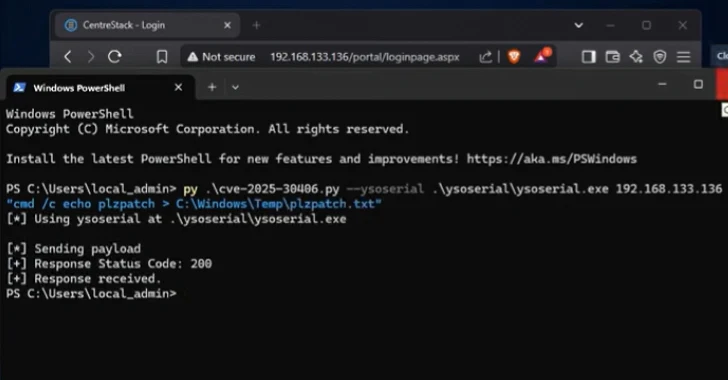
A significant security vulnerability has been identified in Gladinet’s CentreStack and Triofox solutions, leading to active exploitation by malicious actors. This flaw, designated as CVE-2025-30406 with a CVSS score of 9.0, involves the use of hard-coded cryptographic keys, rendering internet-accessible servers susceptible to remote code execution (RCE) attacks.
CentreStack and Triofox are enterprise solutions designed to facilitate secure remote access and collaboration by integrating on-premise file servers with cloud capabilities. They offer features such as seamless integration with existing IT infrastructures, advanced encryption, and robust permission management to enhance operational efficiency and data security.
The vulnerability was addressed in CentreStack version 16.4.10315.56368, released on April 3, 2025. However, reports indicate that the flaw was exploited as a zero-day in March 2025, prior to the release of the patch. The exact methods employed by attackers during this period remain unclear.
Further analysis by cybersecurity firm Huntress revealed that the vulnerability also affects Triofox versions up to 16.4.10317.56372. By default, these versions contain the same hard-coded cryptographic keys in their configuration files, which can be exploited for remote code execution.
Telemetry data from Huntress’s partner base indicates that CentreStack software is installed on approximately 120 endpoints, with seven unique organizations confirmed to have been compromised through this vulnerability. The earliest detected sign of compromise dates back to April 11, 2025, at 16:59:44 UTC.
Attackers have been observed leveraging the flaw to download and sideload a DLL using an encoded PowerShell script. This technique is reminiscent of recent attacks exploiting vulnerabilities in other software, such as CrushFTP. Following the initial compromise, attackers have conducted lateral movement within networks and installed MeshCentral for persistent remote access.
Additionally, attackers have been identified running Impacket PowerShell commands to perform various enumeration tasks and install MeshAgent. The full scope and objectives of these campaigns are currently under investigation.
In light of active exploitation, it is imperative for users of Gladinet CentreStack and Triofox to update their instances to the latest versions immediately to mitigate potential risks. Organizations should also review their systems for signs of compromise and implement additional security measures, such as monitoring for unusual activity and enhancing access controls.