A sophisticated cyberattack campaign has recently emerged, targeting the Tibetan community through culturally significant lures to distribute advanced malware. China-aligned threat actors are leveraging events […]
Month: June 2025
Escalating Cyber Threats Target MOVEit Transfer Systems: A Comprehensive Analysis
In recent months, a significant surge in cyberattacks has targeted MOVEit Transfer systems, a widely utilized managed file transfer (MFT) solution. This escalation underscores the […]
Critical Vulnerabilities in ControlID iDSecure Software Pose Significant Security Risks
The Cybersecurity and Infrastructure Security Agency (CISA) has recently issued a critical advisory concerning multiple vulnerabilities in ControlID’s iDSecure On-premises vehicle control software. These flaws, […]
Critical Privilege Escalation Vulnerability Discovered in IBM i Systems
A significant security vulnerability, identified as CVE-2025-36004, has been discovered in multiple versions of IBM i, potentially allowing attackers to escalate privileges through an unqualified […]
Advanced Techniques in Windows Registry Manipulation: Implications for Cybersecurity
Recent research has unveiled sophisticated methods for manipulating the Windows Registry using C++ programming, highlighting significant security vulnerabilities within Windows systems. This study not only […]
Critical Vulnerabilities in Cisco ISE Enable Remote Command Execution with Root Privileges
Cisco has identified and addressed two critical security vulnerabilities in its Identity Services Engine (ISE) and ISE Passive Identity Connector (ISE-PIC) that could allow unauthenticated […]
Cybercriminals Exploit Large Language Models to Enhance Hacking Capabilities
The cybersecurity landscape is undergoing a significant transformation as cybercriminals increasingly harness artificial intelligence (AI) technologies to bolster their illicit activities. Large Language Models (LLMs), […]
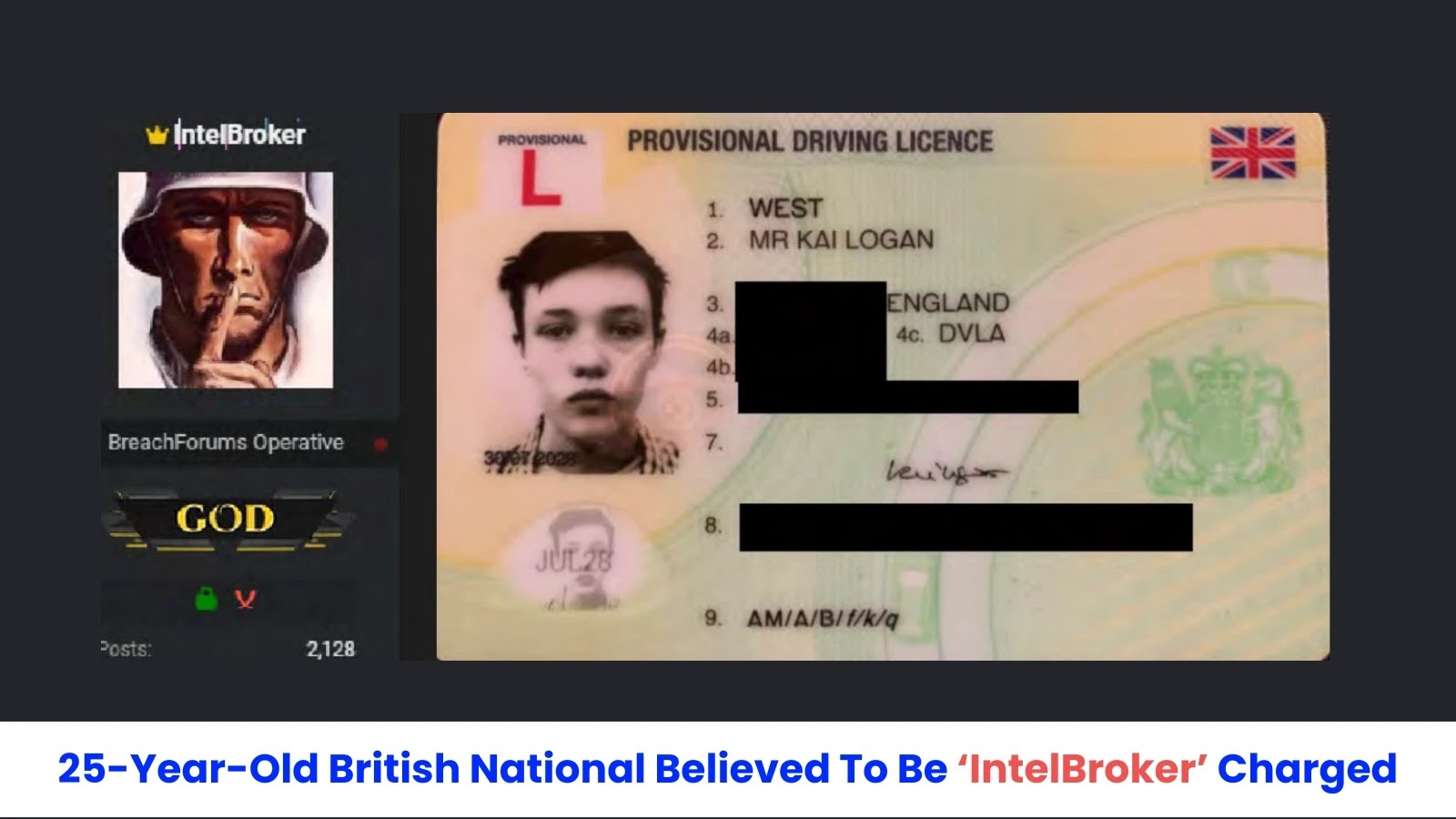
British Hacker IntelBroker Charged in $25 Million Cybercrime Operation
Federal prosecutors in the Southern District of New York have charged 25-year-old British national Kai West, known online as IntelBroker, with orchestrating a sophisticated cybercriminal […]
Iranian Cyber Espionage Campaign Targets High-Profile Individuals Through Sophisticated Spear-Phishing Attacks
A sophisticated Iranian cyber espionage campaign has resurfaced with renewed intensity, targeting high-profile figures through meticulously crafted spear-phishing operations that impersonate major email providers, including […]
Exploiting nOAuth Vulnerability in Microsoft Entra ID: A Pathway to Full Account Takeover
A critical security flaw, termed nOAuth, has been identified within Microsoft Entra ID’s authentication processes, posing a significant risk to enterprise SaaS applications. This vulnerability […]