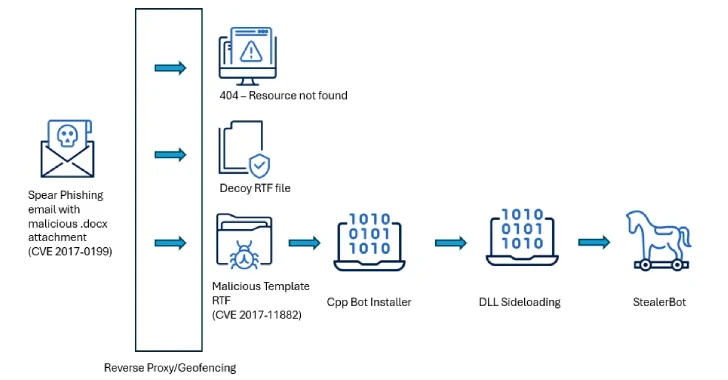
In a series of sophisticated cyber espionage operations, the advanced persistent threat (APT) group known as SideWinder has been targeting high-level government institutions across South Asia, including Sri Lanka, Bangladesh, and Pakistan. These attacks have been meticulously crafted to exploit outdated Microsoft Office vulnerabilities, specifically CVE-2017-0199 and CVE-2017-11882, to infiltrate and maintain persistent access within these governmental environments.
Targeted Institutions and Attack Vectors
The campaign has been particularly focused on several key governmental bodies:
– Bangladesh: The Telecommunication Regulatory Commission, Ministry of Defence, and Ministry of Finance.
– Pakistan: The Directorate of Indigenous Technical Development.
– Sri Lanka: The Department of External Resources, Department of Treasury Operations, Ministry of Defence, and the Central Bank.
The attackers initiate their campaigns with spear-phishing emails, a common tactic in cyber espionage. These emails are designed to appear legitimate and are tailored to the specific targets, increasing the likelihood of the recipient opening the malicious attachments. Once the attachment is opened, the embedded exploits for the aforementioned vulnerabilities are triggered, setting off a chain reaction that leads to the deployment of the StealerBot malware.
Exploitation of Legacy Vulnerabilities
The exploitation process begins when a victim opens a malicious document attached to the spear-phishing email. This action triggers the CVE-2017-0199 exploit, which allows the attacker to execute arbitrary code remotely. Subsequently, this leads to the deployment of additional payloads that install StealerBot through DLL side-loading techniques.
A notable aspect of SideWinder’s strategy is the use of geofencing. The malicious payloads are configured to activate only if the victim’s IP address matches the targeted region. If the IP address does not align with the specified criteria, the victim receives a benign RTF file, effectively minimizing the risk of detection and analysis by security researchers outside the targeted regions.
StealerBot Malware Capabilities
StealerBot is a .NET-based implant with a range of functionalities designed to facilitate comprehensive data exfiltration and system control:
– Data Collection: The malware is capable of capturing screenshots, logging keystrokes, and harvesting passwords and files from the compromised system.
– Reverse Shell Access: It establishes a reverse shell, allowing attackers to execute commands on the infected machine remotely.
– Additional Payload Deployment: StealerBot can download and execute additional malware, enabling the attackers to adapt their tools and tactics as needed.
These capabilities provide SideWinder with a robust platform for prolonged surveillance and data extraction from high-value targets.
Consistency and Precision in Operations
SideWinder’s operations are characterized by their consistency and precision. The group maintains a steady pace of activity without significant periods of inactivity, indicating a well-organized and persistent effort. Their tactics, techniques, and procedures (TTPs) reflect a high degree of control, ensuring that malicious payloads are delivered exclusively to carefully selected targets and often for limited durations.
Broader Context of Cyber Threats in South Asia
The activities of SideWinder are part of a broader landscape of cyber threats in the South Asian region. For instance, in April 2025, Pakistan successfully thwarted a series of cyber attacks allegedly launched by Indian hackers targeting various government ministries. These attempted breaches aimed to disrupt digital operations and steal sensitive data but were neutralized before any damage occurred. Federal IT Minister Shaza Fatima Khawaja confirmed that despite multiple hacking attempts, the attackers failed to breach any system or gain access to critical data related to federal ministries. She emphasized that Pakistan’s robust cybersecurity measures prevented any breakdown in services or leakage of information. The minister also highlighted that Pakistan has consistently ranked among the top countries in the world for cybersecurity over the past two years, attributing this to the highly capable professionals who work around the clock to defend the nation’s digital borders. ([samaa.tv](https://www.samaa.tv/2087332551-pakistan-foils-indian-hackers-cyber-attacks-on-ministries?utm_source=openai))
Similarly, in March 2025, the China-linked APT group Mustang Panda was observed weaponizing Visual Studio Code software as part of espionage operations targeting government entities in Southeast Asia. The group used Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks, demonstrating a relatively new technique in their cyber arsenal. This campaign is assessed to be a continuation of previously documented attack activities aimed at an unnamed Southeast Asian government entity in late September 2023. Mustang Panda has been operational since 2012, routinely conducting cyber espionage campaigns targeting government and religious entities across Europe and Asia, particularly those located in South China Sea countries. ([redpacketsecurity.com](https://www.redpacketsecurity.com/chinese-hackers-exploit-visual-studio-code-in-southeast-asian-cyberattacks/?utm_source=openai))
Implications and Recommendations
The persistent and evolving nature of these cyber threats underscores the critical need for governmental institutions to:
– Update and Patch Systems: Regularly update software and apply patches to address known vulnerabilities, particularly those that are actively exploited by threat actors.
– Enhance Email Security: Implement advanced email filtering and monitoring solutions to detect and block spear-phishing attempts.
– Conduct Regular Security Training: Educate employees on recognizing phishing attempts and other common attack vectors to reduce the risk of successful social engineering attacks.
– Implement Network Segmentation: Divide networks into segments to limit the spread of malware and unauthorized access within the organization.
– Monitor and Respond to Threats: Establish robust monitoring systems to detect unusual activities promptly and have an incident response plan in place to address potential breaches effectively.
By adopting these measures, organizations can bolster their defenses against sophisticated threat actors like SideWinder and mitigate the risks associated with cyber espionage campaigns.