified in Tableau Server, potentially allowing attackers to upload and execute malicious files, leading to full system […]
NIST Releases Ascon-Based Lightweight Cryptography Standard to Secure IoT Devices
In August 2025, the National Institute of Standards and Technology (NIST) unveiled Special Publication 800-232, introducing the Ascon family of algorithms as the new standard […]
Critical Vulnerabilities in Tableau Server Allow Malicious File Uploads and Remote Code Execution
Salesforce’s Tableau Server, a widely utilized data visualization tool, has been found to contain multiple critical security vulnerabilities that could allow attackers to upload and […]
Comparing EDR and MDR: Choosing the Right Cybersecurity Solution for Your Organization
In today’s rapidly evolving digital landscape, organizations face increasingly sophisticated cyber threats that necessitate robust security measures. Two prominent solutions have emerged to address these […]
Exploiting Python’s eval() and exec() Functions: A Growing Cybersecurity Threat
In recent years, the cybersecurity landscape has witnessed a surge in sophisticated attacks targeting Python applications. Central to these threats is the exploitation of Python’s […]
Chinese Hacker Sentenced to Four Years for Deploying Kill Switch on Global Network
In a landmark case highlighting the severe risks posed by insider threats, 55-year-old Chinese national Davis Lu has been sentenced to four years in federal […]
Arch Linux Faces Prolonged DDoS Attack Disrupting Key Services
The Arch Linux Project has been grappling with a persistent distributed denial-of-service (DDoS) attack that commenced on August 16, 2025. This sustained assault has significantly […]
Cybercriminals Exploit Windows Scheduled Tasks for Stealthy System Persistence
In recent times, cybersecurity experts have observed a significant increase in the misuse of Windows Scheduled Tasks by malicious actors aiming to maintain unauthorized access […]
Critical Vulnerabilities in vtenext CRM Allow Authentication Bypass and Remote Code Execution
A recent security assessment of vtenext CRM version 25.02 has uncovered multiple critical vulnerabilities that enable unauthenticated attackers to bypass authentication mechanisms through three distinct […]