On July 14, 2025, Beluga, a prominent Russian premium vodka producer owned by NovaBev Group, experienced a significant ransomware attack that severely disrupted its IT […]
Month: July 2025
Critical Buffer Overflow Vulnerability in Lenovo Protection Driver Exposes Systems to Arbitrary Code Execution
A significant security vulnerability has been identified in Lenovo’s Protection Driver, potentially allowing local attackers with elevated privileges to execute arbitrary code on affected systems. […]
Cybercriminals Exploit GitHub to Distribute Malware via Fake Accounts
In a concerning development, cybercriminals have been found exploiting GitHub, a widely trusted platform among developers, to distribute malware through a network of fake accounts. […]
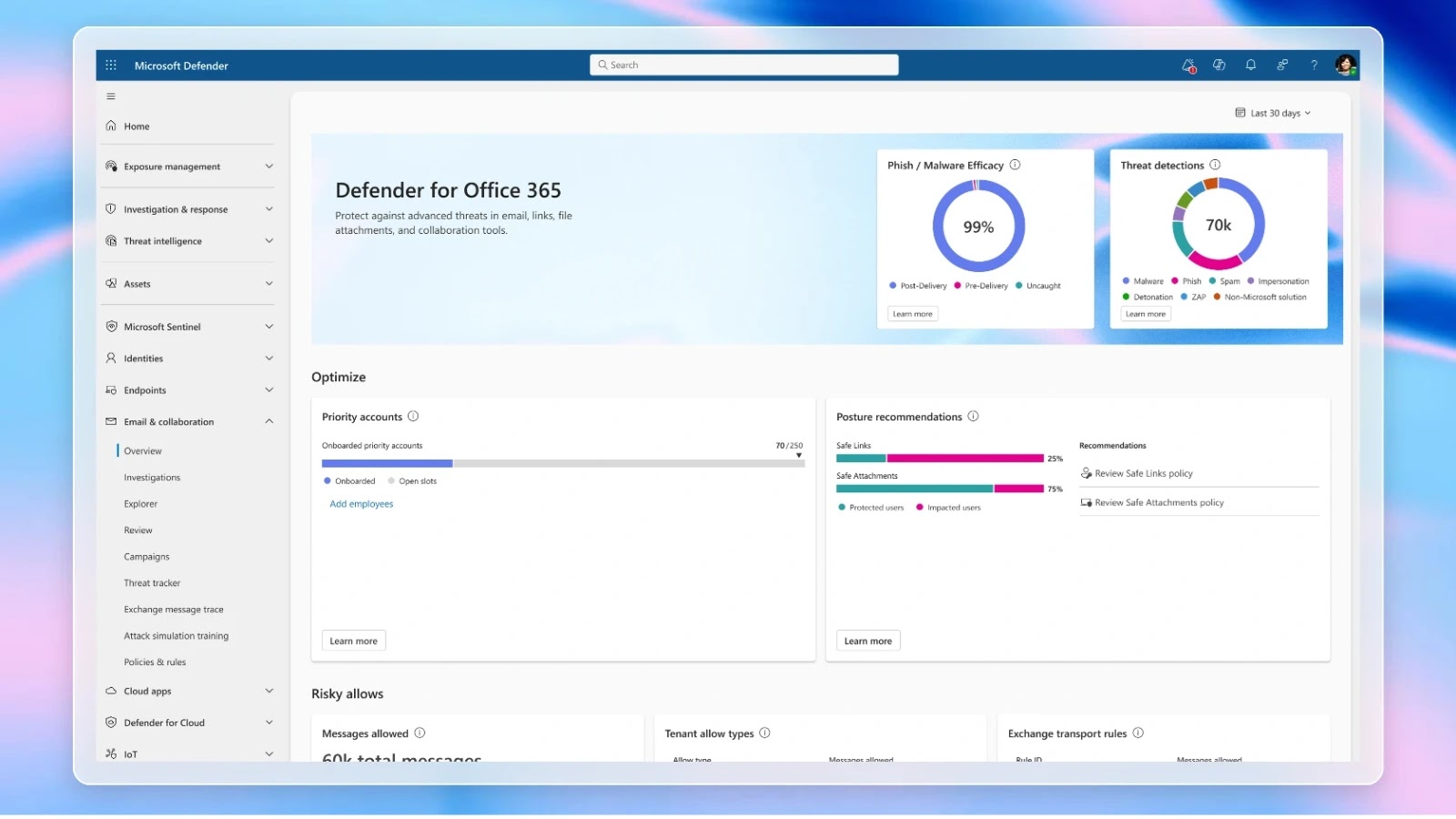
Microsoft Defender for Office 365 Unveils Enhanced Dashboard for Comprehensive Threat Insights
Microsoft has introduced a significant update to its Defender for Office 365 platform, featuring a redesigned customer dashboard aimed at providing security teams with real-time, […]
Critical Vulnerability in Ubiquiti UniFi Devices Enables Remote Command Injection
A significant security flaw has been identified in multiple Ubiquiti UniFi Access devices, potentially allowing unauthorized individuals to execute arbitrary commands remotely. This vulnerability, designated […]
Critical Vulnerabilities in Sophos Intercept X for Windows Allow Arbitrary Code Execution
Sophos, a leading cybersecurity firm, has recently addressed three critical vulnerabilities in its Intercept X for Windows product line. These flaws, identified as CVE-2024-13972, CVE-2025-7433, […]
Threat Actors Exploiting Ivanti Connect Secure Vulnerabilities to Deploy Cobalt Strike Beacon
Since December 2024, a sophisticated malware campaign has been actively targeting Ivanti Connect Secure VPN devices by exploiting critical vulnerabilities, notably CVE-2025-0282 and CVE-2025-22457. These […]
Critical Fortinet FortiWeb Vulnerability Exploited Following Public PoC Release
A critical vulnerability in Fortinet’s FortiWeb application firewall, identified as CVE-2025-25257 with a CVSS score of 9.6, has been actively exploited in the wild following […]
Hackers Exploit GitHub Repositories to Distribute Amadey Malware and Data Stealers
In April 2025, cybersecurity researchers identified a sophisticated campaign where threat actors utilized public GitHub repositories to host and distribute malicious payloads, notably the Amadey […]
From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware
In today’s digital landscape, IT disruptions are becoming increasingly common, prompting organizations to move beyond traditional data backup methods toward comprehensive cyber resilience strategies. This […]