The Level Lock Pro, the latest iteration from Level Home, builds upon its predecessor’s foundation to offer enhanced features and performance for homeowners seeking a […]
Month: August 2025
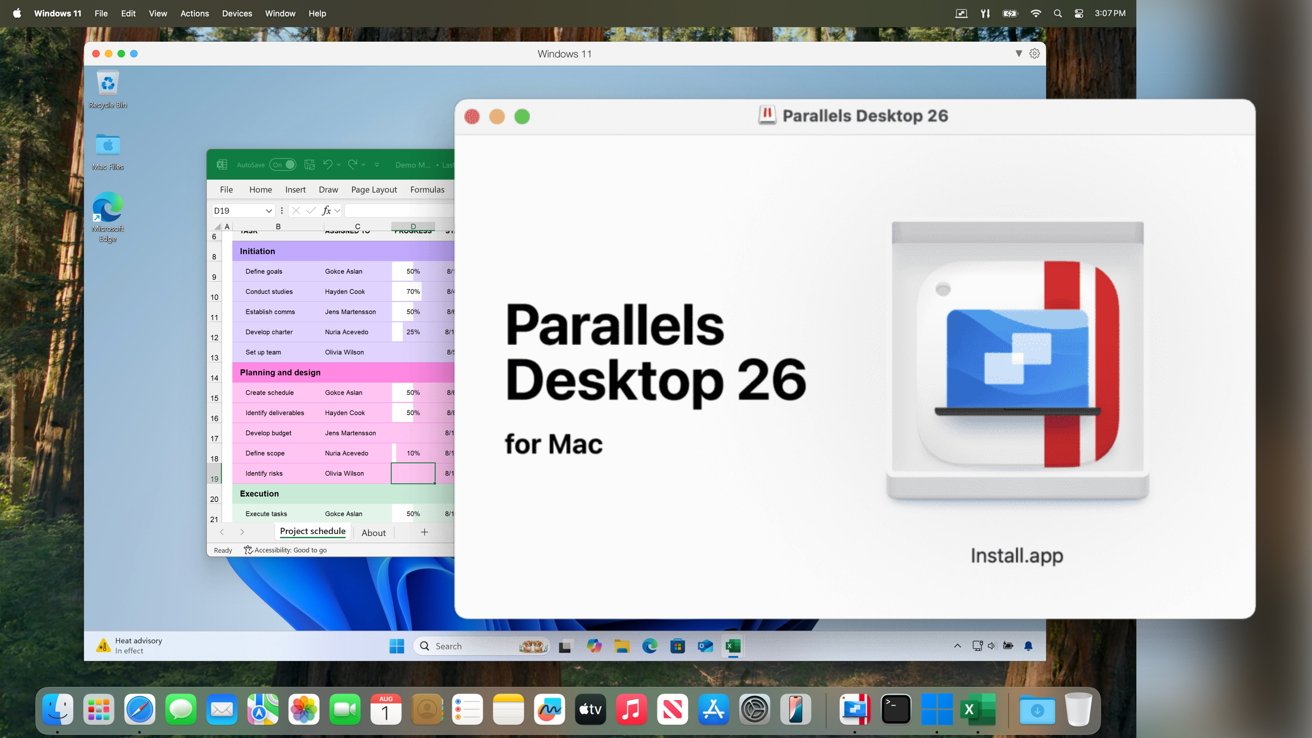
Parallels Desktop 26: Embracing Apple’s Branding and Supporting macOS 26 Tahoe
Parallels Desktop has unveiled its latest iteration, Parallels Desktop 26, aligning its versioning with Apple’s recent shift to year-based numbering for its operating systems. This […]
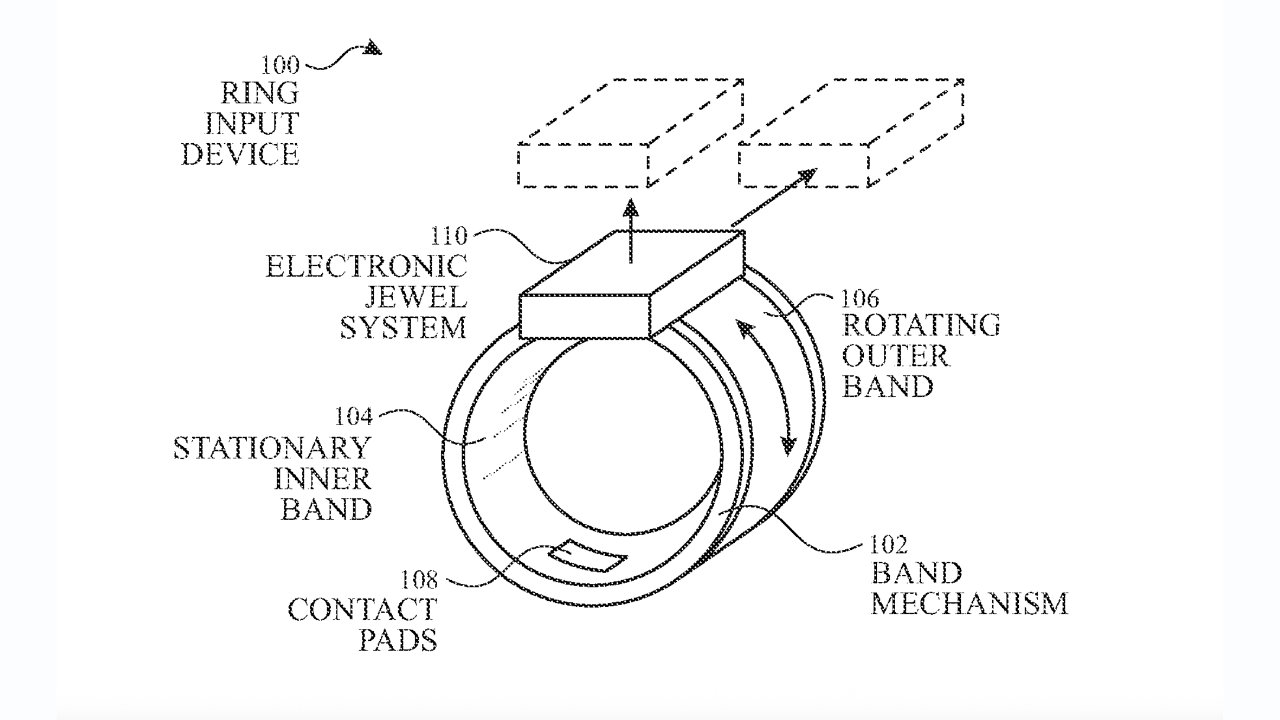
Apple’s Smart Ring: A Multifunctional Companion for iPhone Control
Apple’s exploration into wearable technology has led to the development of a smart ring, potentially revolutionizing how users interact with their devices. This innovative accessory […]
[August-26-2025] Daily Cybersecurity Threat Report
This report details a series of recent cyber incidents, providing key information for each event, including published URLs and associated screenshots, strictly based on the […]
Advanced Gmail Phishing Tactics Employ AI Prompt Injection to Evade Detection
Phishing attacks have long relied on deceiving individuals into divulging sensitive information. However, a recent campaign has escalated this threat by not only targeting users […]
Microsoft Introduces New Admin Controls for Copilot Agent Sharing in Microsoft 365
In mid-September 2025, Microsoft is set to launch a pivotal administrative feature within Microsoft 365, empowering IT administrators to oversee organization-wide sharing permissions for user-created […]
KorPlug Malware: Advanced Obfuscation Techniques and Analysis Challenges
KorPlug, a sophisticated malware strain, has recently emerged as a significant threat in the cybersecurity landscape. Employing advanced obfuscation techniques, it effectively evades detection and […]
Cybercriminals Exploit SendGrid to Harvest Login Credentials
A sophisticated credential harvesting campaign has recently emerged, exploiting the trusted reputation of SendGrid, a widely used cloud-based email service platform. By leveraging SendGrid’s legitimate […]
Apple’s Zero-Click RCE Vulnerability: A Deep Dive into CVE-2025-43300
A critical zero-click remote code execution (RCE) vulnerability, identified as CVE-2025-43300, has been discovered within Apple’s image processing infrastructure. This flaw resides in the JPEG […]
Emergence of Mac.c: A New macOS Stealer Offering Rapid Data Exfiltration on the Dark Web
A newly identified macOS-based information stealer, known as Mac.c, has recently appeared on darknet forums, offering rapid data exfiltration capabilities for a subscription fee of […]

![[August-26-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)