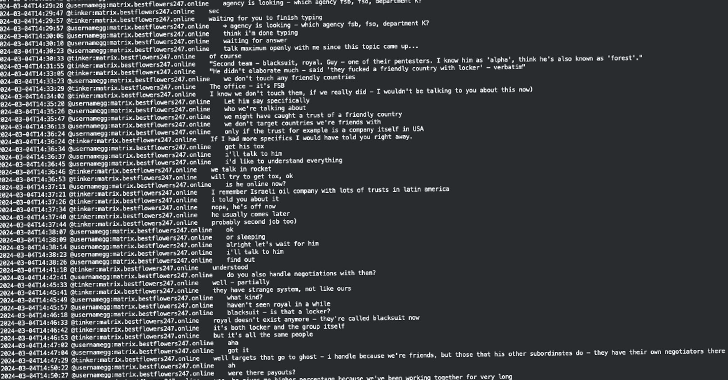
In March 2025, a significant leak of internal communications from the notorious Black Basta ransomware group has offered a rare glimpse into the operations of the cybercriminal organization. This leak has provided cybersecurity experts and law enforcement agencies with invaluable insights into how such groups operate, their motives, and their methods of conducting attacks.
Black Basta has been on the radar of cybersecurity experts for their involvement in numerous high-profile ransomware attacks. The group is known for targeting large corporations and demanding exorbitant ransom payments in exchange for the decryption of hijacked data. The leaked chat logs, which span several months, reveal the group’s strategies, internal conflicts, and their approach to selecting targets.
One of the most striking revelations from the leaked conversations is the meticulous planning that goes into each attack. The group discusses potential targets in detail, analyzing the financial standing of companies, the type of data they hold, and their perceived ability to pay a ransom. This suggests a highly organized and strategic approach rather than random attacks.
The conversations also shed light on the internal dynamics of the group. There are clear signs of hierarchy and designated roles within the organization. Some members are responsible for scanning networks and identifying vulnerabilities, while others handle negotiations and payment logistics. This division of labor highlights the professional nature of the group’s operations.
Furthermore, the chats reveal the group’s use of advanced technology and techniques to evade detection. They frequently discuss the use of sophisticated encryption methods and the deployment of custom-built malware to bypass security measures. This underscores the evolving nature of cyber threats and the need for organizations to continually update their security protocols.
Interestingly, the leaked chats also expose internal disputes and disagreements among group members. These range from arguments over the distribution of ransom payments to disagreements on the selection of targets. Such conflicts are indicative of the inherent challenges in maintaining cohesion within a criminal enterprise, particularly when significant sums of money are involved.
Despite these disputes, the group remains focused on its primary objective: financial gain through cybercrime. The chats indicate that members are constantly seeking new ways to maximize their earnings, whether through increasing ransom demands or exploring new types of cyberattacks.
The leak has prompted renewed efforts from international law enforcement to track down and apprehend members of Black Basta. Cybersecurity firms are also using the information to develop more effective defense strategies against ransomware attacks. The insights gained from these chats will likely aid in the prevention of future attacks and contribute to the broader understanding of organized cybercrime.
In response to this leak, security experts are urging organizations to enhance their cybersecurity measures. This includes regularly updating software, implementing robust data backup systems, and conducting comprehensive security audits. By doing so, companies can bolster their defenses against sophisticated ransomware groups like Black Basta.
The leaked communications of the Black Basta group provide a unique opportunity to understand the inner workings of a major ransomware operation. For cybersecurity professionals and businesses alike, these insights are invaluable in the ongoing battle against cybercrime. As ransomware attacks continue to rise, the information gleaned from such leaks is crucial in developing effective strategies to protect sensitive data and maintain operational integrity.