In a sophisticated cyberattack campaign identified in early 2025, malicious actors have been leveraging counterfeit Facebook pages and sponsored advertisements to lure users into downloading malware under the guise of the legitimate Kling AI platform. Kling AI, developed by Beijing-based Kuaishou Technology, is renowned for its AI-driven capabilities to generate images and videos from textual and visual prompts. Since its launch in June 2024, the platform has amassed a user base exceeding 22 million as of April 2025.
The Deceptive Strategy
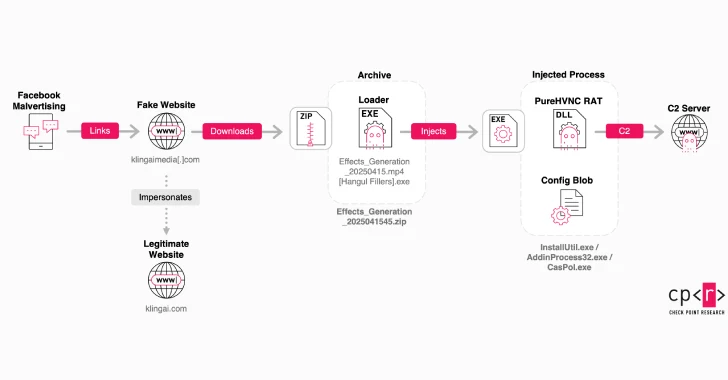
The attackers created fraudulent Facebook pages and ads that closely mimicked Kling AI’s official branding. These deceptive ads directed unsuspecting users to spoofed websites, such as klingaimedia[.]com or klingaistudio[.]com, which were designed to replicate the authentic Kling AI interface. Visitors to these sites were prompted to create AI-generated content directly within their browsers.
However, instead of delivering the promised multimedia content, the sites offered downloads labeled as images or videos. These downloads were, in reality, malicious Windows executables concealed using double extensions and Hangul Filler characters (0xE3 0x85 0xA4), a technique that effectively disguises the true nature of the files.
Malware Deployment and Functionality
Upon downloading and executing these disguised files, users inadvertently initiated a multi-stage malware deployment process:
1. Initial Loader Execution: The downloaded file acted as a loader, which, when executed, established persistence on the victim’s system by modifying Windows Registry settings. It also monitored for the presence of analysis tools such as Wireshark, OllyDbg, Procmon, ProcExp, PeStudio, and Fiddler to evade detection.
2. Second-Stage Payload Deployment: The loader then injected a second-stage payload into legitimate system processes like CasPol.exe or InstallUtil.exe. This payload, obfuscated using .NET Reactor, was identified as the PureHVNC Remote Access Trojan (RAT).
3. Data Exfiltration: Once active, PureHVNC established communication with a command-and-control (C2) server located at 185.149.232[.]197. The RAT was equipped with capabilities to steal sensitive information, including credentials stored in browsers and data from cryptocurrency wallet extensions installed on Chromium-based browsers. Additionally, it employed a plugin-based approach to capture screenshots when window titles matching those of banks and cryptocurrency wallets were opened.
Scope and Attribution
Check Point Research identified at least 70 promoted posts from fake social media pages impersonating Kling AI. While the exact perpetrators remain unidentified, evidence from the fake websites and some advertisements suggests a possible origin in Vietnam. This aligns with a broader trend of Vietnamese threat actors exploiting the popularity of generative AI tools to disseminate malware. For instance, earlier this month, cybersecurity firm Morphisec reported that a Vietnamese threat actor had been using fake AI-powered tools to distribute an information stealer malware dubbed Noodlophile.
Implications and Recommendations
This campaign underscores the evolving tactics of cybercriminals who combine social engineering with advanced malware to compromise users’ systems and exfiltrate personal data. The use of social media platforms like Facebook for malvertising—advertising that delivers malware—has become increasingly prevalent.
To mitigate such threats, users are advised to:
– Exercise Caution with Online Ads: Be skeptical of ads promoting software downloads, especially those offering free or highly discounted AI tools.
– Verify Authenticity: Always access services through official websites and verify the legitimacy of the source before downloading any software.
– Maintain Updated Security Software: Ensure that antivirus and anti-malware programs are up to date to detect and prevent the execution of malicious files.
– Educate and Train: Organizations should provide regular training to employees about the risks of phishing and malvertising campaigns, emphasizing the importance of vigilance when interacting with online content.
By adopting these practices, individuals and organizations can better protect themselves against the sophisticated and evolving landscape of cyber threats.