Cybersecurity researchers have recently identified three significant security vulnerabilities within the Rack Ruby web server interface. These flaws, if exploited, could allow attackers to access unauthorized files, inject malicious data, and manipulate server logs under specific conditions.
Overview of the Vulnerabilities:
The vulnerabilities, reported by cybersecurity firm OPSWAT, are as follows:
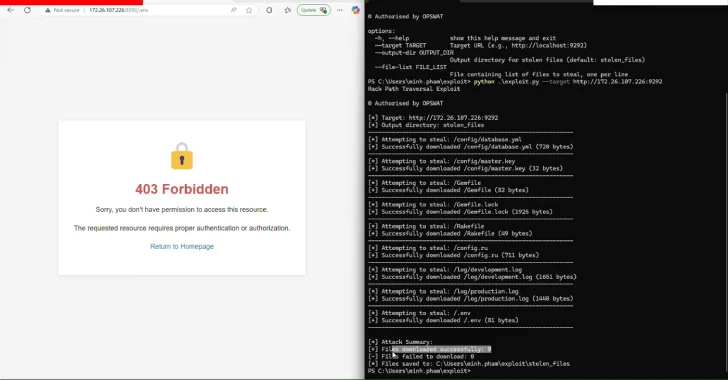
1. CVE-2025-27610 (CVSS score: 7.5): This path traversal vulnerability enables attackers to access all files within the specified root directory, provided they can determine the file paths.
2. CVE-2025-27111 (CVSS score: 6.9): This flaw involves improper neutralization of carriage return line feeds (CRLF) sequences and inadequate output neutralization for logs, allowing attackers to manipulate log entries and distort log files.
3. CVE-2025-25184 (CVSS score: 5.7): Similar to CVE-2025-27111, this vulnerability pertains to improper neutralization of CRLF sequences and output for logs, potentially enabling attackers to inject malicious data and alter log entries.
Potential Impact:
Exploiting these vulnerabilities could have severe consequences, including:
– Data Breaches: Unauthorized access to sensitive information such as configuration files, credentials, and confidential data.
– Log Manipulation: Obscuring attack traces by altering log entries, making it challenging to detect and respond to security incidents.
– Code Injection: Introducing malicious code into the system, potentially leading to further exploitation or system compromise.
Technical Details:
The root cause of these vulnerabilities lies in the Rack::Static middleware, which serves static content like JavaScript, stylesheets, and images. This component fails to properly sanitize user-supplied paths before serving files. Consequently, an attacker can craft specific paths to access files outside the intended static file directory.
Notably, when the `:root` parameter is not explicitly defined, Rack defaults this value to the current working directory (`Dir.pwd`), implicitly designating it as the web root directory for the Rack application. If the `:root` option is undefined or misconfigured relative to the `:urls` option, an unauthenticated attacker could exploit CVE-2025-27610 through path traversal techniques to access sensitive files beyond the intended web directory.
Mitigation Measures:
To address these vulnerabilities, the following steps are recommended:
1. Update Rack::Static: Ensure that your Rack::Static middleware is updated to the latest version where these vulnerabilities have been patched.
2. Review Configuration Settings: Verify that the `:root` parameter is correctly defined and points to a directory containing only publicly accessible files.
3. Remove Rack::Static if Unnecessary: If the middleware is not essential to your application, consider removing it to eliminate potential risks.
Broader Implications:
This disclosure highlights the critical importance of regular security assessments and prompt patch management in web applications. Developers and system administrators must remain vigilant, ensuring that all components are up-to-date and configured securely to prevent unauthorized access and potential data breaches.