In a sophisticated cyberattack campaign identified by Netskope Threat Labs in February 2025, threat actors have been leveraging deceptive CAPTCHAs and Cloudflare’s Turnstile verification system to disseminate LegionLoader malware. This campaign primarily targets individuals searching for PDF documents online, leading them through a complex infection chain that culminates in the installation of a malicious browser extension designed to steal sensitive user data.
The Infection Chain:
1. Initial Lure: Victims are enticed by search engine results to open a PDF document. Upon accessing the document, they encounter a fake CAPTCHA prompt, which appears to be a standard verification step.
2. Redirection and Deception: Clicking the fake CAPTCHA initiates a series of redirections involving Cloudflare Turnstile CAPTCHAs and browser notification requests. If the user consents to receive notifications, they are further directed to download what seems to be the desired document.
3. Malicious Download: Instead of the intended document, the user unknowingly downloads an MSI installer file.
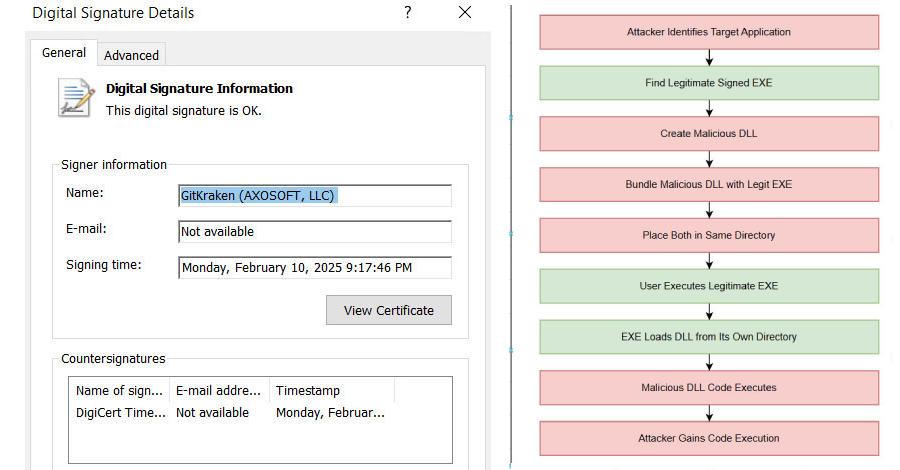
4. Execution and Concealment: Executing the MSI file registers an application named Kilo Verfair Tools, which includes several custom actions. One such action launches SumatraPDF, a legitimate document viewer, to maintain the illusion of document viewing.
5. Malware Deployment: Simultaneously, a batch script named logd.bat is executed, extracting DLLs from an archive and running a file signed with a VMware certificate, thereby initiating the malware infection.
Technical Breakdown:
– Malicious DLL Execution: The DLL, masquerading as a legitimate OpenSSL library, decodes and executes the LegionLoader payload. This payload employs a custom algorithm to deobfuscate shellcode, utilizing techniques like API Hammering to evade detection.
– Process Hollowing: The shellcode decrypts and loads the final payload into a newly created explorer.exe process using Process Hollowing, a method where the memory of a legitimate process is replaced with malicious code.
– PowerShell Script Execution: Once active, LegionLoader downloads and executes a PowerShell script. This script undergoes multiple layers of deobfuscation, including Base64 decoding and XOR decryption, to retrieve and execute another payload.
– Malicious Browser Extension Installation: The final stage involves installing a browser extension named Save to Google Drive, which mimics a legitimate Google service. This extension targets multiple browsers, including Google Chrome, Microsoft Edge, Brave, and Opera, granting itself extensive permissions to access user data such as cookies, browsing history, and even monitoring Bitcoin activities. The stolen data is then exfiltrated to the attackers.
Exploitation of Cloudflare Turnstile:
Cloudflare Turnstile is a verification tool designed to replace traditional CAPTCHAs, aiming to confirm web visitors are real without the need for intrusive puzzles. In this campaign, attackers have exploited Turnstile by integrating it into their redirection chain, adding a layer of legitimacy to their malicious activities. This exploitation underscores the need for vigilance, even when encountering seemingly trustworthy verification systems.
Indicators of Compromise:
Netskope Threat Labs has identified several indicators associated with this campaign, including the use of fake CAPTCHAs, Cloudflare Turnstile, and the distribution of MSI files leading to LegionLoader installation. They have reported the malicious URLs to various web hosting services and provided proactive coverage against this threat through their Advanced Threat Protection.
Recommendations:
– Exercise Caution with CAPTCHAs and Browser Notifications: Users should be wary of CAPTCHAs and browser notification requests, especially when downloading files from unknown sources.
– Verify the Legitimacy of Downloads: Before downloading and executing files, ensure they originate from reputable sources.
– Implement Robust Cybersecurity Measures: Utilize advanced threat protection solutions to detect and prevent such sophisticated attacks.
This campaign highlights the evolving tactics of cybercriminals who exploit everyday online activities, such as document searches, to distribute malware. Continuous monitoring and adherence to cybersecurity best practices are essential to mitigate such threats.