A new and highly sophisticated variant of the Hook Android banking trojan, known as Hook Version 3, has surfaced, marking a significant advancement in mobile […]
Month: August 2025
Unveiling Mustang Panda: China’s Elite Cyber Espionage Group and Its Evolving Tactics
Since at least 2014, Mustang Panda, a China-based advanced persistent threat (APT) group, has established itself as a formidable force in the realm of cyber […]
Critical Chrome Use-After-Free Vulnerability Allows Remote Code Execution
Google has recently issued an urgent security update for its Chrome browser to address a critical use-after-free vulnerability identified as CVE-2025-9478. This flaw resides within […]
Salesloft Drift Compromise Leads to Unauthorized Access and Data Exfiltration from Salesforce Instances
In a recent and sophisticated cyberattack, a threat actor identified as UNC6395 exploited vulnerabilities in the Salesloft Drift application to gain unauthorized access to corporate […]
Emergence of Cephalus Ransomware: Exploiting Remote Desktop Protocol for Initial Access
A new ransomware variant, dubbed Cephalus, has surfaced, posing a significant threat to organizations by exploiting vulnerabilities in Remote Desktop Protocol (RDP) connections. Named after […]
DOGE’s Unsecured Cloud Storage of Social Security Data Sparks Major Security Concerns
A recent whistleblower disclosure has brought to light alarming actions by the Department of Government Efficiency (DOGE) within the Social Security Administration (SSA). The department […]
ZipLine Campaign Targets U.S. Manufacturing Firms with Advanced In-Memory Malware
In recent weeks, a sophisticated cyberattack known as the ZipLine campaign has been targeting manufacturing companies in the United States. This operation employs advanced social […]
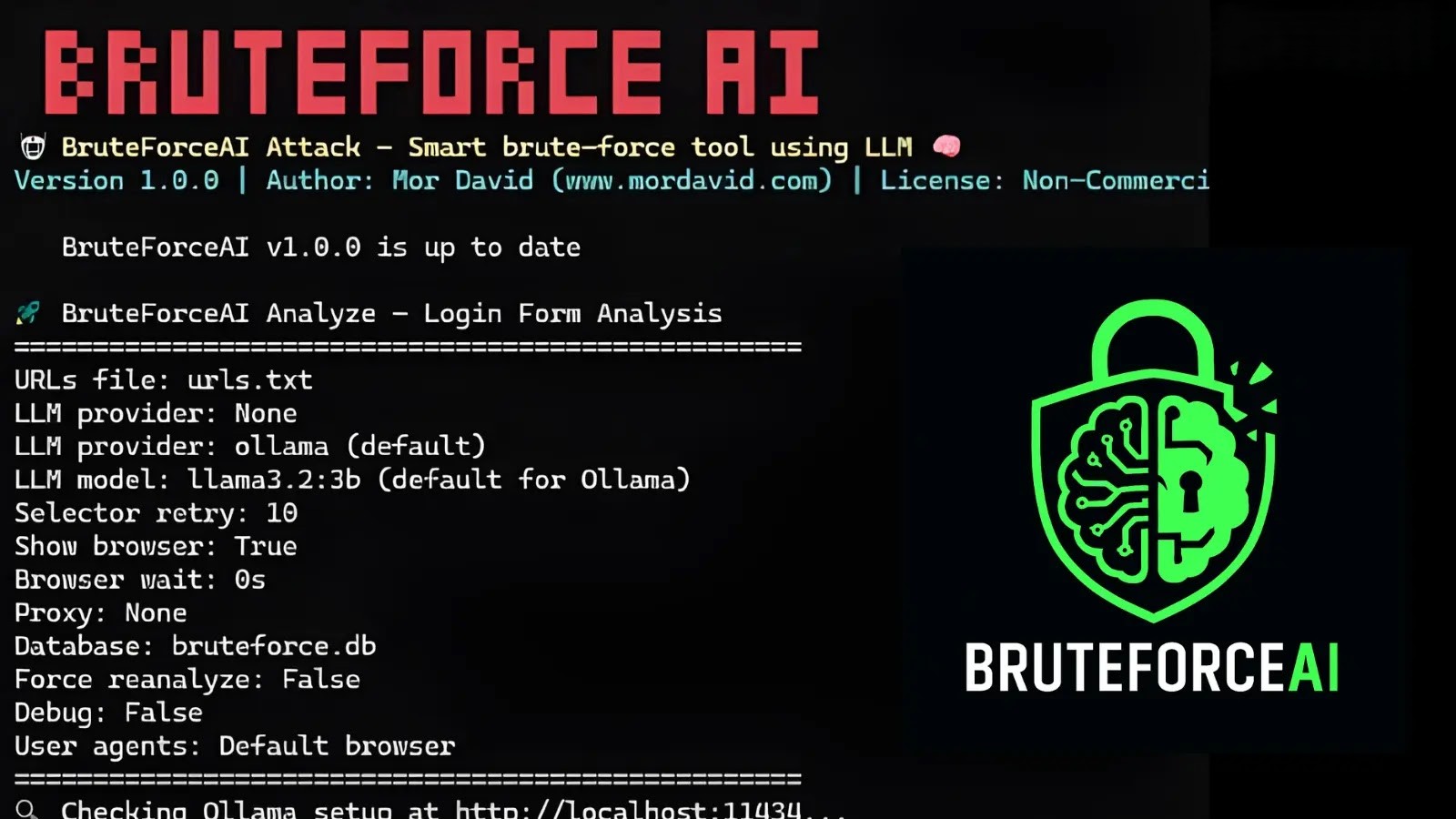
BruteForceAI: Revolutionizing Penetration Testing with AI-Driven Brute-Force Attacks
In the ever-evolving landscape of cybersecurity, the emergence of BruteForceAI marks a significant advancement in penetration testing methodologies. Developed by Mor David, this innovative framework […]
Spotify Introduces Direct Messaging for Music Sharing: Exploring Potential Security Implications
On August 26, 2025, Spotify unveiled Messages, a direct messaging feature designed to enhance user engagement by facilitating the sharing of music, podcasts, and audiobooks […]
Emerging Zip Slip Vulnerability Enables Attackers to Manipulate ZIP Files During Decompression
A newly identified variant of the Zip Slip vulnerability has surfaced, allowing cybercriminals to exploit path traversal flaws in widely used decompression utilities. By crafting […]