The Ukrainian Computer Emergency Response Team (CERT-UA) recently issued a critical warning regarding an escalating cyber-espionage campaign targeting Ukraine’s defense-industrial complex and military personnel. At the core of this sophisticated campaign is the Dark Crystal Remote Access Trojan (DCRat), which attackers have cleverly distributed through compromised Signal accounts, significantly amplifying their capability to deceive targeted individuals.
First identified in 2019, DCRat has matured over the years, becoming increasingly versatile and dangerous. Its modular design allows attackers flexibility, extending functionality through custom plugins that can be adapted to specific espionage missions. This malware can execute arbitrary commands on infected systems, enabling attackers to silently extract sensitive data, including usernames, passwords, internal military documents, strategic communications, and other classified materials.
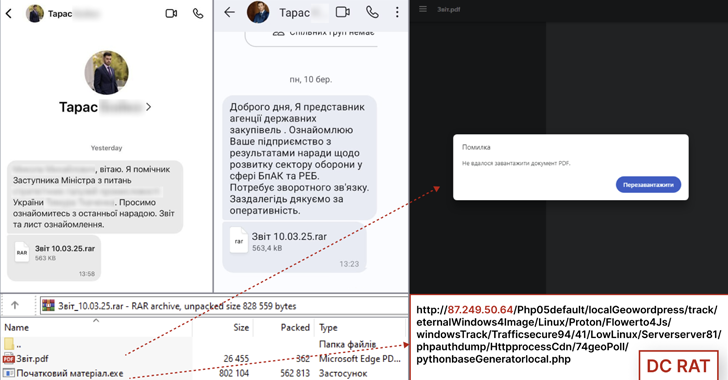
The recent spike in DCRat activity detected by CERT-UA began in March 2025, employing a notably cunning tactic involving the Signal messaging application—a platform previously trusted for secure and encrypted communications. Attackers are leveraging compromised Signal accounts belonging to legitimate Ukrainian defense personnel to distribute malicious files. These communications typically present themselves as routine messages containing purported meeting minutes or official military updates. The attachments, cleverly disguised as PDF documents within a compressed archive, actually harbor malware capable of infiltrating and compromising targeted systems.
Upon closer analysis, the infection mechanism reveals a highly sophisticated technique involving DarkTortilla, a .NET-based malware loader designed to evade detection through advanced encryption and obfuscation methods. Once opened, this loader silently executes and decrypts payloads, ultimately deploying the DCRat onto the victim’s device. The stealthy nature of this malware significantly complicates detection and remediation efforts, creating prolonged and covert access for cyber adversaries.
CERT-UA has linked this espionage operation directly to a threat group designated as UAC-0200, a sophisticated adversary active since mid-2024. This threat actor demonstrates clear strategic objectives, consistently focusing on sensitive areas such as unmanned aerial vehicles (UAVs), electronic warfare systems, and other advanced military technologies pivotal to Ukraine’s defensive capabilities. The targeted nature of the campaigns strongly indicates a direct intent to undermine and exploit Ukraine’s military preparedness and strategic positioning amid ongoing geopolitical tensions.
The implications of this cyber campaign extend beyond mere espionage. By infiltrating key defense infrastructure through trusted platforms like Signal, attackers aim not only to steal critical information but potentially to disrupt vital communications channels during times of crisis. Such threats underscore the growing vulnerabilities introduced by reliance on third-party messaging platforms, which attackers exploit due to lower security oversight compared to traditional military-grade communication channels.
CERT-UA emphasizes that preventing these cyber intrusions requires heightened vigilance at both the organizational and individual levels. Defense personnel should thoroughly verify message authenticity, even when communications appear to originate from known or trusted contacts. Unsolicited messages, especially those with attachments or embedded links, must be treated with extreme caution. Organizations within the defense sector should implement stringent policies surrounding the use of messaging applications, prioritizing secured and encrypted internal communication platforms wherever feasible.
Additionally, cybersecurity best practices, including multi-factor authentication (MFA), endpoint security solutions, regular software updates, and ongoing security education, are essential to mitigating the risks posed by sophisticated threats such as DCRat. Continuous employee training and awareness programs should be instituted, emphasizing the recognition of phishing attempts and other forms of social engineering, to reduce the likelihood of human error facilitating malware infections.
Furthermore, robust security protocols, including proactive threat detection and response capabilities, must be integrated into defense sector cybersecurity operations. The establishment of real-time monitoring and rapid response procedures enables swift identification and neutralization of threats before they can inflict substantial damage or gain extensive footholds within critical infrastructure.
The increasing frequency and sophistication of cyberattacks against Ukraine, particularly those involving the defense sector, highlight the ongoing necessity for international cybersecurity cooperation. Intelligence sharing among allies and global cybersecurity agencies can substantially improve the capacity to respond to, mitigate, and prevent complex cyber-espionage threats.
As the cyber landscape evolves, attackers continue exploiting novel techniques and vulnerabilities to infiltrate high-value targets. For Ukraine’s defense sector, vigilance, adaptability, and a robust cybersecurity posture remain essential. This recent attack involving DCRat delivered via compromised Signal accounts demonstrates that threat actors continually evolve their tactics, requiring constant adaptation and rigorous defense strategies to protect critical national security assets effectively.