Delegated Managed Service Accounts (dMSAs), introduced in Windows Server 2025, represent Microsoft’s latest advancement in secure service account management. Designed to enhance security by mitigating traditional credential theft attacks such as Kerberoasting, dMSAs offer automatic credential management and tie authentication directly to machine identities. This innovation aims to eliminate the risks associated with manual password management in traditional service accounts.
According to Microsoft’s documentation, dMSAs provide a more secure and manageable approach to service account management compared to traditional service accounts. Administrators can transition from conventional service accounts by disabling the original account’s password authentication and redirecting all requests through the Local Security Authority (LSA) using the new dMSA mechanism.
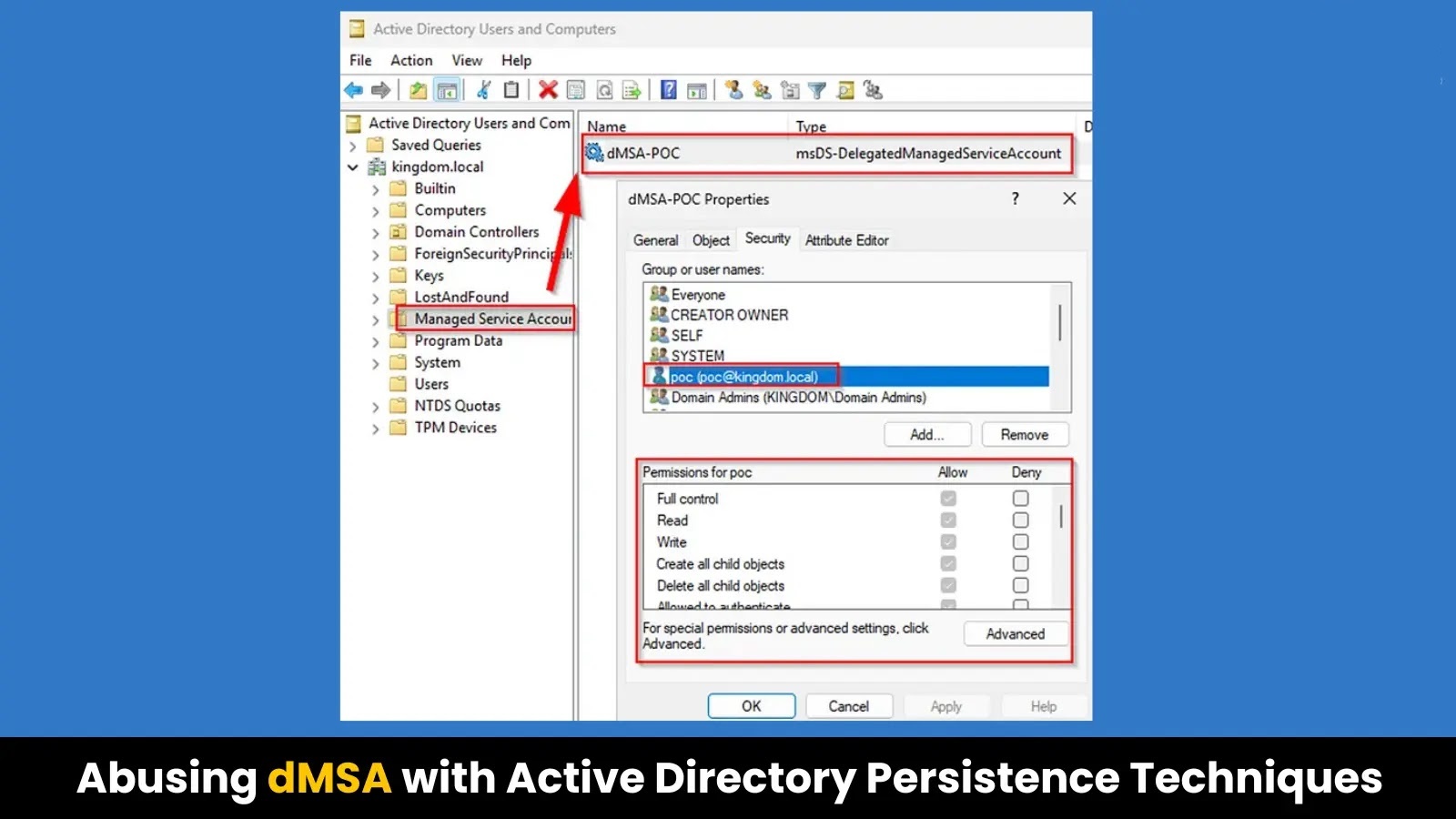
Potential Abuse of dMSAs
Despite the enhanced security controls, security researchers have identified potential abuse vectors that could allow attackers to establish persistent access within Active Directory environments. The primary concern lies in the Access Control Lists (ACLs) of the dMSA objects themselves.
The Managed Service Accounts container and its permission inheritance structure present a vulnerability. An attacker with temporary domain administrator access can modify ACLs to maintain control over dMSA accounts even after their elevated privileges are revoked.
Exploitation Process
The exploitation process involves the following steps:
1. Acquiring GenericAll Permissions: The attacker gains GenericAll permissions on the Managed Service Accounts container.
2. Forcing Inheritance: Although GenericAll permissions on the container do not automatically grant access to child objects, the attacker can force inheritance down to all dMSA objects.
3. Establishing Persistent Control: By executing specific commands, the attacker can:
– Change ownership of dMSA objects.
– Create new dMSA accounts under their control.
– Modify the `PrincipalsAllowedToRetrieveManagedPassword` property to include their compromised accounts.
Mitigation Strategies
To protect against such exploitation, organizations deploying Windows Server 2025 should implement the following measures:
– Monitor ACL Modifications: Closely monitor changes to the Managed Service Accounts container ACLs to detect unauthorized modifications.
– Configure Group Policy Settings: Enable the Group Policy setting: Computer Configuration\Administrative Templates\System\Kerberos\Enable Delegated Managed Service Account logons only on authorized systems.
– Event Monitoring: Monitor for Event ID 4662, which indicates Write access to dMSA objects, to identify potential unauthorized changes.
– Implement Least Privilege Access: Apply the principle of least privilege to Active Directory administrative groups to minimize the risk of unauthorized access.
– Regular ACL Audits: Regularly audit ACL changes on critical containers using tools like PingCastle or BloodHound to identify and remediate potential vulnerabilities.
While dMSAs significantly improve service account security over traditional accounts, organizations must remain vigilant about potential abuse vectors. The security improvements offered by dMSAs outweigh the risks, particularly when proper monitoring and access controls are implemented. As Microsoft continues to develop Windows Server 2025, additional security controls around dMSA management are expected to emerge to address these newly discovered persistence techniques.