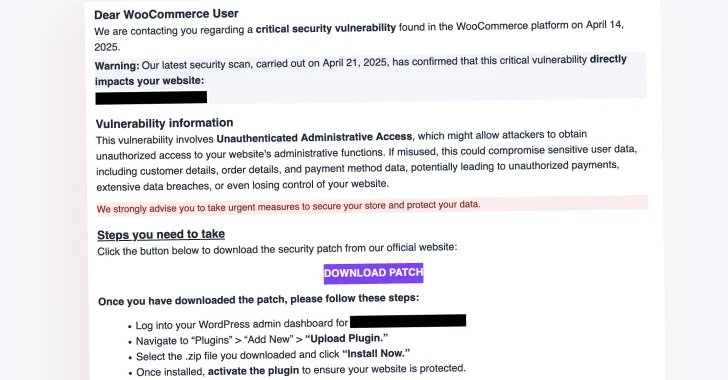
Cybersecurity experts have identified a large-scale phishing campaign specifically targeting WooCommerce users. This deceptive operation involves sending fake security alerts that prompt recipients to download a critical patch, which, in reality, installs a backdoor on their websites.
Patchstack, a WordPress security firm, has characterized this campaign as highly sophisticated. It appears to be a variant of a similar attack observed in December 2023, where attackers used counterfeit Common Vulnerabilities and Exposures (CVE) notifications to compromise WordPress sites. The consistent tactics, such as the phishing email content, the design of the fraudulent web pages, and the methods used to conceal the malware, suggest that the same threat actor may be responsible for both campaigns.
The phishing emails claim that the targeted websites are affected by a non-existent Unauthenticated Administrative Access vulnerability. They urge recipients to visit a phishing website that employs an Internationalized Domain Name (IDN) homograph attack to mimic the official WooCommerce site. Specifically, the attackers use the domain woocommėrce[.]com, substituting the letter e with ė to deceive users.
Upon clicking the Download Patch link in the email, victims are redirected to this spoofed WooCommerce Marketplace page, where they can download a ZIP archive named authbypass-update-31297-id.zip. They are then instructed to install this file as they would a standard WordPress plugin. However, this action initiates a series of malicious activities:
1. Creation of a New Administrator Account: The malware sets up a new administrator-level user with an obfuscated username and a randomized password. It also establishes a cron job that runs every minute to maintain this account.
2. Data Transmission to External Servers: The compromised site sends an HTTP GET request to an external server (woocommerce-services[.]com/wpapi), transmitting information about the new administrator account and the infected website’s URL.
3. Download and Execution of Additional Payloads: The malware fetches a second-stage obfuscated payload from another server (woocommerce-help[.]com/activate or woocommerce-api[.]com/activate). This payload includes multiple web shells, such as P.A.S.-Fork, p0wny, and WSO, which provide the attackers with remote control over the website.
4. Concealment of Malicious Components: The malware hides the rogue plugin from the list of installed plugins and conceals the newly created administrator account to evade detection.
The ultimate goal of this campaign is to grant attackers remote access to the compromised websites. This access enables them to inject spam content, display unauthorized advertisements, redirect visitors to malicious sites, enlist the server into a botnet for Distributed Denial-of-Service (DDoS) attacks, or even encrypt server resources as part of a ransomware scheme.
Recommendations for WooCommerce Users:
– Vigilance Against Phishing Attempts: Be cautious of unsolicited emails claiming to be from WooCommerce or other trusted sources, especially those urging immediate action.
– Verify Sources: Before downloading any updates or patches, confirm their authenticity by visiting the official WooCommerce website directly.
– Regular Security Audits: Periodically review your website for unauthorized plugins or administrator accounts.
– Keep Software Updated: Ensure that your WordPress installation, themes, and plugins are up-to-date to protect against known vulnerabilities.
By implementing these measures, WooCommerce users can enhance their website security and reduce the risk of falling victim to such sophisticated phishing campaigns.