The North Korean state-sponsored cyber threat actor, Lazarus Group, has intensified its malicious activities by targeting job seekers in the cryptocurrency sector. Utilizing a sophisticated social engineering technique known as ClickFix, the group deploys a previously undocumented Go-based backdoor named GolangGhost on both Windows and macOS systems.
Campaign Overview
This latest operation, dubbed ClickFake Interview by French cybersecurity firm Sekoia, is an extension of the earlier Contagious Interview campaign, also referred to as DeceptiveDevelopment, DEV#POPPER, and Famous Chollima. Active since at least December 2022, Contagious Interview was publicly documented in late 2023. The campaign primarily targets centralized finance entities by impersonating reputable companies such as Coinbase, KuCoin, Kraken, Circle, Securitize, BlockFi, Tether, Robinhood, and Bybit. This marks a strategic shift from Lazarus Group’s previous focus on decentralized finance (DeFi) platforms.
Attack Methodology
The attack begins with Lazarus Group operatives reaching out to potential victims via professional networking platforms like LinkedIn or X (formerly Twitter). Posing as recruiters from well-known cryptocurrency firms, they offer enticing job opportunities to lure individuals into their trap.
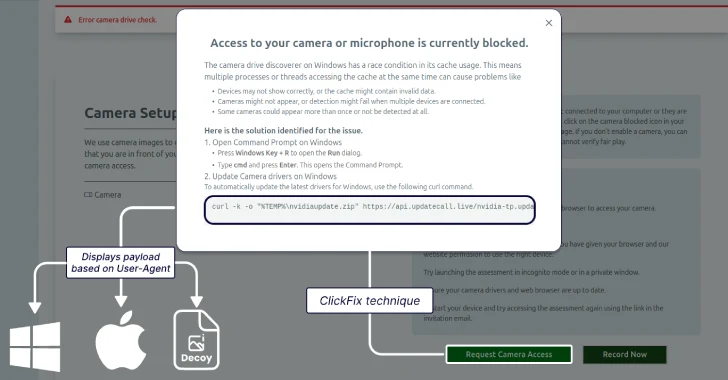
Once the target expresses interest, the attackers propose a video interview. They direct the candidate to a seemingly legitimate video interviewing service named Willo, instructing them to complete a video assessment. The entire setup is meticulously designed to build trust and appears professional until the user is prompted to enable their camera.
At this juncture, an error message appears, indicating that the user needs to download a driver to fix the issue. This is where the ClickFix technique is employed. The victim is provided with specific instructions to resolve the purported issue, which vary depending on the operating system:
– Windows Users: The target is prompted to open the Command Prompt and execute a `curl` command. This command downloads and runs a Visual Basic Script (VBS) file, which subsequently launches a batch script to execute the GolangGhost malware.
– macOS Users: The victim is instructed to open the Terminal application and run a `curl` command. This command fetches a shell script that, in turn, executes another shell script. The second script runs a stealer module named FROSTYFERRET (also known as ChromeUpdateAlert) alongside the GolangGhost backdoor.
Malware Functionality
The FROSTYFERRET module is designed to deceive the user by displaying a fake window stating that the Chrome web browser requires access to the user’s camera or microphone. It then prompts the user to enter their system password. Regardless of the validity of the entered password, the information is exfiltrated to a Dropbox location controlled by the attackers. This suggests an attempt to access the iCloud Keychain using the stolen credentials.
GolangGhost, the primary payload, is a Go-based backdoor that provides the attackers with persistent access to the compromised system. Its capabilities include:
– Command Execution: Running arbitrary commands on the infected machine.
– File Manipulation: Uploading and downloading files between the victim’s system and the attacker’s server.
– System Information Gathering: Collecting detailed information about the victim’s system, including operating system details, hardware specifications, and network configurations.
– Persistence Mechanisms: Ensuring the malware remains active across system reboots and user sessions.
Implications and Recommendations
The Lazarus Group’s use of the ClickFix tactic in conjunction with the deployment of GolangGhost underscores the evolving sophistication of state-sponsored cyber threats. By exploiting the trust associated with professional networking platforms and legitimate-looking services, they effectively deceive individuals into compromising their systems.
To mitigate the risk of such attacks, individuals and organizations should adopt the following measures:
1. Verify Recruiter Identities: Always confirm the authenticity of recruiters and the legitimacy of job offers, especially those received through unsolicited messages on social media platforms.
2. Exercise Caution with Unfamiliar Platforms: Be wary of instructions to download software or drivers from unfamiliar sources, particularly during the job application process.
3. Implement Security Best Practices: Keep operating systems and software up to date, use reputable antivirus solutions, and regularly back up important data.
4. Educate and Train Staff: Provide regular training on recognizing phishing attempts and social engineering tactics to enhance organizational resilience against such threats.
By remaining vigilant and adopting proactive security measures, individuals and organizations can better protect themselves against the sophisticated tactics employed by threat actors like the Lazarus Group.