A recently identified security vulnerability in Apache Tomcat’s Common Gateway Interface (CGI) servlet could enable attackers to bypass established security constraints under specific conditions. This […]
Day: May 30, 2025
SentinelOne Restores Services After Global Platform Outage
On May 29, 2025, SentinelOne, a prominent cybersecurity firm specializing in AI-driven threat detection, experienced a significant global platform outage that disrupted services for commercial […]
ConnectWise Breach: Nation-State Actors Compromise Systems to Access Customer Data
On May 28, 2025, ConnectWise, a prominent provider of software solutions for managed service providers (MSPs), disclosed a security breach within its internal systems. The […]
Ensuring Data Security in Cloud Storage and Collaboration Platforms
The rapid adoption of cloud technologies has revolutionized how organizations store and share data. However, this shift has also introduced significant security challenges. Recent statistics […]
CISA Issues Five Critical ICS Advisories Highlighting Vulnerabilities in Industrial and Medical Systems
On May 29, 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released five urgent advisories addressing critical vulnerabilities in Industrial Control Systems (ICS). These […]
Cybercriminals Exploit Fake CAPTCHA to Deploy EDDIESTEALER Malware
In a recent development, cybersecurity experts have identified a sophisticated malware campaign that utilizes deceptive CAPTCHA verification pages to distribute a newly discovered Rust-based infostealer […]
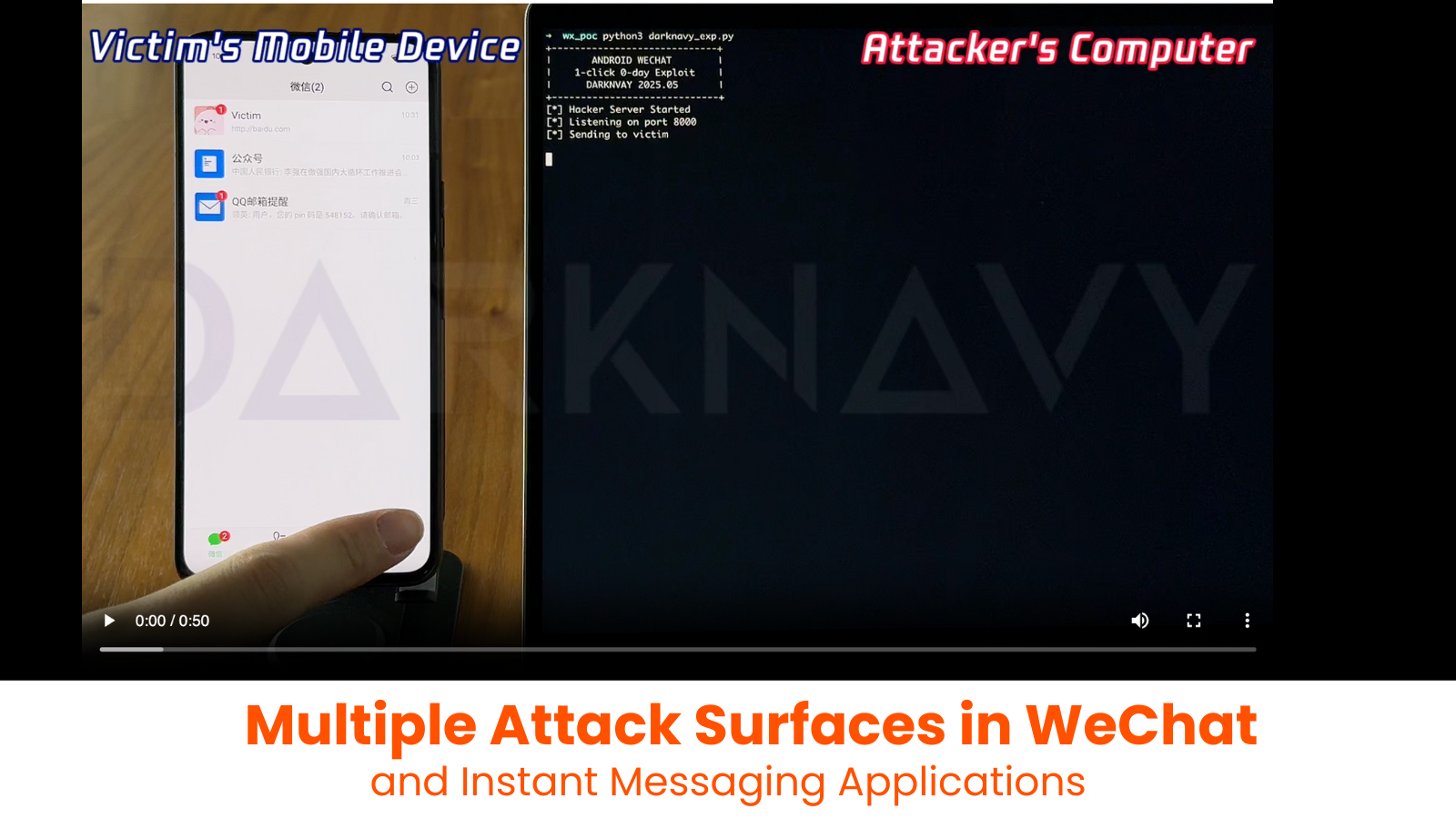
Emerging Threats in Instant Messaging: WeChat’s Vulnerabilities and the Need for Enhanced Security
Instant messaging (IM) applications such as WeChat, WhatsApp, Telegram, and QQ have become integral to daily communication, connecting billions globally. However, their widespread adoption has […]
Critical Cisco IOS XE Vulnerability Enables Remote Code Execution: PoC Released
A critical security vulnerability has been identified in Cisco’s IOS XE Wireless Controller Software, posing a significant threat to enterprise networks. Security researchers have released […]
North Korean Operatives Exploit Legitimate Software to Evade Detection in Cyber Espionage Campaigns
In a sophisticated cyber espionage campaign throughout 2024, North Korean operatives have demonstrated the ability to exploit legitimate software tools to establish undetectable remote access […]
New Browser-in-the-Middle Attack Exploits Safari’s Fullscreen API to Steal Credentials
A sophisticated Browser-in-the-Middle (BitM) attack has emerged, specifically targeting users of Apple’s Safari browser by exploiting vulnerabilities in its Fullscreen API implementation. This attack enables […]