WhatsApp has unveiled a groundbreaking feature called Message Summaries, designed to help users quickly catch up on unread messages through artificial intelligence. Announced on June […]
Month: June 2025
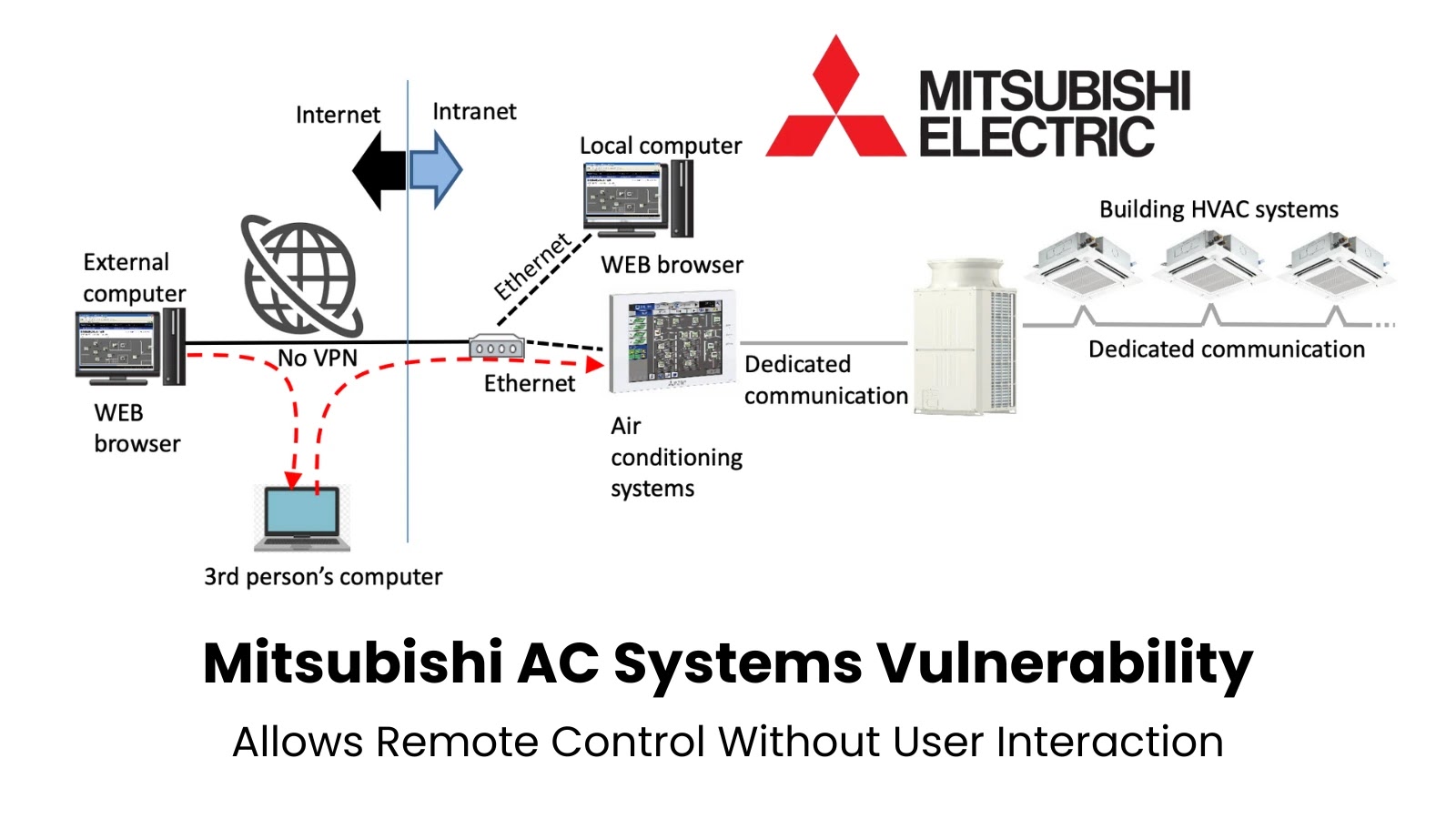
Critical Vulnerability in Mitsubishi Electric Air Conditioning Systems Enables Remote Control Without User Interaction
Mitsubishi Electric has recently disclosed a significant security vulnerability affecting 27 models of its air conditioning systems. This flaw, identified as CVE-2025-3699, allows remote attackers […]
Blind Eagle’s Persistent Cyber Assaults on Latin American Institutions
Since 2018, the advanced persistent threat (APT) group known as Blind Eagle, or APT-C-36, has been orchestrating sophisticated cyberattacks targeting critical sectors across Latin America, […]
ClickFix: The Evolving Social Engineering Threat Targeting Multiple Platforms
In the ever-changing landscape of cybersecurity, a new and sophisticated social engineering technique known as ClickFix has emerged, posing significant risks to users across various […]
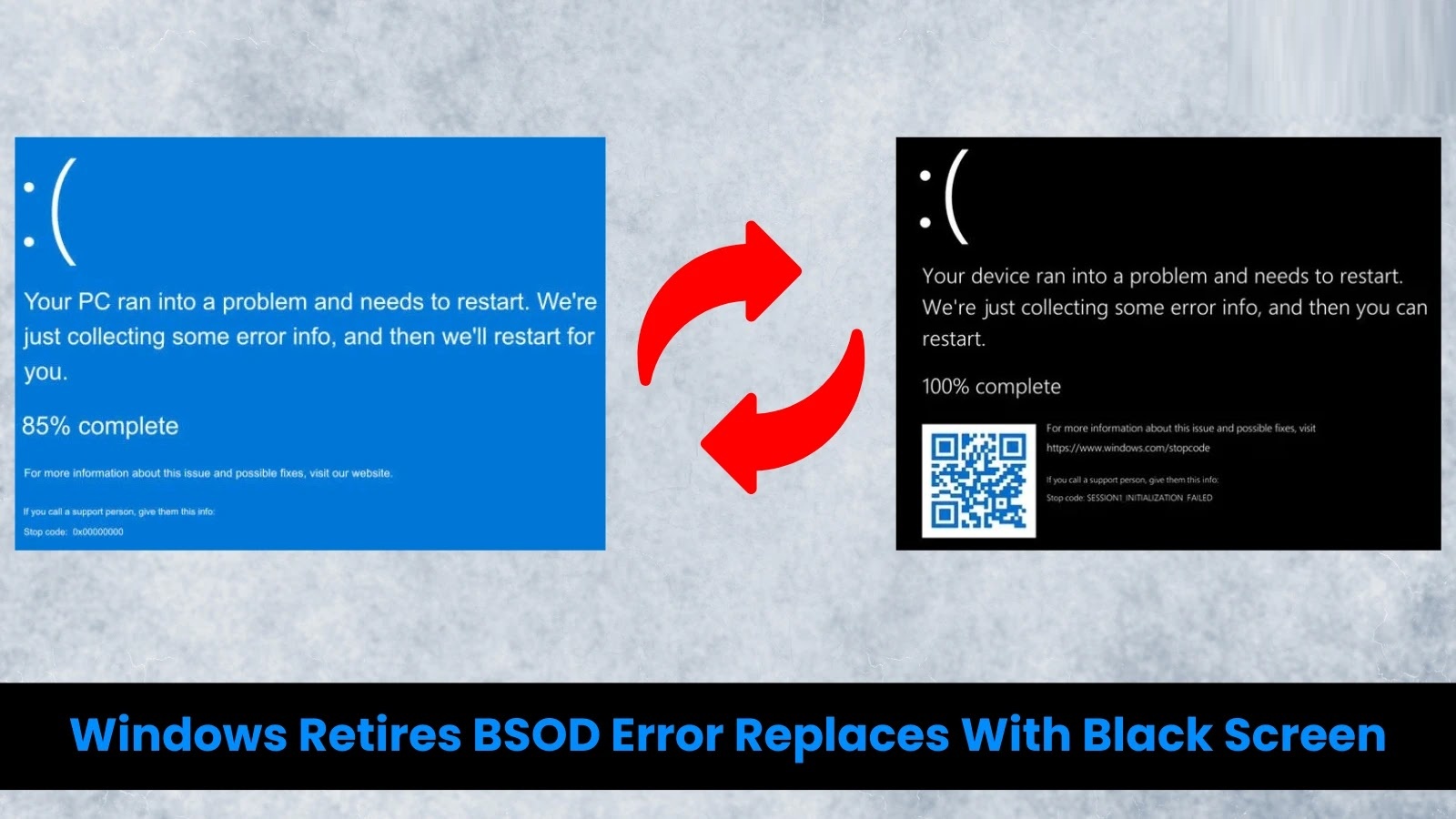
Microsoft Retires Iconic ‘Blue Screen of Death’ After Four Decades, Introduces Sleeker Black Version
After more than 40 years of signaling critical system errors to users, Microsoft is officially phasing out the notorious Blue Screen of Death (BSOD). The […]
Threat Actors Exploit Windows Task Scheduler to Maintain Persistent Access
In a recent cyberattack targeting critical national infrastructure in the Middle East, threat actors have demonstrated advanced techniques to maintain persistent access to compromised systems […]
Cybercriminals Exploit ClickFix Tactics to Deploy Malicious AppleScripts on macOS
A sophisticated malware campaign has recently emerged, targeting macOS users through deceptive ClickFix tactics. This method involves tricking individuals into executing malicious AppleScripts, leading to […]
Critical Pre-Authentication Vulnerability in MongoDB Servers Exposes Systems to Denial of Service Attacks
A significant security vulnerability, identified as CVE-2025-6709, has been discovered in MongoDB Server versions across the 6.0, 7.0, and 8.0 release branches. This flaw allows […]
Malicious Python Package ‘psslib’ Triggers Immediate Windows Shutdowns
A recent discovery has unveiled a malicious Python package named psslib on the Python Package Index (PyPI), designed to exploit Windows systems by initiating immediate […]
Let’s Encrypt Introduces Six-Day Validity Certificates and IP Address Support
In a significant move to enhance web security, Let’s Encrypt, the world’s largest certificate authority, has announced plans to introduce six-day validity certificates, commonly referred […]