Instant messaging (IM) applications such as WeChat, WhatsApp, Telegram, and QQ have become integral to daily communication, connecting billions globally. However, their widespread adoption has also made them attractive targets for cyberattacks, posing significant risks to personal privacy, financial assets, and even national security. Recent research has unveiled critical vulnerabilities within these platforms, emphasizing the delicate balance between functionality and security.
WeChat’s Client-Side Vulnerabilities
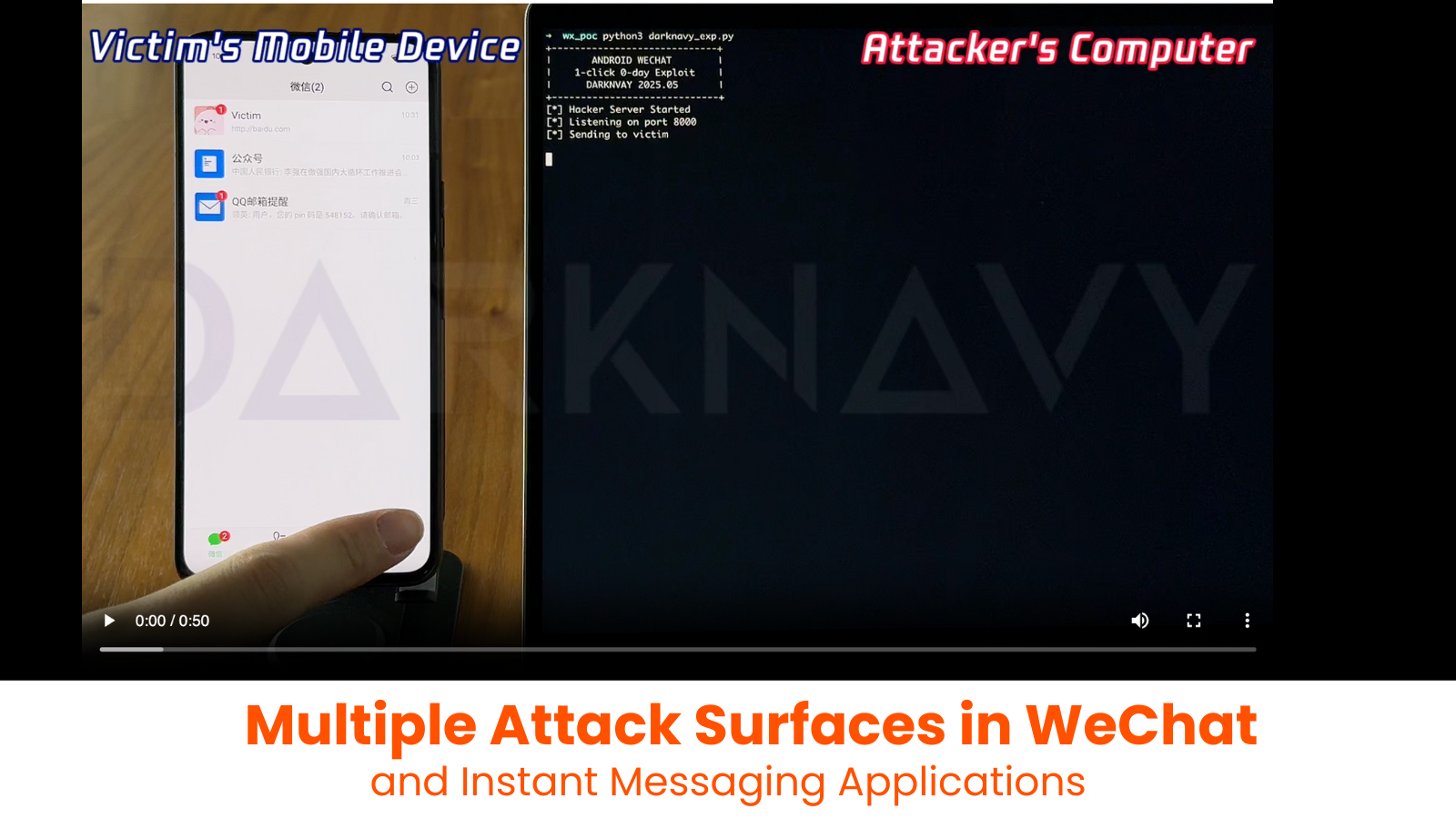
A recent study by cybersecurity firm DARKNAVY has brought to light a significant client-side vulnerability in WeChat. This flaw exploits the application’s built-in browser components and URL parsing mechanisms, enabling remote code execution without any user interaction beyond receiving a malicious message. This discovery marks a substantial escalation in security threats, particularly given WeChat’s extensive user base.
Understanding the Attack Surface
IM clients are susceptible to various security risks, primarily at the client level. Key vulnerabilities include:
– URL Parsing and Custom Protocols: Attackers can exploit custom protocols (e.g., `weixin://` in WeChat) to trigger unauthorized actions.
– File Processing: Malicious files can be crafted to exploit weaknesses in how IM apps handle different file types.
– Embedded Browsers: In-app browsers may contain outdated components susceptible to known exploits.
– Mini-Program Ecosystems: Third-party mini-programs can introduce additional vulnerabilities if not properly vetted.
Historical Context of IM Vulnerabilities
The landscape of IM security has been marred by several notable incidents:
– iMessage Memory Corruption (2019): A flaw (CVE-2019-8641) allowed remote code execution via malicious files without user interaction.
– WhatsApp GIF Vulnerability (2019): A crafted GIF could trigger a double-free vulnerability (CVE-2019-11932), enabling device hijacking.
– XcodeGhost Malware (2015): Malicious code was injected into apps like WeChat through a compromised version of Apple’s Xcode, leading to data theft.
WeChat’s Security Mechanisms
WeChat has implemented several security measures to mitigate potential threats:
– URL Validation and Debugging Controls: WeChat’s debugging mechanism, accessible via URLs like `debugxweb.qq.com`, poses risks if exploited. Attackers could manipulate parameters to force version rollbacks or configuration changes. However, WeChat enforces strict safeguards: sensitive operations like `install_embed_plugin` require enabling `bEnableLocalDebug`, and `set_config_url` mandates HTTPS with whitelisted domains (`dldir1.qq.com`). This prevents tampering while maintaining functionality for legitimate use cases.
– XWEB Browser Engine: WeChat’s Android client uses the XWEB engine, a Chromium-based browser lagging behind official releases (v130 vs. Chrome’s v136). Despite this, XWEB employs sandboxing, isolating rendering processes (`xweb_sandboxed_process_0`) from privileged ones to mitigate exploits. JSBridge interfaces, which enable web-to-native functions like `scanQRCode`, are tightly controlled via cloud-based permission arrays, limiting access for untrusted sites.
– Mini-Program Security: WeChat’s mini-programs, used by over 1.2 billion users, operate in a dual-thread architecture. JavaScript logic and rendering layers are isolated, preventing cross-layer privilege escalation. For example, rendering-layer APIs like `insertVideoPlayer` cannot access high-risk functions such as `saveFile`, reducing the impact of cross-site scripting (XSS) vulnerabilities.
Ongoing Challenges and Recommendations
Despite these defenses, IM platforms remain vulnerable. In 2025, a Windows WhatsApp flaw (CVE-2025-30401) allowed attackers to disguise executables as images, tricking users into executing malware. Similarly, libwebp vulnerabilities (CVE-2023-4863) affected WeChat’s image rendering, enabling heap overflows. These incidents highlight the need for continuous updates and robust input validation.
To enhance security, IM developers should:
– Regularly Update Components: Ensure all embedded browsers and libraries are up-to-date to mitigate known vulnerabilities.
– Implement Strict Input Validation: Sanitize all user inputs to prevent injection attacks.
– Enhance User Awareness: Educate users on recognizing phishing attempts and the importance of not interacting with suspicious messages.
– Strengthen Mini-Program Vetting: Implement rigorous security assessments for third-party mini-programs before integration.
As IM applications continue to evolve, integrating more features and expanding their attack surfaces, a proactive and comprehensive approach to security is imperative to protect users and maintain trust in these essential communication tools.