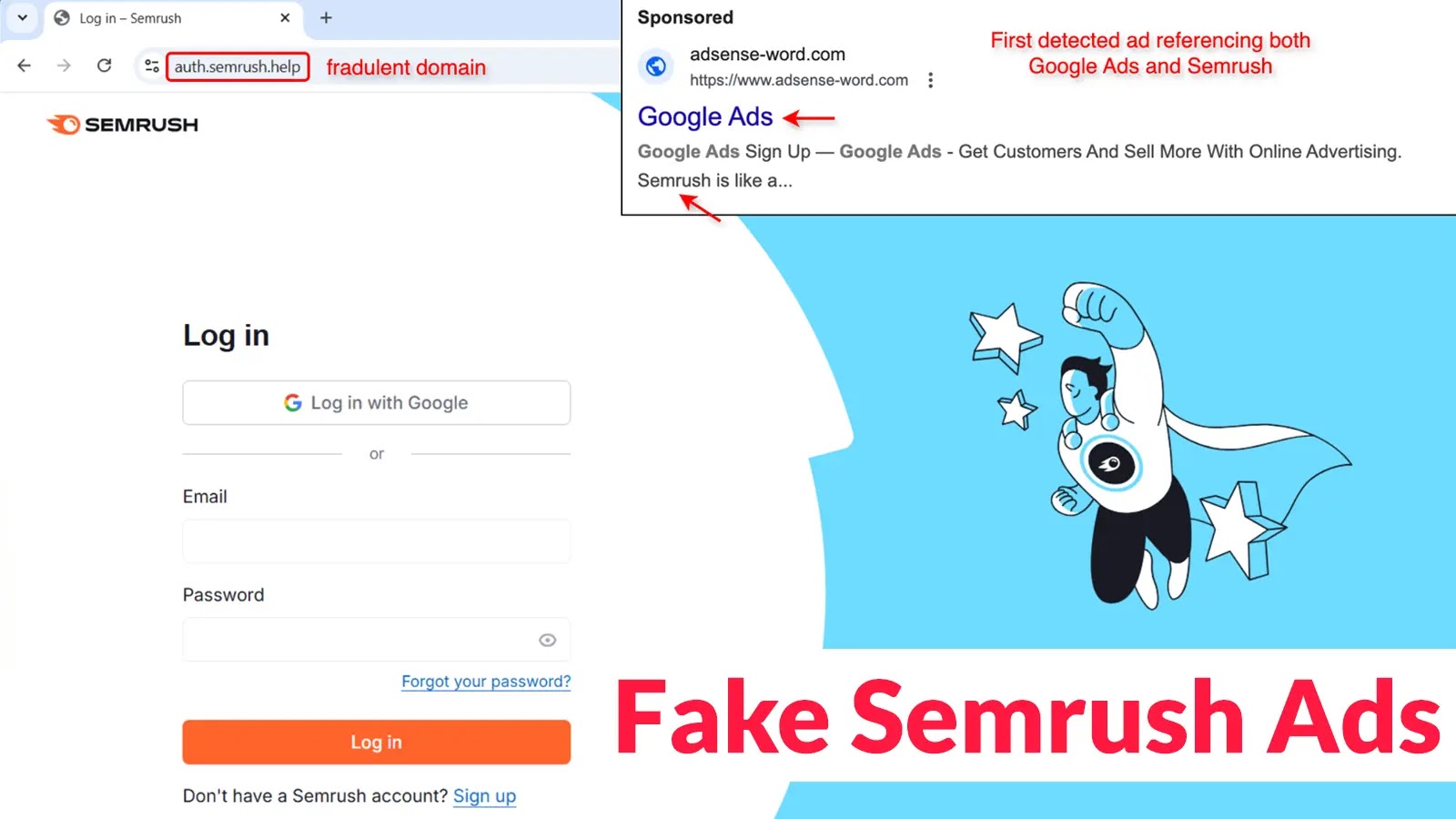
In a recent and sophisticated phishing campaign, cybercriminals have been targeting SEO professionals by deploying counterfeit Semrush advertisements on Google. These deceptive ads are designed to steal Google account credentials, posing a significant threat to digital marketers and businesses reliant on online visibility tools.
The Deceptive Strategy
The attackers have strategically placed malicious ads that mimic legitimate Semrush promotions within Google search results. When users click on these ads, they are redirected to meticulously crafted phishing sites that closely resemble Semrush’s official login page. Notably, these counterfeit pages often display domain names similar to Semrush’s, such as “semrush[.]click” or “semrush[.]tech,” but with different top-level domains, making them appear authentic at first glance. ([bleepingcomputer.com](https://www.bleepingcomputer.com/news/security/fake-semrush-ads-used-to-steal-seo-professionals-google-accounts/?utm_source=openai))
The Phishing Mechanism
Upon reaching the fraudulent login page, users are prompted to sign in using their Google credentials. The phishing site predominantly offers the “Log in with Google” option, effectively coercing users into providing their Google account information. Once entered, these credentials are captured and transmitted directly to the attackers. This method not only grants unauthorized access to the victims’ Google accounts but also to any integrated services, such as Google Analytics and Google Search Console, which are commonly linked with Semrush accounts. ([bleepingcomputer.com](https://www.bleepingcomputer.com/news/security/fake-semrush-ads-used-to-steal-seo-professionals-google-accounts/?utm_source=openai))
Potential Consequences
The implications of this phishing campaign are far-reaching. By gaining access to Google accounts, cybercriminals can retrieve sensitive business data, including website performance metrics, user behavior analytics, and strategic marketing information. This data is invaluable for competitors and malicious entities aiming to undermine a business’s online presence or exploit its customer base. Furthermore, with control over Google Ads accounts, attackers can initiate additional malvertising campaigns, perpetuating a cycle of fraud and data breaches. ([malware.news](https://malware.news/t/semrush-impersonation-scam-hits-google-ads/92338?utm_source=openai))
The Evolution of the Attack
This campaign signifies an evolution in phishing tactics. Previously, similar attacks directly targeted Google Ads accounts through malicious ads hosted on Google Sites. The current strategy, however, adopts a more indirect approach by impersonating Semrush, a widely used SEO tool. This shift indicates that cybercriminals are continuously refining their methods to exploit trusted platforms and services, thereby increasing the likelihood of deceiving their targets. ([malware.news](https://malware.news/t/semrush-impersonation-scam-hits-google-ads/92338?utm_source=openai))
Protective Measures
To safeguard against such sophisticated phishing attempts, individuals and organizations should adopt the following practices:
1. Verify URLs Carefully: Before entering login credentials, ensure that the website’s URL matches the official domain of the service. Be cautious of slight misspellings or unusual domain extensions.
2. Avoid Clicking on Sponsored Ads for Login: Access services directly by typing the URL into the browser or using bookmarks, rather than clicking on sponsored search results, which can be manipulated.
3. Enable Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security, making it more challenging for attackers to gain unauthorized access even if they obtain login credentials.
4. Educate and Train Staff: Regularly conduct cybersecurity awareness training to help employees recognize phishing attempts and understand the importance of secure online practices.
5. Use Password Managers: Password managers can autofill credentials only on recognized and verified domains, reducing the risk of entering information on fraudulent sites.
Industry Response
Security researchers have reported these malicious ads to Google, leading to their prompt removal. However, the persistence of such campaigns underscores the need for continuous vigilance and proactive security measures within the digital marketing community. As cyber threats evolve, staying informed and adopting robust security protocols are essential to protect sensitive information and maintain trust in online platforms. ([bleepingcomputer.com](https://www.bleepingcomputer.com/news/security/fake-semrush-ads-used-to-steal-seo-professionals-google-accounts/?utm_source=openai))
Conclusion
The exploitation of fake Semrush ads to steal Google account credentials highlights the increasing sophistication of phishing campaigns targeting SEO professionals. By understanding the tactics employed by cybercriminals and implementing comprehensive security measures, individuals and organizations can better defend against these deceptive attacks and safeguard their valuable digital assets.