A significant security flaw has been identified in Cisco’s Unified Intelligence Center (CUIC), a pivotal component in Cisco’s contact center solutions. This vulnerability, designated as […]
Month: July 2025
Cybercriminals Exploit SVG Files to Deliver Malicious JavaScript
In recent cybersecurity developments, threat actors have increasingly weaponized Scalable Vector Graphics (SVG) files to embed malicious JavaScript code, facilitating sophisticated phishing campaigns that bypass […]
Threat Actors Deploy Malicious npm Packages to Disrupt Russian and Belarusian Websites
A sophisticated cyber campaign has emerged, targeting Russian-language users through a network of compromised npm packages. Threat actors have weaponized at least 28 new packages, […]
International Operation Dismantles Pro-Russian Hacking Group NoName057(16)
In a significant international effort, law enforcement agencies from 12 countries, coordinated by Europol and Eurojust, have successfully dismantled the pro-Russian hacking group NoName057(16). This […]
CitrixBleed 2 Vulnerability: A Critical Threat to NetScaler Devices
In June 2025, a critical security flaw, designated as CVE-2025-5777 and colloquially known as CitrixBleed 2, was identified in Citrix NetScaler Application Delivery Controller (ADC) […]
PyPI Implements Ban on Inbox.ru Domains After Massive Spam Campaign
The Python Package Index (PyPI), a central repository for Python programming language packages, has recently enforced a ban on registrations from the inbox.ru email domain. […]
Critical SharePoint Remote Code Execution Vulnerability Exploited via Malicious XML Payloads in Web Parts
A recently disclosed remote code execution (RCE) vulnerability in Microsoft SharePoint has been identified, stemming from the deserialization process of WebPart properties. This flaw allows […]
Cybercriminals Exploit DNS Queries for Covert Command-and-Control Operations and Data Exfiltration
Cybercriminals are increasingly leveraging the Domain Name System (DNS) to establish covert communication channels, enabling command-and-control (C2) operations and data exfiltration that bypass traditional network […]
GhostContainer Malware Exploits Microsoft Exchange Servers in Targeted Cyber Espionage Campaigns
A sophisticated cyber espionage campaign has been identified, targeting Microsoft Exchange servers within government and high-tech organizations across Asia. The malware, known as GhostContainer, exploits […]
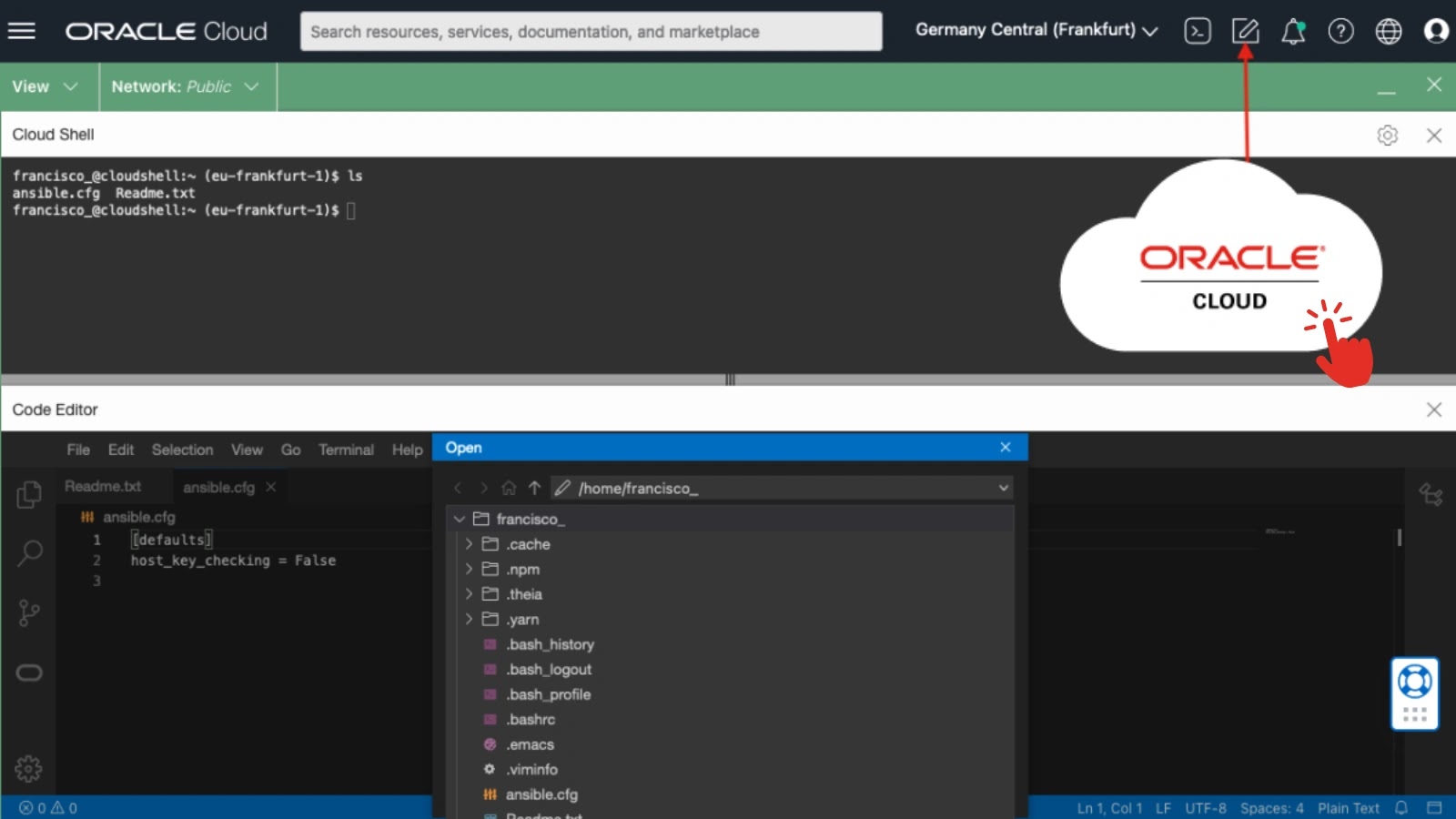
Critical Vulnerability in Oracle Cloud Code Editor Exposes Users to Remote Code Execution
A significant security flaw was identified in Oracle Cloud Infrastructure’s (OCI) Code Editor, potentially allowing attackers to execute remote code within users’ Cloud Shell environments […]