In the rapidly evolving landscape of artificial intelligence, ensuring the safety and reliability of Large Language Models (LLMs) has become paramount. Recent research has unveiled […]
Day: June 24, 2025
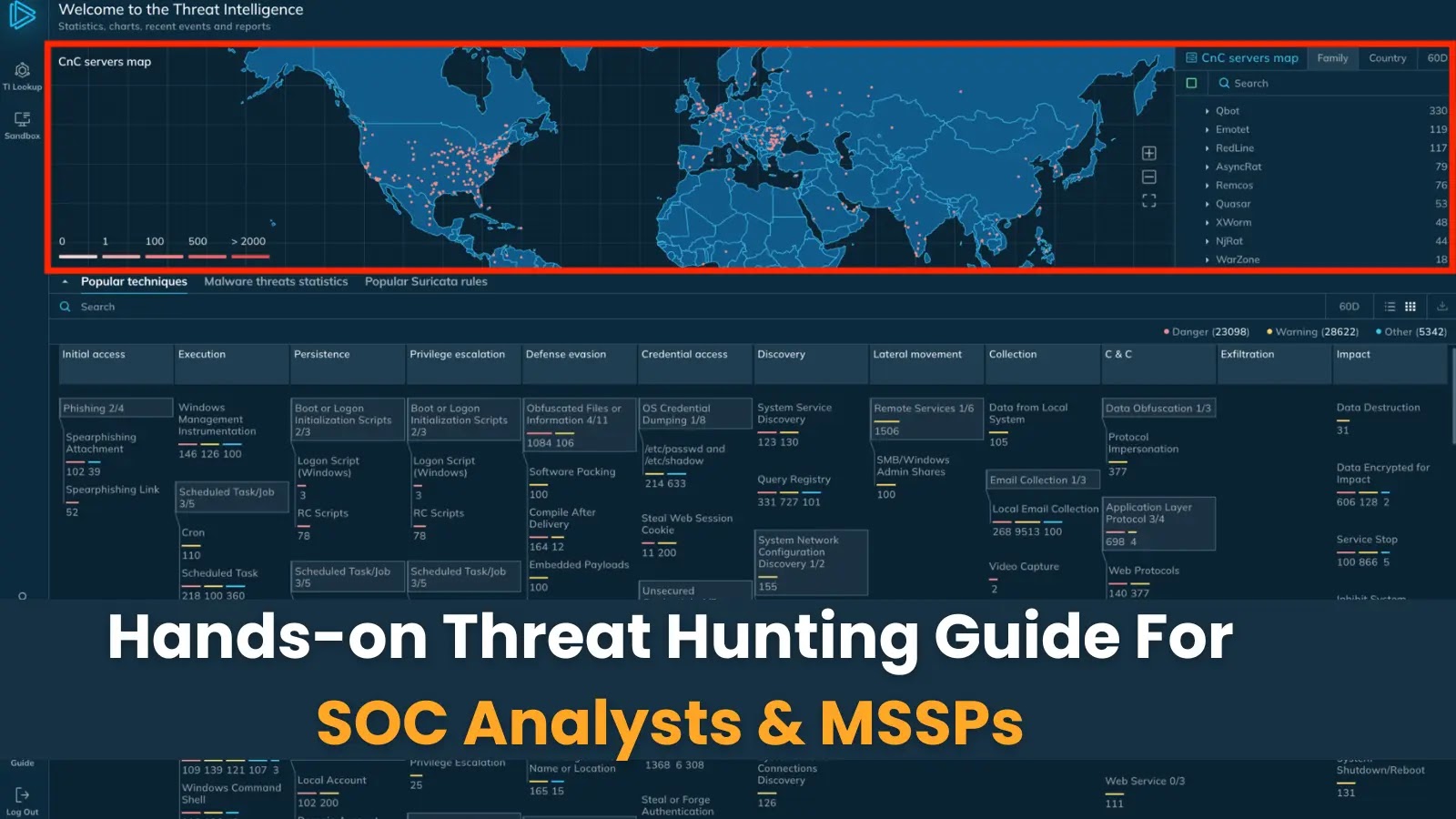
Hands-On Cybersecurity Threat Hunting Guide for SOC Analysts and MSSPs
In the ever-evolving landscape of cyber threats, Security Operations Center (SOC) analysts and Managed Security Service Providers (MSSPs) must adopt proactive threat-hunting strategies to stay […]
McLaren Health Care Data Breach Exposes Personal Information of 743,000 Individuals
McLaren Health Care, a prominent healthcare provider headquartered in Grand Blanc, Michigan, has reported a significant data breach that compromised the personal information of 743,131 […]
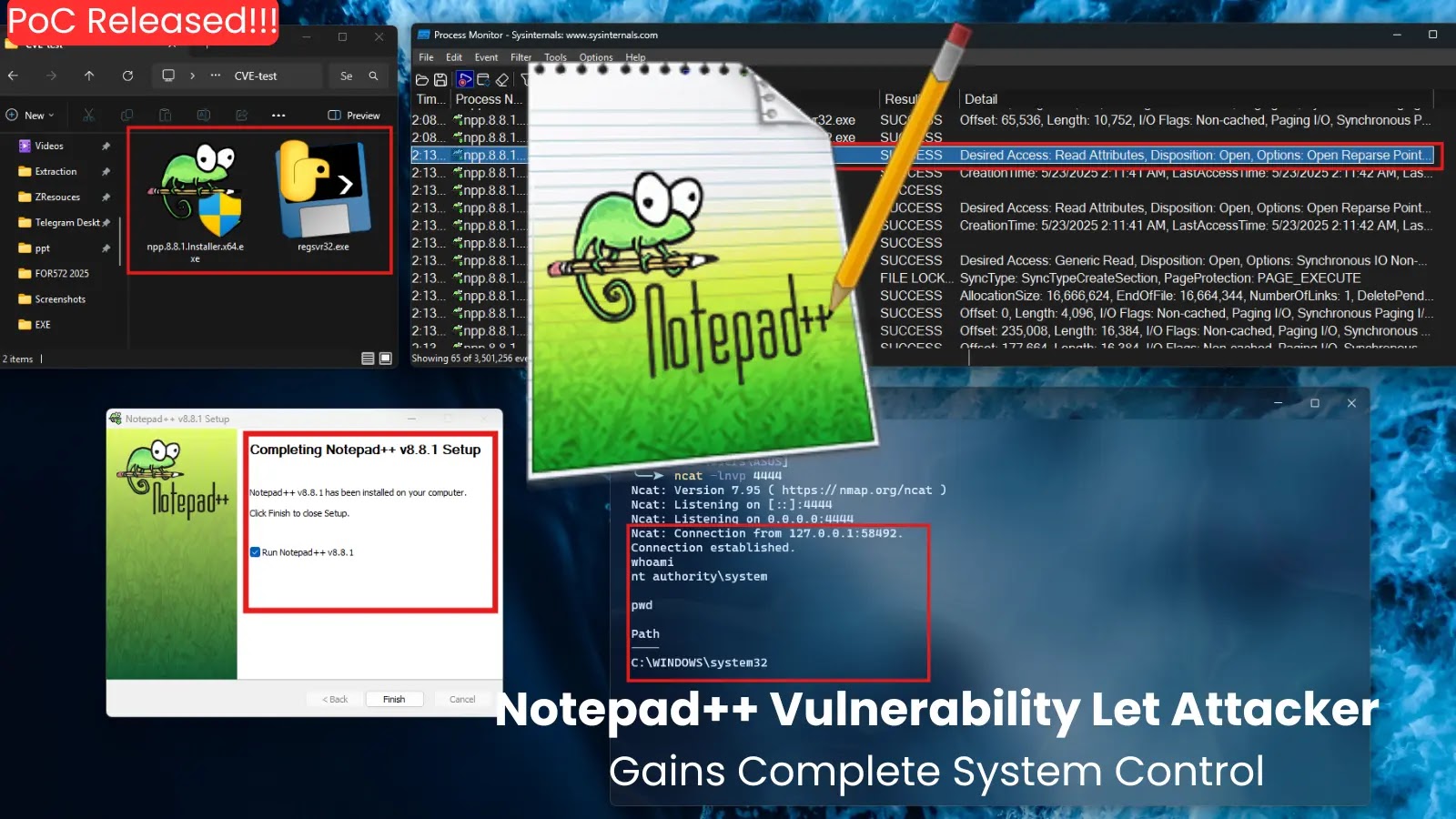
Critical Notepad++ Vulnerability Exposes Systems to Full Compromise
A critical security vulnerability has been identified in Notepad++ version 8.8.1, potentially allowing attackers to gain complete control over affected systems. This flaw, designated as […]
China-Linked ‘LapDogs’ Cyber Espionage Campaign Exploits Over 1,000 SOHO Devices
A sophisticated cyber espionage campaign, attributed to a China-linked group, has been identified targeting over 1,000 Small Office/Home Office (SOHO) devices worldwide. This operation, known […]
North Korean Hackers Exploit Fake Zoom Applications to Execute System Takeover Commands
In a sophisticated cyberattack campaign, North Korean-affiliated hackers are targeting professionals by deploying counterfeit Zoom applications designed to execute system takeover commands. This operation combines […]
Introducing the OWASP AI Testing Guide: A Comprehensive Framework for Securing AI Applications
As artificial intelligence (AI) becomes increasingly integrated into critical sectors such as healthcare, finance, and cybersecurity, the need for robust security measures tailored to AI […]
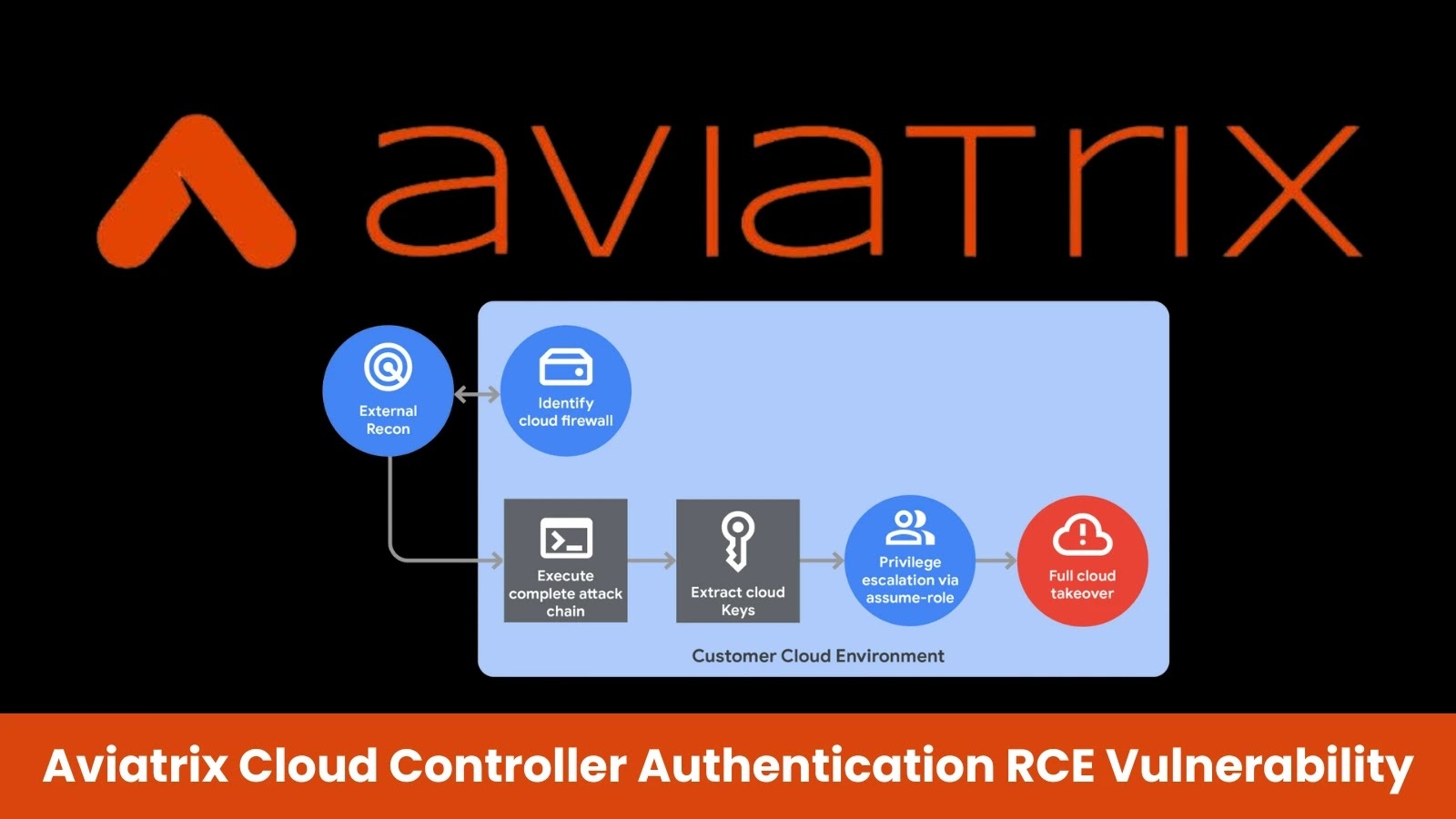
Critical Vulnerabilities in Aviatrix Controller Pose Severe Risks to Cloud Environments
Recent discoveries have unveiled two critical vulnerabilities in the Aviatrix Controller, a pivotal component in cloud networking that facilitates connectivity across various vendors and regions. […]
Sophisticated DMV-Themed Phishing Campaign Targets U.S. Citizens
In May 2025, a sophisticated phishing campaign emerged, targeting U.S. citizens by impersonating state Department of Motor Vehicles (DMV) agencies. This large-scale operation combined SMS […]
Critical Vulnerability in Xiaomi’s Interoperability App Exposes Devices to Unauthorized Access
A significant security flaw has been identified in Xiaomi’s Interoperability Application, potentially compromising millions of devices worldwide. This vulnerability, designated as CVE-2024-45347, has been assigned […]