Cybersecurity experts have recently identified significant developments in the XorDDoS malware, a notorious distributed denial-of-service (DDoS) Trojan that has been targeting Linux systems for over a decade. Between November 2023 and February 2025, 71.3% of XorDDoS attacks were directed at the United States, underscoring the persistent threat this malware poses.
Joey Chen, a researcher at Cisco Talos, highlighted the escalating prevalence of XorDDoS from 2020 to 2023. This surge is attributed not only to the malware’s widespread distribution but also to an increase in malicious DNS requests associated with its command-and-control (C2) infrastructure. Notably, XorDDoS has expanded its reach beyond traditional Linux machines to target Docker servers, converting infected hosts into bots.
The geographical distribution of compromised devices reveals that nearly 42% are located in the United States, followed by Japan, Canada, Denmark, Italy, Morocco, and China. This global spread indicates the malware’s extensive impact across various regions.
XorDDoS is known for its ability to infect Linux devices and transform them into zombies, which attackers can control to execute malicious tasks remotely, primarily DDoS attacks. The malware employs XOR-based encryption for communication with its C2 servers, enhancing its stealth and persistence.
The primary method of initial access involves conducting Secure Shell (SSH) brute-force attacks to obtain valid credentials. Once access is gained, the malware is downloaded and installed on vulnerable Internet of Things (IoT) devices and other internet-connected systems. To maintain persistence, XorDDoS sets up an embedded initialization script and a cron job, ensuring it launches automatically at system startup. It also uses the XOR key BB2FA36AAA9541F0 to decrypt a configuration within itself, extracting the IP addresses necessary for C2 communication.
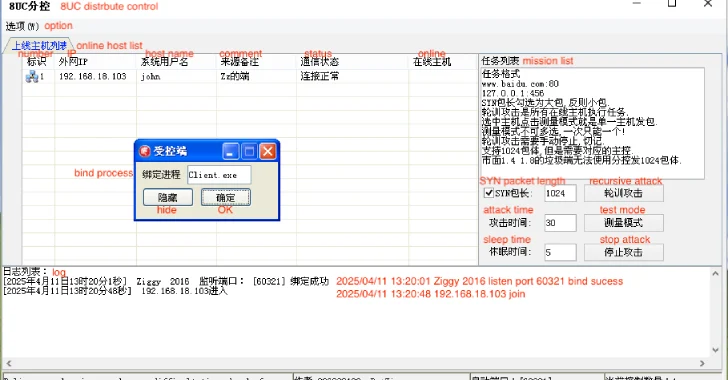
In 2024, Talos observed a new version of the XorDDoS sub-controller, referred to as the VIP version, along with its corresponding central controller and a builder. This development suggests that the malware’s infrastructure is evolving, potentially indicating that these tools are being advertised for sale. The central controller manages multiple XorDDoS sub-controllers and sends DDoS commands simultaneously, with each sub-controller commandeering a botnet of infected devices.
The language settings of the multi-layer controller, XorDDoS builder, and controller binding tool strongly suggest that the operators are Chinese-speaking individuals. This insight provides valuable context for understanding the origins and potential motivations behind the malware’s development and deployment.
The expansion of XorDDoS to target Docker servers is particularly concerning. By exploiting exposed Docker servers, the malware can infect all existing containers on the server, effectively converting them into bots for DDoS attacks. This method of propagation demonstrates the malware’s adaptability and the increasing sophistication of its operators.
The persistence mechanisms employed by XorDDoS are multifaceted. In addition to creating scheduled autorun tasks and configuring autorun services, the malware turns its process into a background service that runs independently of the current user session. This tactic helps it evade detection and termination by users, disguising itself as a legitimate process.
During dynamic analysis, researchers found that XorDDoS drops ELF executables with slight variations to its original file for persistence on the victim’s system. This self-replication behavior generates numerous malware executables during active periods of XorDDoS campaigns. Despite their high degree of similarity, these replicas can confuse file hash-based detection systems.
Between December 2022 and August 2023, over 26,000 such replicated malware samples were identified within victims’ systems, generated from approximately 800 initial samples. These malware samples infiltrated networks across various organizations globally, including industries such as semiconductor, telecom, transportation, finance, insurance, and retail.
The C2 network infrastructure of XorDDoS has also evolved. Attackers have migrated their offensive infrastructure to hosts running on legitimate public hosting services. Even though numerous security vendors have classified the C2 domains as malicious and barred them, active malware traffic directed to these new underlying IPs continues. This underscores the necessity of extending protection beyond merely blocking dedicated attacking hosts.
Given that the C2 IP addresses used in the XorDDoS campaign are shared web hosting infrastructure, definitively classifying isolated connections as malicious or benign becomes challenging. Therefore, multiple connections to these IP addresses within a brief time frame can serve as a better indicator of C2 traffic. This behavior strongly suggests C2 activity rather than legitimate network traffic.
To enhance detection capabilities, advanced signatures have been developed to detect malware activities involving non-dedicated attacking hosts. These signatures incorporate multiple network entities, enabling effective identification and mitigation of malware communication sessions that might otherwise evade detection based solely on single-entity analysis.
In conclusion, the XorDDoS Trojan continues to pose a significant threat to Linux systems worldwide. Its expansion to target Docker servers, the development of new controllers, and the evolution of its C2 infrastructure highlight the increasing sophistication of its operators. Organizations must remain vigilant, implementing robust security measures to detect and mitigate the risks associated with this persistent malware.