In a recent cybersecurity development, researchers have identified a threat actor, dubbed ViciousTrap, who has compromised approximately 5,300 network edge devices across 84 countries. This actor has transformed these devices into a vast honeypot network, primarily by exploiting a critical vulnerability in Cisco Small Business routers.
Exploitation of Cisco Vulnerability
The vulnerability in question, CVE-2023-20118, affects several Cisco Small Business router models, including RV016, RV042, RV042G, RV082, RV320, and RV325. By leveraging this flaw, ViciousTrap has managed to infiltrate a significant number of devices, with the highest concentration of infections—850 compromised units—located in Macau.
Infection Mechanism: The NetGhost Script
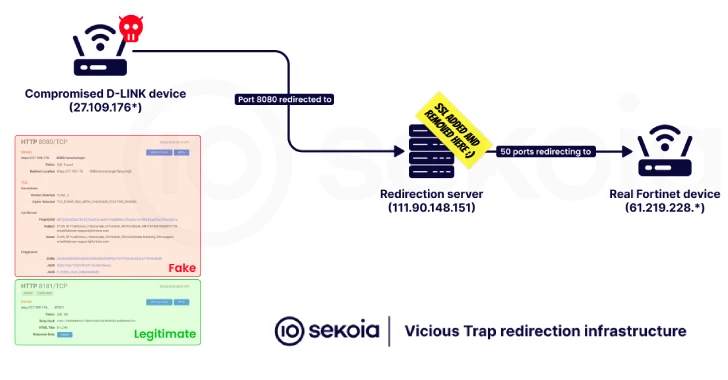
The attack sequence initiated by ViciousTrap involves the deployment of a shell script known as NetGhost. This script redirects incoming traffic from specific ports on the compromised routers to infrastructure controlled by the attacker. Such redirection enables the interception and potential manipulation of network flows, effectively positioning the attacker as an intermediary observer.
Potential Objectives and Implications
While the exact motives behind ViciousTrap’s operations remain uncertain, the establishment of this extensive honeypot network suggests several possible objectives:
– Surveillance of Exploitation Attempts: By monitoring incoming traffic, the attacker can observe various exploitation techniques employed by other threat actors, potentially gathering intelligence on new or undisclosed vulnerabilities.
– Collection of Zero-Day Exploits: The honeypot setup may serve as a means to collect non-public or zero-day exploits, which can be analyzed and potentially weaponized for future attacks.
– Unauthorized Access Utilization: Access obtained by other threat actors could be repurposed by ViciousTrap, allowing them to exploit previously compromised systems for their own objectives.
Broader Targeting Beyond Cisco Devices
ViciousTrap’s activities are not limited to Cisco routers. The threat actor has been observed compromising a diverse range of internet-facing equipment, including:
– SOHO Routers: Devices from brands such as Araknis Networks, ASUS, D-Link, Linksys, and QNAP.
– SSL VPNs: Virtual Private Network appliances that provide secure remote access.
– DVRs: Digital Video Recorders used for surveillance systems.
– BMC Controllers: Baseboard Management Controllers that manage hardware interfaces.
This expansive targeting indicates a strategic effort to build a comprehensive honeypot infrastructure capable of monitoring a wide array of network environments.
Technical Details of the Attack Chain
The attack chain employed by ViciousTrap is methodical and involves multiple stages:
1. Initial Exploitation: The attacker exploits CVE-2023-20118 to execute a shell script via the `ftpget` utility on the compromised device.
2. Deployment of Wget: The initial script contacts an external server to download the `wget` binary, a tool used for retrieving files from the web.
3. Secondary Exploitation: The Cisco vulnerability is exploited a second time to execute a second-stage script retrieved using the previously installed `wget`.
4. Execution of NetGhost: The second-stage script, known as NetGhost, is executed. This script is responsible for redirecting network traffic from the compromised device to the attacker’s infrastructure, facilitating adversary-in-the-middle (AitM) attacks.
5. Self-Removal: To minimize forensic traces, NetGhost includes functionality to remove itself from the compromised host after execution.
Geographical Distribution and Infrastructure
All observed exploitation attempts have originated from a single IP address, 101.99.91[.]151, with initial activity traced back to March 2025. Subsequent activities in April 2025 involved the repurposing of an undocumented web shell previously associated with the PolarEdge botnet, indicating potential overlaps or shared tactics between different threat actors.
Further exploitation efforts in May 2025 targeted ASUS routers from a different IP address, 101.99.91[.]239. Notably, all IP addresses linked to these campaigns are located in Malaysia and are part of an Autonomous System (AS45839) operated by the hosting provider Shinjiru.
Indicators of Chinese-Origin Threat Actor
Several factors suggest that ViciousTrap may be of Chinese-speaking origin:
– Infrastructure Overlaps: There is a weak overlap with infrastructure associated with GobRAT, a malware family linked to Chinese threat actors.
– Traffic Redirection Patterns: The redirection of traffic to numerous assets in Taiwan and the United States aligns with known tactics employed by Chinese cyber espionage groups.
Recommendations for Mitigation
Given the sophisticated nature of ViciousTrap’s operations and the widespread exploitation of CVE-2023-20118, it is imperative for organizations to take proactive measures:
– Patch Management: Ensure that all network devices, especially those facing the internet, are updated with the latest firmware and security patches.
– Disable Unnecessary Services: If remote management interfaces are not essential, disable them to reduce the attack surface.
– Network Segmentation: Implement network segmentation to limit the potential impact of a compromised device.
– Monitor Network Traffic: Regularly monitor network traffic for unusual patterns or unauthorized access attempts.
– Incident Response Planning: Develop and regularly update incident response plans to address potential breaches promptly.
Conclusion
The emergence of ViciousTrap underscores the evolving tactics of threat actors who exploit known vulnerabilities to establish extensive surveillance networks. By transforming compromised devices into honeypots, these actors can gather intelligence on exploitation techniques, collect zero-day exploits, and potentially repurpose unauthorized access for further malicious activities. Organizations must remain vigilant, promptly address known vulnerabilities, and implement robust security measures to mitigate such threats.