In March 2025, cybersecurity researchers identified a series of sophisticated cyber espionage activities targeting government agencies and public institutions in Japan and Taiwan. These operations have been attributed to MirrorFace, a nation-state threat actor with alleged ties to China’s intelligence apparatus. The group’s latest campaign involves deploying advanced malware strains, notably ROAMINGMOUSE and an enhanced version of the ANEL backdoor, to infiltrate and extract sensitive information from targeted entities.
Background on MirrorFace
MirrorFace, also known as Earth Kasha, is believed to be a sub-cluster within the Advanced Persistent Threat group APT10. APT10 has a documented history of conducting cyber espionage operations aligned with Chinese strategic interests. Over the past five years, MirrorFace has been implicated in over 200 cyberattacks aimed at compromising Japan’s national security and technological sectors. These attacks have targeted a wide array of entities, including the Foreign and Defense Ministries, the Japan Aerospace Exploration Agency (JAXA), and various private companies and think tanks. ([apnews.com](https://apnews.com/article/68adcb293b2931da4c30ca0279720124?utm_source=openai))
Recent Campaign Tactics
The latest campaign orchestrated by MirrorFace employs a multifaceted approach to compromise target systems:
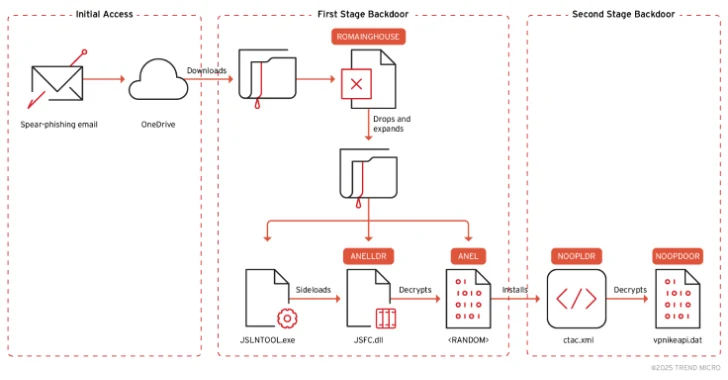
1. Spear-Phishing Emails: The attack initiates with carefully crafted spear-phishing emails sent to specific individuals within targeted organizations. These emails often originate from legitimate but compromised accounts, enhancing their credibility. They contain embedded Microsoft OneDrive URLs that, when accessed, download a ZIP archive.
2. Malware Deployment via ROAMINGMOUSE: The downloaded ZIP file includes a malicious Excel document embedded with macros. Upon execution, these macros activate ROAMINGMOUSE, a macro-enabled dropper first observed in MirrorFace operations in 2024. ROAMINGMOUSE decodes and extracts additional components necessary for the next stage of the attack.
3. DLL Sideloading to Activate ANEL Backdoor: The extracted components include a legitimate executable (e.g., JSLNTOOL.exe) and a malicious DLL (ANELLDR). By exploiting DLL sideloading techniques, the legitimate executable loads the malicious DLL, which then decrypts and executes the ANEL backdoor. This backdoor provides the attackers with persistent access to the compromised system.
Enhancements in ANEL Backdoor
The 2025 iteration of the ANEL backdoor exhibits significant advancements:
– In-Memory Execution of Beacon Object Files (BOFs): The updated ANEL includes a new command that facilitates the in-memory execution of BOFs. BOFs are compiled C programs that extend the capabilities of Cobalt Strike, a penetration testing tool often repurposed by threat actors for malicious activities. This feature allows for more flexible and stealthy post-exploitation operations.
– Integration with NOOPDOOR via SharpHide: In certain instances, MirrorFace has utilized SharpHide, an open-source tool, to deploy NOOPDOOR (also known as HiddenFace). NOOPDOOR is another backdoor that supports DNS-over-HTTPS (DoH), enabling the concealment of command-and-control (C2) communications by encrypting DNS queries. This technique enhances the stealth and resilience of the malware’s communication channels.
Implications and Recommendations
The persistent and evolving nature of MirrorFace’s cyber espionage activities underscores the critical need for robust cybersecurity measures among government agencies and public institutions, particularly those in Japan and Taiwan. The use of advanced malware and sophisticated delivery mechanisms highlights the group’s capability and intent to infiltrate high-value targets.
To mitigate the risks posed by such threats, organizations are advised to:
– Enhance Email Security Protocols: Implement advanced email filtering solutions to detect and block spear-phishing attempts.
– Conduct Regular Security Training: Educate employees on recognizing phishing emails and the importance of not engaging with suspicious links or attachments.
– Implement Multi-Layered Defense Strategies: Utilize a combination of endpoint detection and response (EDR) tools, network monitoring, and intrusion detection systems to identify and respond to malicious activities promptly.
– Regularly Update and Patch Systems: Ensure that all software and systems are up-to-date with the latest security patches to prevent exploitation of known vulnerabilities.
By adopting these proactive measures, organizations can strengthen their defenses against sophisticated threat actors like MirrorFace and safeguard sensitive information from unauthorized access and exfiltration.