In a sophisticated cyber espionage campaign that began in April 2024, a threat actor affiliated with Türkiye exploited a zero-day vulnerability in Output Messenger, an enterprise communication platform developed in India. This campaign targeted Kurdish military entities in Iraq, aiming to collect sensitive user data.
The Microsoft Threat Intelligence team identified this activity and attributed it to a group they track as Marbled Dust, also known by aliases such as Cosmic Wolf, Sea Turtle, Teal Kurma, and UNC1326. Active since at least 2017, Marbled Dust has a history of targeting public and private organizations across the Middle East and North Africa. In early 2024, the group expanded its operations to include attacks on telecommunications, media, internet service providers (ISPs), IT service providers, and Kurdish websites in the Netherlands.
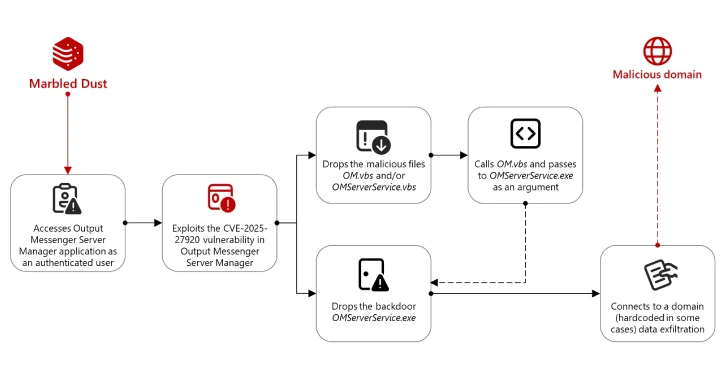
Microsoft’s analysis suggests that Marbled Dust conducted preliminary reconnaissance to identify targets using Output Messenger. Once identified, the group exploited a directory traversal vulnerability, designated as CVE-2025-27920, in Output Messenger version 2.0.62. This flaw allowed remote attackers to access or execute arbitrary files on the server. The vulnerability was addressed by the developer, Srimax, in December 2024 with the release of version 2.0.63. However, the company’s advisory did not mention any active exploitation of this flaw at the time.
The attack sequence initiated with Marbled Dust gaining authenticated access to the Output Messenger Server Manager application. The group likely employed techniques such as DNS hijacking or typosquatting to intercept credentials necessary for authentication. With access secured, the attackers collected user credentials and exploited CVE-2025-27920 to deploy malicious scripts and executables, including OM.vbs, OMServerService.vbs, and OMServerService.exe, onto the server.
The OMServerService.exe is a Golang-based backdoor designed to communicate with a hard-coded command-and-control (C2) domain, api.wordinfos[.]com, facilitating data exfiltration. On the client side, the installer extracted and executed both the legitimate OutputMessenger.exe and OMClientService.exe, another Golang backdoor connecting to the same C2 domain. This backdoor performed connectivity checks and sent unique identifiers of the victim’s machine to the C2 server. The server’s response was then executed using the Windows command prompt.
In one observed instance, a victim device with Output Messenger client software installed connected to an IP address previously associated with Marbled Dust, indicating likely data exfiltration.
Additionally, Microsoft discovered a reflected cross-site scripting (XSS) vulnerability in the same version of Output Messenger, designated as CVE-2025-27921. However, there is no evidence to suggest that this particular flaw has been exploited in real-world attacks.