A critical zero-day vulnerability, designated as CVE-2025-54309, has been identified in CrushFTP, a widely used file transfer server. This flaw allows remote attackers to bypass […]
Day: August 28, 2025
Microsoft Teams Users Face Global Disruption in Accessing Embedded Office Documents
On Thursday, August 28, 2025, a significant service disruption affected Microsoft Teams users worldwide, preventing them from opening embedded Microsoft Office documents within the platform. […]
Critical Zero-Day Vulnerability in Citrix NetScaler ADC and Gateway Exploited in the Wild
A critical zero-day remote code execution (RCE) vulnerability, identified as CVE-2025-7775, has been discovered in Citrix NetScaler Application Delivery Controller (ADC) and NetScaler Gateway systems. […]
Emerging Ransomware Group ‘Underground’ Adopts Advanced Tactics to Target Global Organizations
Over the past year, a new ransomware group known as ‘Underground’ has surfaced as a significant threat to organizations across various industries and regions. Initially […]
CISA Issues Urgent Alert on Active Exploitation of Citrix NetScaler Zero-Day Vulnerability
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding a critical zero-day vulnerability affecting Citrix NetScaler systems, identified as CVE-2025-7775. This […]
Sophisticated Malware Campaign Targets Indonesian Pensioners by Impersonating TASPEN
A sophisticated cyberattack has recently emerged, targeting Indonesia’s senior citizens by exploiting their trust in the nation’s pension fund system. This malicious campaign impersonates PT […]
Critical Vulnerability in Kea DHCP Server Allows Remote Service Disruption with a Single Packet
A recently identified vulnerability in the ISC Kea DHCP server, designated as CVE-2025-40779, poses a significant threat to network infrastructures globally. This flaw enables remote […]
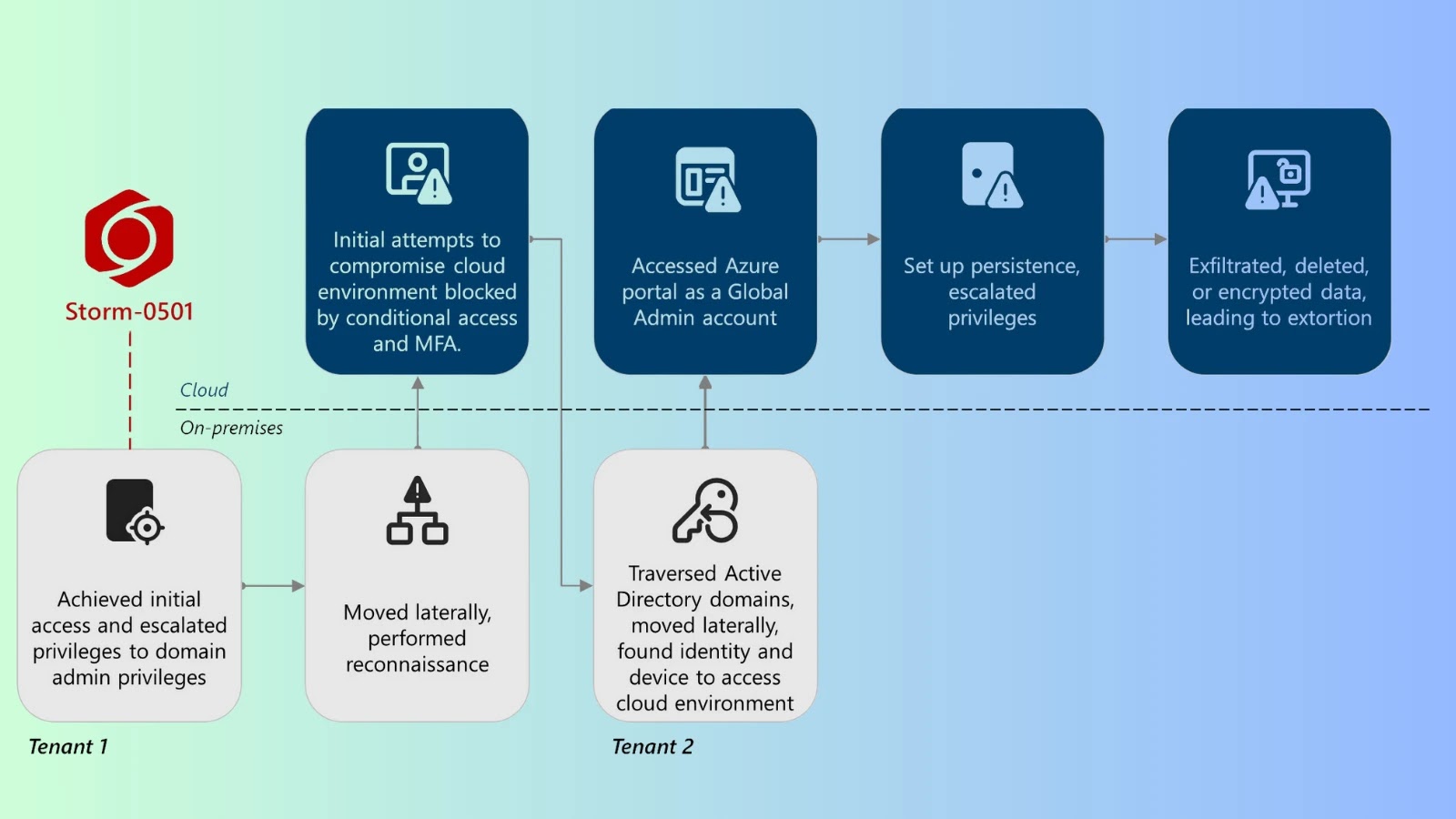
Microsoft Exposes Storm-0501’s Advanced Cloud Ransomware Tactics
Microsoft Threat Intelligence has unveiled a significant evolution in ransomware methodologies, spearheaded by the financially motivated threat actor known as Storm-0501. This group has transitioned […]
CISA Releases Comprehensive Guide to Counter Chinese State-Sponsored Cyber Threats
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the National Security Agency (NSA), Federal Bureau of Investigation (FBI), and a coalition of […]
TAG-144 Intensifies Cyber Attacks on South American Government Entities with Advanced Tactics
Over the past year, a clandestine cyber threat group identified as TAG-144—also known by aliases Blind Eagle and APT-C-36—has escalated its operations targeting government institutions […]