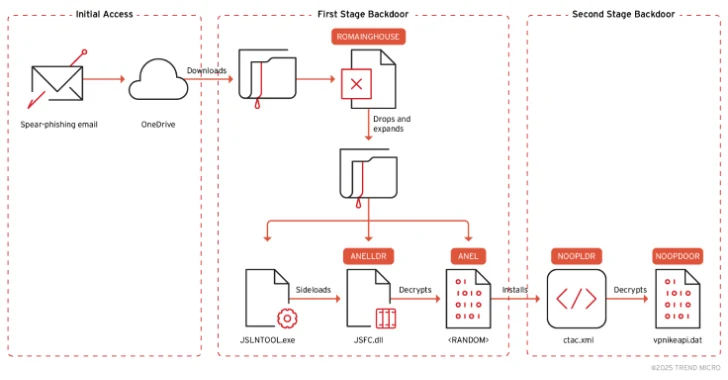
In a recent and sophisticated cyber espionage campaign, Iranian state-sponsored hackers have been identified leveraging a counterfeit website that mimics a reputable German modeling agency. […]
Month: May 2025
Microsoft’s New OneDrive Feature Raises Security Concerns Over Default Sync of Personal and Corporate Accounts
In May 2025, Microsoft introduced a new feature in OneDrive titled Prompt to Add Personal Account to OneDrive Sync. This update allows users to synchronize […]
Analyzing Browser Privacy: Identifying the Most Data-Collecting Web Browsers
In today’s digital landscape, web browsers serve as essential tools for accessing the internet. However, they also function as conduits for data collection, capturing user […]
The Evolution and Impact of Ransomware-as-a-Service (RaaS) on Global Cybersecurity
In recent years, the cybersecurity landscape has undergone a significant transformation with the emergence of Ransomware-as-a-Service (RaaS). This model has revolutionized cybercrime by enabling individuals […]
Critical macOS Remote Code Execution Vulnerability CVE-2024-44236: Analysis and Mitigation
A significant security flaw, designated as CVE-2024-44236, has been identified in Apple’s macOS operating system. This vulnerability, with a Common Vulnerability Scoring System (CVSS) score […]
Microsoft Bookings Vulnerability Exposes Organizations to Impersonation and Phishing Attacks
A critical security flaw has been identified in Microsoft Bookings, a scheduling tool integrated within Microsoft 365, which could allow attackers to create unauthorized Entra […]
Cisco Addresses Critical CVE-2025-20188 Vulnerability in IOS XE Wireless Controllers
Cisco has recently released software updates to mitigate a critical security vulnerability identified as CVE-2025-20188 in its IOS XE Wireless Controller software. This flaw, assigned […]
Russian Hackers Exploit ClickFix Tactics to Deploy LOSTKEYS Malware
In recent developments, the Russian state-sponsored cyber group known as COLDRIVER has been identified utilizing a sophisticated social engineering technique called ClickFix to distribute a […]
MirrorFace Intensifies Cyber Espionage Efforts Against Japan and Taiwan
In March 2025, cybersecurity researchers identified a series of sophisticated cyber espionage activities targeting government agencies and public institutions in Japan and Taiwan. These operations […]
Tesla’s ‘Robotaxi’ and ‘Cybercab’ Trademarks Face Challenges Ahead of June Launch
Tesla’s ambitious plans to revolutionize urban transportation with its autonomous ride-hailing services have encountered significant trademark obstacles. The U.S. Patent and Trademark Office (USPTO) recently […]