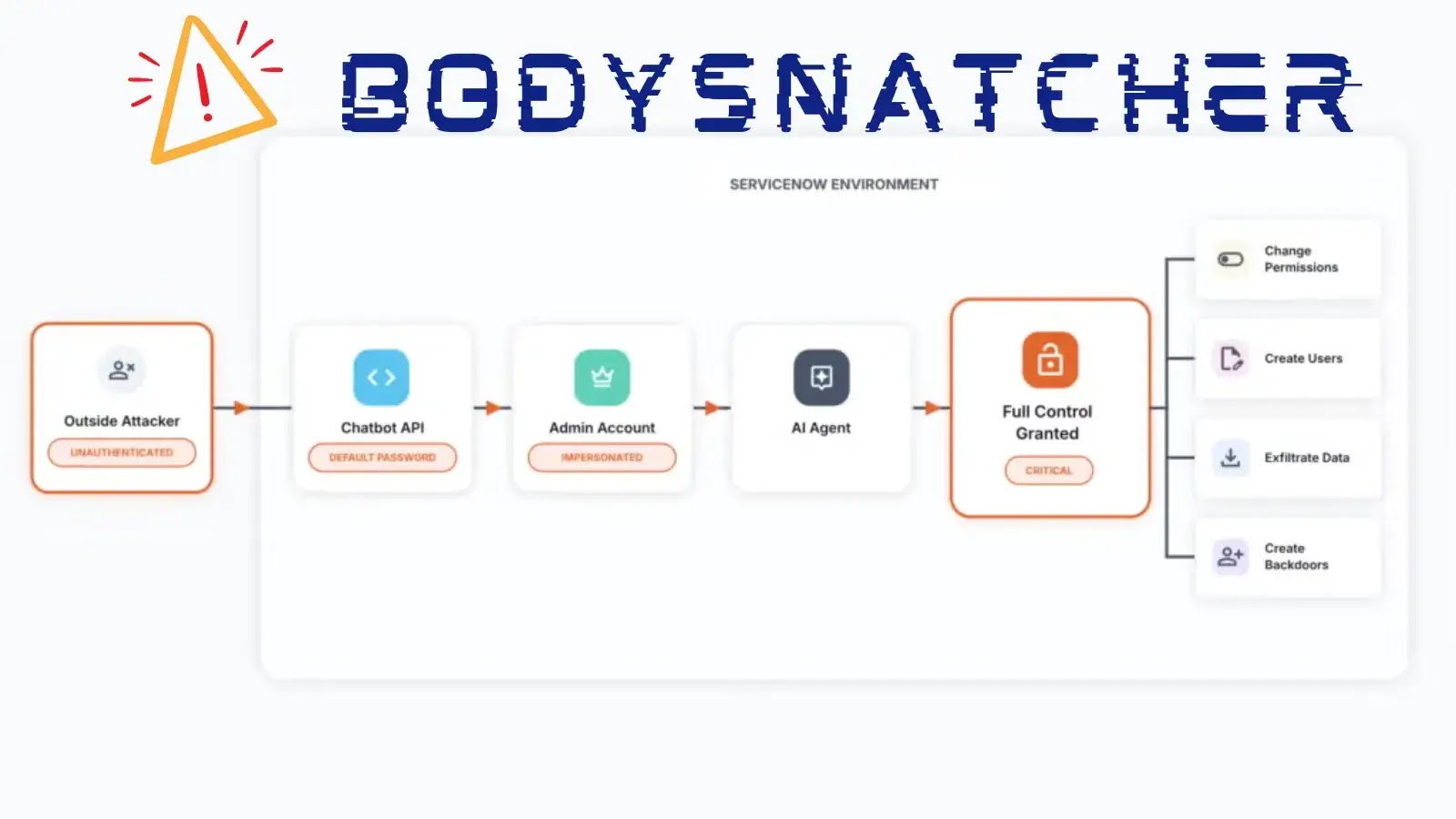
In the wake of the unprecedented cyber-espionage campaign known as Salt Typhoon, the U.S. Congress is actively exploring measures to bolster national cybersecurity defenses. This state-sponsored attack, attributed to Chinese operatives, has compromised major telecommunications providers, including AT&T, Verizon, and Lumen Technologies, granting unauthorized access to sensitive communications and data.
The Salt Typhoon Breach: A Detailed Overview
Salt Typhoon represents one of the most significant cyber intrusions in recent history. The attackers infiltrated the networks of leading U.S. telecom companies, enabling them to geolocate millions of individuals and intercept private communications at will. Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technology, highlighted the severity of the breach, noting that the Chinese operatives gained extensive access to the networks, allowing them to monitor and record phone calls and text messages. ([theregister.com](https://www.theregister.com/2024/12/30/att_verizon_confirm_salt_typhoon_breach/?utm_source=openai))
The intrusion was not limited to a single entity; it affected multiple telecommunications firms, with at least nine companies confirmed to have been compromised. The attackers exploited administrative accounts to gain control over vast segments of the network infrastructure, including over 100,000 routers in one instance. This level of access underscores the sophisticated nature of the attack and the vulnerabilities present in critical infrastructure. ([theregister.com](https://www.theregister.com/2024/12/30/att_verizon_confirm_salt_typhoon_breach/?utm_source=openai))
Congressional Response and Legislative Actions
In response to the Salt Typhoon incident, the U.S. House Committee on Government Reform convened a hearing to assess the implications of the breach and to consider potential legislative measures. The committee, led by Chairman William Timmons (R-SC), is evaluating strategies to enhance the nation’s cybersecurity posture and prevent future incidents of this magnitude.
One of the primary concerns is the adequacy of current cybersecurity protocols within the telecommunications sector. The Federal Communications Commission (FCC) has been urged to implement mandatory cybersecurity risk management plans for telecom carriers. Outgoing FCC Chair Jessica Rosenworcel described the Salt Typhoon attack as a clarion call for necessary security improvements, emphasizing the need to understand the breach’s mechanics, assess its full impact, and take proactive measures to prevent recurrence. ([reuters.com](https://www.reuters.com/technology/cybersecurity/outgoing-fcc-head-says-salt-typhoon-hacking-clarion-call-address-security-issues-2025-01-17/?utm_source=openai))
Additionally, the U.S. Treasury Department has imposed sanctions on individuals and entities linked to the cyberattacks. Notably, Chinese hacker Yin Kecheng and the cybersecurity firm Sichuan Juxinhe Network Technology Co. LTD have been sanctioned for their roles in the breaches, which included compromising Treasury Department workstations and accessing private communications of numerous Americans. ([apnews.com](https://apnews.com/article/745b111710316322c4173822889c276e?utm_source=openai))
Challenges in Rebuilding Trust and Compliance
The aftermath of Salt Typhoon has presented significant challenges for the affected industries. Companies are grappling with regulatory compliance costs, the urgent need to implement enhanced security measures, and potential legal repercussions stemming from the breaches. The public disclosure of these incidents has also damaged corporate reputations and heightened concerns over data privacy. For critical infrastructure sectors, the stakes are particularly high, as failure to address these vulnerabilities could lead to further attacks that destabilize essential services and erode public trust. ([darkreading.com](https://www.darkreading.com/cyberattacks-data-breaches/salt-typhoon-wake-up-call-critical-infrastructure?utm_source=openai))
The complexity of these threats necessitates a multifaceted response. Salt Typhoon has exposed systemic weaknesses, such as outdated systems, inadequate threat detection capabilities, and insufficient identity verification mechanisms. Addressing these issues requires organizations to adopt advanced defense architectures, including zero-trust frameworks and AI-driven monitoring systems, to restore trust and enhance resilience. ([darkreading.com](https://www.darkreading.com/cyberattacks-data-breaches/salt-typhoon-wake-up-call-critical-infrastructure?utm_source=openai))
The Role of Federal Agencies and Public-Private Collaboration
The private sector cannot tackle these challenges alone. Federal agencies like the Cybersecurity and Infrastructure Security Agency (CISA) and the FBI must lead efforts to mitigate threats and assist with recovery. A coordinated response that prioritizes public-private collaboration is critical to preventing future incidents. Real-time threat intelligence sharing between federal agencies and the private sector can enable organizations to detect and respond to advanced threats more effectively. Additionally, federal resources, including technical expertise and funding, can accelerate recovery efforts, helping affected industries address vulnerabilities and restore operations. ([darkreading.com](https://www.darkreading.com/cyberattacks-data-breaches/salt-typhoon-wake-up-call-critical-infrastructure?utm_source=openai))
However, the recent decision by the Department of Homeland Security (DHS) to terminate all of its advisory committees raises new concerns about the continuity of government-industry collaboration in cybersecurity. Advisory committees have long played a vital role in shaping security policies, facilitating information exchange, and ensuring that private sector concerns are integrated into federal decision-making. Without these advisory bodies, industries may face additional challenges in obtaining clear guidance and streamlined coordination from federal agencies, potentially slowing response efforts in the wake of future cyber incidents. ([darkreading.com](https://www.darkreading.com/cyberattacks-data-breaches/salt-typhoon-wake-up-call-critical-infrastructure?utm_source=openai))
Beyond immediate recovery, long-term strategies must focus on resilience. National cybersecurity training programs and preparedness initiatives can equip organizations with the tools needed to defend against increasingly sophisticated attacks. Federal agencies should work closely with the private sector to strengthen the overall cybersecurity posture, ensuring a robust framework that can withstand evolving threats. Despite the DHS’s restructuring, it is imperative that new channels for collaboration be established to maintain a strong national cybersecurity defense. ([darkreading.com](https://www.darkreading.com/cyberattacks-data-breaches/salt-typhoon-wake-up-call-critical-infrastructure?utm_source=openai))
Conclusion
The Salt Typhoon cyberattacks have served as a stark reminder of the vulnerabilities present in critical infrastructure and the need for a comprehensive, coordinated response. As Congress deliberates on potential legislative actions, the emphasis must be on enhancing cybersecurity protocols, fostering public-private collaboration, and implementing proactive measures to safeguard national security. The lessons learned from this incident should inform future strategies to prevent similar breaches and to build a more resilient digital infrastructure.