During the recent Berkshire Hathaway annual shareholder meeting, Warren Buffett, the esteemed 94-year-old investor, announced his forthcoming retirement as CEO by the end of 2025. […]
Month: May 2025
Backbone Pro: The Ultimate Universal Gaming Controller for Seamless Cross-Platform Play
Backbone has unveiled the Backbone Pro, a cutting-edge gaming controller engineered to deliver a seamless gaming experience across a multitude of devices, including smartphones, tablets, […]
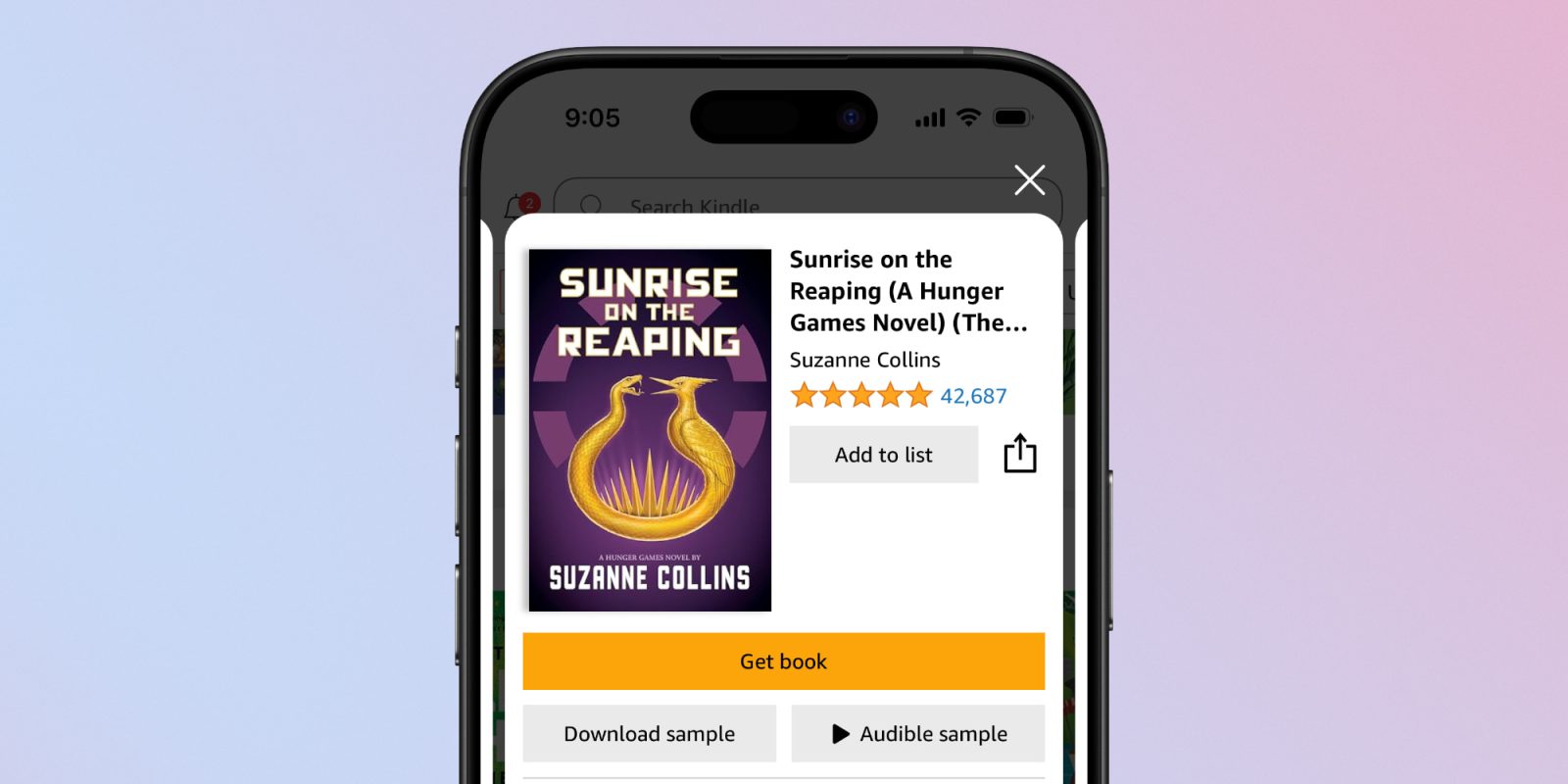
Kindle’s iOS App Enhances Book Purchasing Experience on iPhone and iPad
In a significant development for digital readers, Amazon’s Kindle app for iOS has introduced a new feature that simplifies the process of purchasing e-books on […]
[May-06-2025] Daily Cybersecurity Threat Report
1. Executive Summary This report details significant cybersecurity incidents reported within the last 24 hours, providing contextual analysis of the threat actors involved and their […]
Critical Vulnerability in Apache Parquet Java Allows Arbitrary Code Execution
A significant security vulnerability has been identified in Apache Parquet Java, a widely used columnar storage format within big data ecosystems. This flaw, designated as […]
Critical ‘SonicBoom’ Attack Chain Enables Remote Authentication Bypass and Administrative Control
A newly identified attack sequence, termed SonicBoom, poses a significant threat by allowing remote attackers to circumvent authentication protocols and gain administrative control over enterprise […]
Chimera Malware: A New Era of Cyber Threats Outsmarting Traditional Defenses
In early 2025, a formidable cyber threat emerged, known as Chimera, marking a significant advancement in malware sophistication. This malware’s debut was marked by an […]
LUMMAC.V2 Stealer Exploits ClickFix Technique to Deceive Users into Executing Malicious Commands
Cybersecurity researchers have recently uncovered a sophisticated evolution of the LUMMAC credential-stealing malware, now rewritten from C to C++ and operating with enhanced capabilities. This […]
Luna Moth’s Evolving Phishing Tactics: Weaponized Helpdesk Domains Targeting Legal and Financial Sectors
The cybercriminal group known as Luna Moth, also referred to as Silent Ransom Group, UNC3753, and Storm-0252, has intensified its phishing campaigns since March 2025, […]
Hackers Exploit SS7 Vulnerability to Intercept SMS and Track Phones
A significant security flaw within the Signaling System 7 (SS7) protocol has surfaced, enabling cybercriminals to intercept SMS messages and monitor mobile phone locations in […]


![[May-06-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)





