In a recent cyber espionage campaign, the threat actor known as Marbled Dust has been exploiting a zero-day vulnerability in Output Messenger to target Kurdish military entities in Iraq. This sophisticated attack, identified by Microsoft Threat Intelligence, has been active since April 2024 and involves the deployment of malicious payloads to collect sensitive user data across victim networks.
Understanding the Zero-Day Vulnerability
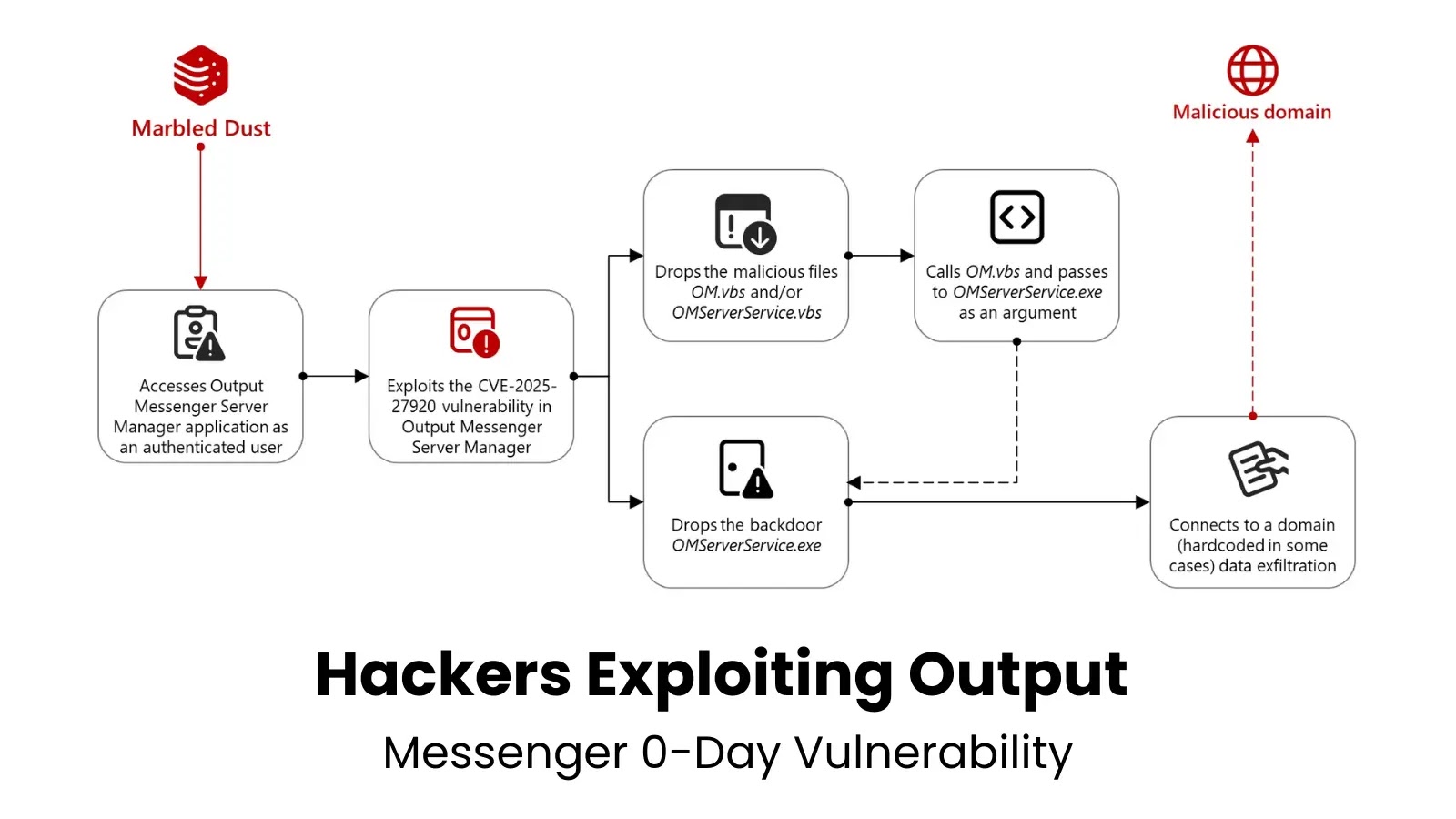
Output Messenger is a multiplatform chat software widely used by organizations for internal communications. The identified vulnerability, designated as CVE-2025-27920, is a directory traversal flaw that allows authenticated users to upload malicious files to the server’s startup directory. This vulnerability enables attackers to execute arbitrary code on the server, leading to potential data breaches and system compromises.
Upon discovering this vulnerability, Microsoft promptly notified Srimax, the developer of Output Messenger. Srimax responded swiftly by releasing patches to address the issue, underscoring the importance of timely software updates in maintaining cybersecurity.
Marbled Dust’s Targeting Strategy
Marbled Dust has a history of targeting entities that counter the interests of the Turkish government. In this campaign, they have specifically focused on users associated with Kurdish military operations in Iraq. The successful exploitation of a zero-day vulnerability indicates an increase in the group’s technical sophistication and suggests that their operational goals have become more urgent.
Microsoft’s researchers believe that Marbled Dust conducts reconnaissance to identify whether potential targets use Output Messenger before launching their attacks. While the exact method of obtaining initial authentication credentials remains unclear, it is suspected that the group leverages DNS hijacking or typo-squatted domains to intercept and reuse legitimate credentials.
The Attack Chain
Once Marbled Dust gains authenticated access to the Output Messenger Server Manager, they exploit the directory traversal vulnerability to upload malicious files to the server’s startup folder. These files include OMServerService.vbs and OM.vbs, along with OMServerService.exe placed in the Users/public/videos directory.
These malicious files work together to establish a GoLang backdoor that connects to a command-and-control domain (api.wordinfos[.]com) for further instructions and data exfiltration. On client machines, another backdoor called OMClientService.exe is installed alongside the legitimate Output Messenger application. This malware communicates with the same command-and-control infrastructure, sending identifying information about the victim and executing commands received from the attackers.
In at least one observed case, the attackers used the command-line version of PuTTY (plink) to exfiltrate data collected in RAR archives. This method allows for the discreet transfer of large amounts of data, further compromising the security of the targeted organizations.
Implications and Recommendations
The exploitation of Output Messenger’s zero-day vulnerability by Marbled Dust highlights the evolving tactics of cyber espionage groups and the critical importance of cybersecurity vigilance. By gaining access to the Output Messenger server, attackers can indiscriminately access the communications of every user, steal sensitive data, and impersonate users.
To mitigate the threat, Microsoft recommends updating Output Messenger to version 2.0.63 for Windows clients and version 2.0.62 for servers. Additionally, organizations should enable cloud-delivered protection in their antivirus software to detect and prevent such sophisticated attacks.
This incident serves as a stark reminder of the importance of regular software updates, vigilant monitoring of network activity, and the implementation of robust cybersecurity measures to protect against increasingly sophisticated cyber threats.