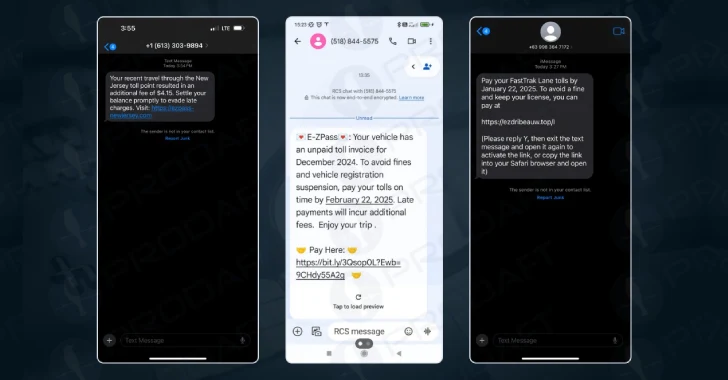
A sophisticated phishing-as-a-service (PhaaS) platform named Lucid has emerged, targeting 169 organizations across 88 countries through smishing attacks delivered via Apple iMessage and Rich Communication Services (RCS) on Android devices. This approach allows cybercriminals to bypass traditional SMS-based detection systems, enhancing the effectiveness of their phishing campaigns.
Lucid operates on a scalable, subscription-based model, enabling threat actors to conduct extensive phishing operations aimed at harvesting credit card information and personally identifiable information (PII) for financial fraud. According to a technical report by Swiss cybersecurity firm PRODAFT, Lucid’s utilization of legitimate communication platforms like iMessage and RCS significantly increases the delivery and success rates of these malicious campaigns.
Origins and Operators
The Lucid platform is attributed to a Chinese-speaking hacking group known as the XinXin group, also referred to as Black Technology. This group has previously developed other PhaaS platforms, including Lighthouse and Darcula. Notably, Darcula has been updated with capabilities to clone any brand’s website, creating convincing phishing versions. The developer behind Lucid, identified as LARVA-242, is a key figure within the XinXin group.
These PhaaS platforms share similarities in templates, target pools, and tactics, indicating a thriving underground economy where Chinese-speaking actors leverage platforms like Telegram to advertise their services on a subscription basis for profit-driven motives.
Targeted Regions and Methods
The phishing campaigns facilitated by Lucid primarily focus on Europe, the United Kingdom, and the United States. They impersonate entities such as postal services, courier companies, toll payment systems, and tax refund agencies, employing convincing phishing templates to deceive victims into providing sensitive information.
To execute these large-scale operations, the threat actors utilize iPhone device farms and mobile device emulators running on Windows systems. This setup allows them to send hundreds of thousands of scam messages containing malicious links in a coordinated manner. The phone numbers targeted are obtained through various means, including data breaches and cybercrime forums.
Evasion Techniques
Lucid employs several sophisticated techniques to evade detection:
– iMessage Exploitation: To circumvent iMessage’s link-clicking restrictions, attackers use tactics like prompting recipients to reply with Y to establish two-way communication.
– RCS Exploitation: For Google’s RCS, they continuously rotate sending domains and numbers to avoid pattern recognition and filtering mechanisms.
Additionally, for iMessage, attackers create temporary Apple IDs with impersonated display names. In the case of RCS, they exploit inconsistencies in carrier implementations of sender verification.
Advanced Features
Lucid offers automation tools that simplify the creation of customizable phishing websites. These sites incorporate advanced anti-detection and evasion techniques, such as IP blocking, user-agent filtering, and time-limited single-use URLs. The platform also allows real-time monitoring of victim activity, recording every interaction with the phishing links via a control panel built using the open-source Webman PHP framework.
Credit card details submitted by victims undergo additional verification steps to ensure their validity before being exploited for fraudulent activities.
Implications and Recommendations
The emergence of Lucid underscores the increasing sophistication and accessibility of phishing campaigns facilitated by PhaaS platforms. These services enable widespread credential theft and subsequent attacks, such as business email compromise.
Organizations are encouraged to:
– Enhance Email Filtering and Detection Systems: Implement advanced filtering mechanisms to identify and block phishing attempts.
– Educate Employees: Conduct regular training sessions to raise awareness about phishing tactics and social engineering techniques.
– Utilize Behavioral Analytics: Monitor for unusual account activity that may indicate a security breach.
By adopting these measures, organizations can better protect themselves against the evolving threat landscape posed by platforms like Lucid.