In the ever-evolving landscape of cyber threats, a new Android malware-as-a-service (MaaS) platform named SuperCard X has surfaced, enabling cybercriminals to execute near-field communication (NFC) relay attacks. This sophisticated malware facilitates unauthorized transactions at point-of-sale (PoS) terminals and automated teller machines (ATMs) by intercepting and relaying NFC communications from compromised devices.
Targeted Campaigns and Distribution Methods
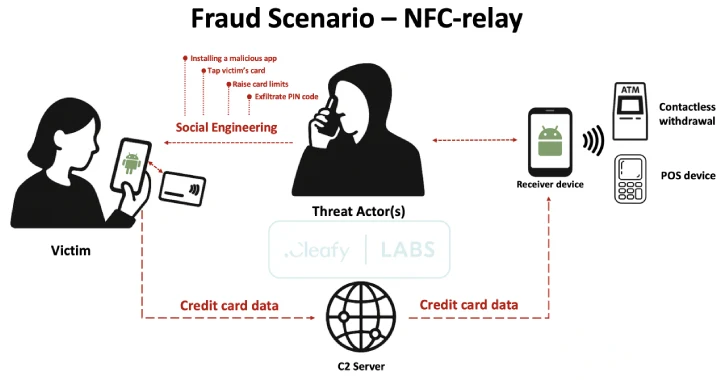
SuperCard X has been actively targeting customers of banking institutions and card issuers, particularly in Italy. The malware’s distribution is primarily conducted through deceptive social engineering tactics, including smishing (SMS phishing) and phone calls. Victims receive fraudulent messages impersonating bank security alerts, prompting them to call a specified number to address a suspicious transaction. This method, known as Telephone-Oriented Attack Delivery (TOAD), manipulates individuals into installing malicious applications under the guise of security software.
The malware is disseminated via three counterfeit applications:
– Verifica Carta (io.dxpay.remotenfc.supercard11)
– SuperCard X (io.dxpay.remotenfc.supercard)
– KingCard NFC (io.dxpay.remotenfc.supercard)
These applications are designed to appear legitimate, thereby increasing the likelihood of successful installation by unsuspecting users.
Operational Mechanism and NFC Relay Technique
Once installed, SuperCard X employs a previously undocumented NFC relay technique to facilitate fraudulent transactions. The malware operates through a two-component system:
1. Reader Component: Installed on the victim’s device, this component captures NFC data when the victim is persuaded to place their debit or credit card near their mobile device.
2. Tapper Component: Located on the attacker’s device, this component receives the relayed NFC data and emulates the victim’s card to perform unauthorized transactions at PoS terminals and ATMs.
Communication between the Reader and Tapper is facilitated via HTTP for command-and-control (C2) purposes. Attackers are required to create an account within the SuperCard X platform before distributing the malicious apps. During the TOAD phase, victims are instructed to enter login credentials provided during the phone call, establishing a link between the infected device and the attacker’s Tapper instance.
Implications and Security Concerns
The emergence of SuperCard X underscores the increasing sophistication of mobile malware and the potential vulnerabilities associated with NFC technology. By leveraging NFC relay attacks, cybercriminals can bypass traditional security measures, leading to significant financial losses for individuals and institutions.
This development is reminiscent of previous Android malware such as NGate, which utilized NFC capabilities to steal payment card data. NGate employed social engineering tactics to obtain card PINs and conducted unauthorized transactions by relaying NFC data from compromised devices to attacker-controlled smartphones. The continuous evolution of such malware highlights the need for enhanced security protocols and user awareness to mitigate the risks associated with NFC-based transactions.
Preventive Measures and Recommendations
To protect against threats like SuperCard X, users are advised to:
– Exercise Caution with Unsolicited Communications: Be wary of unexpected messages or calls requesting personal or financial information.
– Verify Application Authenticity: Only download applications from official app stores and verify the developer’s credentials.
– Implement Strong Security Practices: Regularly update device software, use reputable security applications, and monitor financial statements for unauthorized transactions.
– Educate on Social Engineering Tactics: Stay informed about common social engineering methods to recognize and avoid potential scams.
By adopting these measures, individuals can enhance their defense against sophisticated malware threats and contribute to a more secure digital environment.