The LockBit ransomware group, notorious for its extensive cybercriminal activities, has been implicated in exploiting 20 critical vulnerabilities across various platforms and technologies. This revelation […]
Month: May 2025
Hackers Exploit PDF Invoices to Deploy Cross-Platform Malware
Cybercriminals are increasingly leveraging PDF invoices as a vector to distribute sophisticated malware across multiple operating systems, including Windows, Linux, and macOS. This method exploits […]
Hackers Exploit Windows Remote Management for Stealthy Lateral Movement in Active Directory
Cybersecurity experts have identified a growing trend where threat actors exploit Windows Remote Management (WinRM) to navigate Active Directory (AD) environments stealthily. This technique allows […]
Cybercriminals Exploit Multimedia Files in Sophisticated Vishing Attacks
In early 2025, cybersecurity researchers identified a novel vishing (voice phishing) campaign where cybercriminals utilize multimedia file formats to bypass security systems and deceive victims. […]
Chinese Hackers Exploit Critical SAP Vulnerability CVE-2025-31324 to Deploy Golang-Based SuperShell
A sophisticated cyber threat group, identified as Chaya_004 and believed to be operating from China, has been actively exploiting a critical vulnerability in SAP NetWeaver […]
Malicious npm Packages Compromise Over 3,200 Cursor Users, Stealing Credentials and Installing Backdoors
In a recent cybersecurity development, researchers have identified three malicious npm packages specifically targeting the macOS version of Cursor, a widely-used AI-powered source code editor. […]
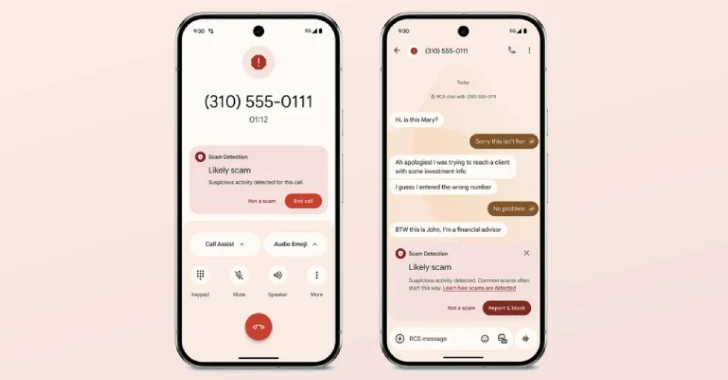
Google Enhances Security with On-Device AI to Combat Scams in Chrome and Android
In a significant move to bolster user security, Google has introduced advanced artificial intelligence (AI) features designed to detect and prevent scams across its Chrome […]
Beyond Vulnerability Management: Rethinking Cybersecurity Strategies
In the ever-evolving landscape of cybersecurity, organizations have traditionally relied on the Common Vulnerabilities and Exposures (CVE) system to identify and address security flaws. However, […]
Securing AI Agents: Essential Strategies to Protect Your Business
Artificial Intelligence (AI) agents are revolutionizing business operations by automating tasks, enhancing customer interactions, and streamlining processes. However, as these agents become more integrated into […]
Initial Access Brokers Exploit Brazilian Executives via NF-e Spam and RMM Software
Cybersecurity researchers have identified a sophisticated campaign targeting Portuguese-speaking users in Brazil, particularly C-level executives and financial and human resources personnel across various industries, including […]