A significant security vulnerability has been identified in Commvault’s Command Center, potentially allowing unauthorized remote code execution on affected systems. This flaw, designated as CVE-2025-34028, has been assigned a CVSS score of 9.0 out of 10, indicating its critical severity.
Commvault disclosed the vulnerability on April 17, 2025, stating that it could lead to a complete compromise of the Command Center environment. The issue affects the 11.38 Innovation Release, specifically versions 11.38.0 through 11.38.19. The company has addressed the flaw in versions 11.38.20 and 11.38.25.
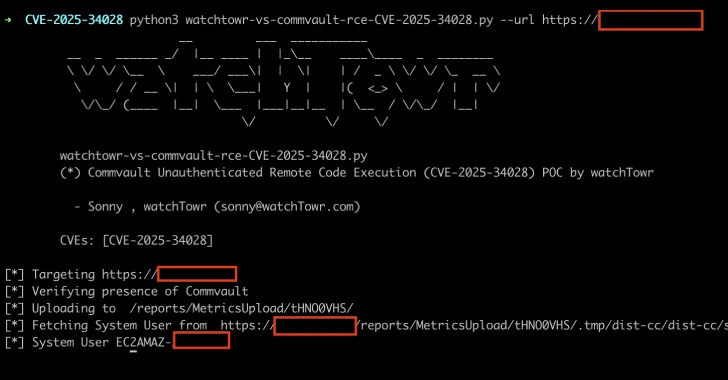
Security researcher Sonny Macdonald from watchTowr Labs discovered and reported the vulnerability on April 7, 2025. The flaw resides in the deployWebpackage.do endpoint, which lacks proper filtering of host communications, leading to a pre-authenticated Server-Side Request Forgery (SSRF). This SSRF can be exploited to execute arbitrary code by manipulating ZIP archive files containing malicious .JSP files.
The exploitation process involves sending an HTTP request to the vulnerable endpoint, causing the Commvault instance to retrieve and unzip a malicious ZIP file from an external server. By leveraging directory traversal techniques, an attacker can place a shell in a publicly accessible directory and execute it, thereby gaining control over the system.
To assist organizations in identifying vulnerable instances, watchTowr has developed a Detection Artefact Generator. Given the active exploitation of similar vulnerabilities in backup and replication software, it is imperative for users to apply the necessary updates promptly to mitigate potential threats.