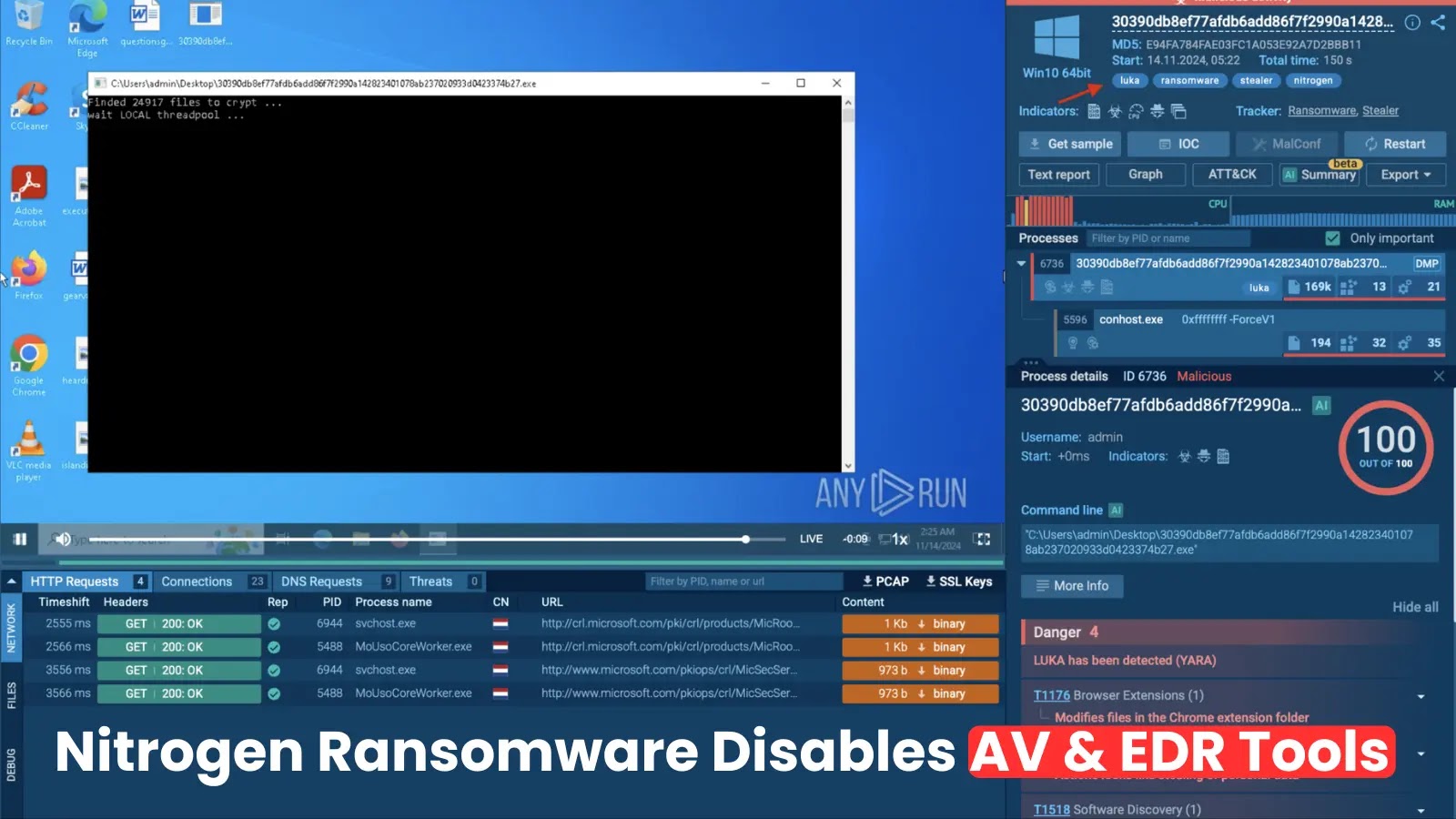
Nitrogen Ransomware has rapidly emerged as a formidable cyber threat, particularly targeting sectors such as construction, financial services, manufacturing, and technology across the United States, Canada, and the United Kingdom. This ransomware employs advanced techniques to infiltrate systems, disable security measures, and encrypt sensitive data, posing significant challenges to organizations worldwide.
Infection Vector and Initial Access
The initial infection vector for Nitrogen Ransomware involves malicious advertisements on popular search engines like Google and Bing. Unsuspecting users are redirected to fraudulent websites that mimic legitimate software download pages. These sites offer trojanized installers for widely used applications such as AnyDesk, WinSCP, and Cisco AnyConnect VPN. When users download and execute these compromised installers, the ransomware is silently deployed onto their systems. ([news.sophos.com](https://news.sophos.com/en-us/2023/07/26/into-the-tank-with-nitrogen/?utm_source=openai))
Deployment and Persistence Mechanisms
Once executed, Nitrogen Ransomware employs several sophisticated techniques to establish a foothold within the infected system:
1. DLL Sideloading: The ransomware utilizes dynamic link library (DLL) sideloading to execute malicious code under the guise of legitimate processes. For instance, it may rename the Windows tool `msiexec.exe` to `install.exe` or `setup.exe`, which then sideloads a malicious `msi.dll` (NitrogenInstaller) stored within the same directory. ([news.sophos.com](https://news.sophos.com/en-us/2023/07/26/into-the-tank-with-nitrogen/?utm_source=openai))
2. Privilege Escalation: Nitrogen attempts to elevate its privileges by executing a User Access Control (UAC) bypass using the CMSTPLUA CLSID method. This technique has been observed in other ransomware families, including LockBit and BlackMatter. ([news.sophos.com](https://news.sophos.com/en-us/2023/07/26/into-the-tank-with-nitrogen/?utm_source=openai))
3. Persistence: The ransomware creates registry run keys to ensure its persistence across system reboots. For example, it may add a key named Python under `HKEY_USERS\
Execution of the Ransomware Payload
After establishing persistence, Nitrogen executes its ransomware payload, which involves:
– File Encryption: The malware employs strong encryption algorithms to lock files, appending a .NBA extension to the encrypted files.
– Ransom Note Deployment: A ransom note named readme.txt is dropped in multiple directories, warning victims about data encryption and theft. The note emphasizes double extortion, threatening to publish stolen data on a dark web blog if the ransom remains unpaid. ([hoploninfosec.com](https://hoploninfosec.com/nitrogen-ransomware/?utm_source=openai))
Advanced Evasion Techniques
Nitrogen Ransomware incorporates cutting-edge evasion mechanisms to avoid detection and analysis:
1. Debugger and Virtual Machine Detection: The ransomware identifies and avoids running in controlled environments, making it harder for cybersecurity researchers to analyze its behavior.
2. Code Obfuscation: Techniques like stack strings hinder reverse engineering, complicating efforts to understand the malware’s code.
3. System Discovery: Nitrogen enumerates system information and examines Portable Executable (PE) sections to pinpoint high-value targets within the network. ([hoploninfosec.com](https://hoploninfosec.com/nitrogen-ransomware/?utm_source=openai))
Exploitation of Vulnerable Drivers
A notable aspect of Nitrogen Ransomware’s strategy is its exploitation of legitimate but vulnerable drivers to disable security software:
– Bring Your Own Vulnerable Driver (BYOVD) Attack: Nitrogen exploits the legitimate driver truesight.sys from RogueKiller AntiRootkit to terminate security processes and bypass endpoint detection and response (EDR) systems. This technique allows the ransomware to operate with elevated privileges, effectively neutralizing security defenses.
Impact on Key Industries
Nitrogen’s focus on critical industries amplifies its potential for widespread disruption:
1. Manufacturing: As one of the most impacted industries globally, manufacturing faces severe repercussions due to downtime and halted production lines.
2. Financial Services: These organizations are attractive targets due to the sensitive nature of their data and the high operational disruptions.
3. Technology Firms: Nitrogen targets technology companies to exploit their reliance on digital infrastructure, aiming to extract maximum ransom. ([hoploninfosec.com](https://hoploninfosec.com/nitrogen-ransomware/?utm_source=openai))
Double Extortion and Psychological Pressure
Nitrogen’s ransom note employs fear tactics to coerce victims into compliance:
– Threats of Data Publication: The note warns against involving third parties or law enforcement, claiming such actions could result in irreversible data loss or legal penalties under regulations like GDPR.
– False Assurances: The attackers offer decryption tools, proof of data deletion, and even security recommendations upon payment, creating a false sense of assurance to prompt quick payments. ([hoploninfosec.com](https://hoploninfosec.com/nitrogen-ransomware/?utm_source=openai))
Defense Strategies Against Nitrogen Ransomware
Organizations can proactively protect themselves against Nitrogen and similar ransomware threats by implementing the following measures:
1. Regular Software Updates and Patch Management: Ensure all software and systems are updated promptly to close vulnerabilities that ransomware exploits.
2. Implement Multi-Factor Authentication (MFA): Adding an extra layer of security for critical systems can significantly reduce unauthorized access.
3. Employee Training: Regular training programs should be conducted to help employees recognize phishing attempts and other malicious tactics to gain initial access.
4. Endpoint Detection and Response (EDR) Solutions: Deploying EDR tools can help identify and mitigate malicious activities early, minimizing potential damage.
5. Regular Data Backups: Maintain secure and offline backups of critical data to ensure recovery in case of an attack. ([hoploninfosec.com](https://hoploninfosec.com/nitrogen-ransomware/?utm_source=openai))
The Importance of Operational Resilience
As ransomware groups like Nitrogen continue to evolve, organizations must adopt robust cybersecurity frameworks to stay ahead of threats. This includes technical defenses and a comprehensive incident response plan to ensure business continuity. By investing in cybersecurity awareness, advanced detection tools, and regular assessments of their digital infrastructure, enterprises can mitigate risks and build resilience against future attacks.