The Synology BeeStation Plus is a network-attached storage (NAS) device designed to provide a straightforward solution for users seeking accessible storage on their home network. […]
Month: August 2025
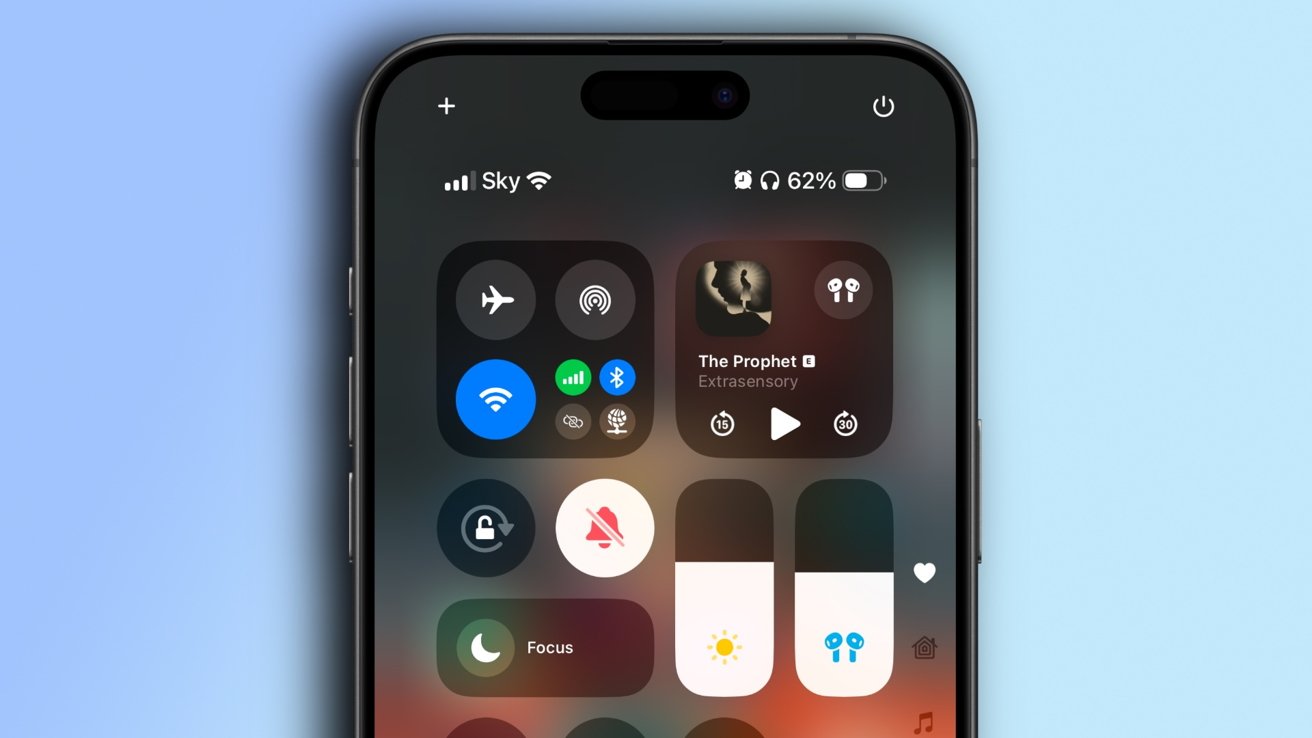
Mastering the Enhanced Control Center in iOS 18: A Comprehensive Guide
With the release of iOS 18, Apple has significantly revamped the iPhone’s Control Center, introducing a suite of customization options that empower users to tailor […]
Apple’s Fourth Retail Store in India Set to Open in Pune on September 4
Apple is set to expand its retail footprint in India with the inauguration of its fourth official store, Apple Koregaon Park, located in Pune. The […]
Chipolo Introduces Rechargeable Bluetooth Trackers with Enhanced Features
Chipolo, a leader in Bluetooth tracking technology, has unveiled its latest line of rechargeable trackers, marking a significant advancement in the realm of personal item […]
Apple Secures Half of TSMC’s 2nm Chip Production Capacity for Future Devices
Apple is set to become the primary beneficiary of Taiwan Semiconductor Manufacturing Company’s (TSMC) forthcoming 2-nanometer (2nm) chip production, securing approximately 50% of the initial […]
[August-27-2025] Daily Cybersecurity Threat Report
This report details a series of recent cyber incidents, providing key information for each event, including published URLs and associated screenshots, strictly based on the […]
Cyber Sabotage Disrupts Iranian Maritime Communications
In late August 2025, a sophisticated cyberattack targeted Iran’s maritime communications infrastructure, severing satellite links and navigation aids for numerous vessels. Instead of attacking each […]
Massive Coordinated Scanning Campaign Targets Microsoft Remote Desktop Protocol Services
In a significant escalation of cyber reconnaissance activities, a massive coordinated scanning campaign has been detected targeting Microsoft Remote Desktop Protocol (RDP) services. Threat actors […]
Threat Actors Evolve Android Droppers to Deploy Simple Malware and Evade Detection
In the ever-evolving landscape of cybersecurity, threat actors are continuously refining their tactics to bypass security measures and deploy malware more effectively. A notable development […]
Malicious Bing Ads Deploy Weaponized PuTTY to Exploit Kerberos and Attack Active Directory Services
A recent cybersecurity investigation has uncovered a sophisticated malvertising campaign that leverages Microsoft’s Bing search platform to distribute a weaponized version of PuTTY, a widely […]



![[August-27-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)



